Supercharged by AI, deepfakes have rapidly become a critical security threat, exploiting human trust to bypass traditional security measures. Beyond raising the risk of financial losses and data theft, a successful deepfake attack can erode credibility, unsettle shareholders, and trigger regulatory consequences. This research will help CIOs and security leaders identify vulnerabilities, evaluate risks, and design a proactive, resilient deepfake defense program.
Because deepfakes target humans rather than systems, technical controls alone are not enough to stop them. CIOs and security leaders must identify specific deepfake threats, understand their potential impact, and embed a zero trust mindset into every interaction. Only then can your organization’s people, processes, and technology work together to reduce deepfakes from a looming threat to a manageable risk.
1. People are the best defense.
Trained employees are the strongest safeguard against deepfakes. When staff instinctively recognize red flags and feel empowered to question instructions, they can stop attacks before damage occurs.
2. Processes generate confidence.
Zero trust must extend beyond networks and systems to encompass all human communications – no voice, video, or message should be trusted without verification. Clear workflows such as secondary confirmations, code words, or out-of-band checks reduce human error and make verification a default behavior.
3. Technology supports vigilance.
AI deepfakes evolve too quickly for detection tools to be effective on their own. Organizations should instead use them to amplify human vigilance by flagging anomalies and supporting verification steps.
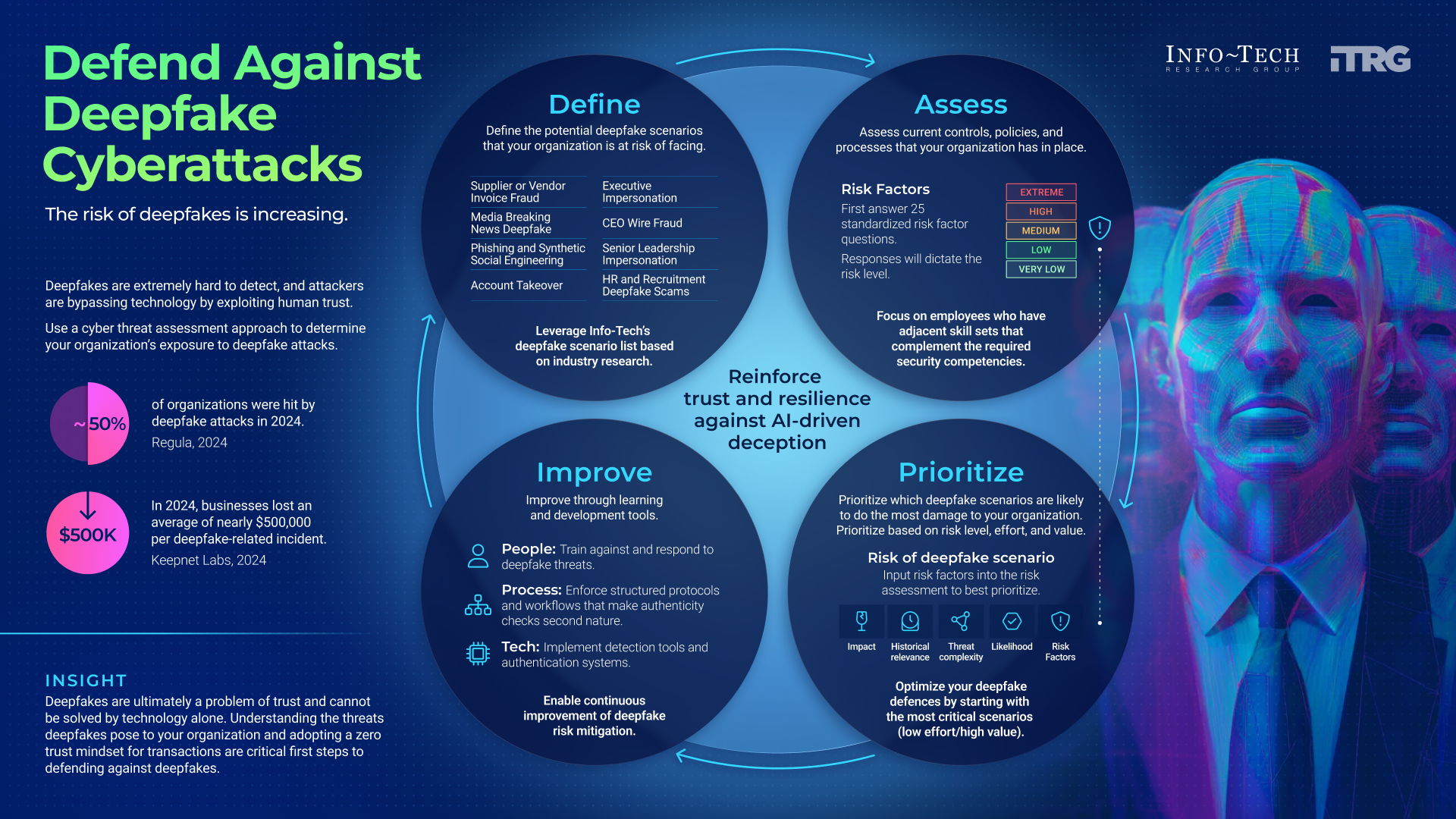
Use this step-by-step framework to build a holistic deepfake defense rooted in zero trust
Info-Tech’s practical research offers an actionable framework and comprehensive threat assessment tool to help you design a deepfake defense strategy that strengthens resilience and preserves trust in digital communication. Use this step-by-step approach to:
- Identify deepfake threat scenarios by understanding and preparing for specific threats to create precise and targeted defenses.
- Assess your organization’s risk factors through a structured risk analysis to determine your level of preparedness for specific risk scenarios.
- Prioritize relevant deepfake scenarios by their potential organizational impact, weighting them according to historical relevance and threat complexity.
Defend Against Deepfake Cyberattacks
Use a cyberthreat assessment approach to determine your organization's exposure to deepfake attacks.
Analyst perspective
Zero trust programs built on people and process are essential to defend against deepfakes.
Deepfakes have quickly shifted from curiosity to critical enterprise threat. They allow attackers to convincingly impersonate executives, vendors, or colleagues, bypassing traditional defenses and targeting the human trust that underpins communication. A single deepfake can cause financial fraud, expose sensitive information, or erode confidence in leadership. CIOs, CISOs, and CSOs now face an urgent and unfamiliar challenge.
Existing frameworks acknowledge deepfakes but provide little practical direction. Detection tools are emerging, but they are inconsistent and cannot serve as a silver bullet. This is not just a technical problem; it is a business resilience issue. Organizations must start by understanding where they are most exposed, which processes, individuals, and transactions are vulnerable, and what the impact would be if a deepfake were successful.
Our perspective is that effective defense requires a holistic, business-centric program built on people, process, and technology. By embedding verification practices into daily workflows, training staff to recognize threats, and strategically layering in detection technology, organizations can restore confidence in communication. Info-Tech's Deepfake Threat Assessment Tool enables leaders to map and prioritize potential risks, providing the clarity needed to design defenses that protect both assets and reputation.

Alexander Toti
Research Analyst, Security & Privacy
Info-Tech Research Group
Executive summary
Your Challenge
Deepfakes now allow attackers to impersonate executives, vendors, or employees with unsettling accuracy, creating a serious threat to enterprise communication.
A single successful attack can result in fraudulent transfers, exposure of sensitive data, or damage to customer trust that takes years to rebuild.
CIOs, CISOs, and CSOs must ensure communications remain trustworthy in an environment where traditional signals of authenticity no longer apply.
It is crucial to understand what deepfake scenarios are likely to happen and be prepared to defend against them.
Common Obstacles
Current cybersecurity frameworks and standards acknowledge deepfakes but provide little actionable guidance, leaving leaders without a clear path forward.
Detection technologies are emerging but remain inconsistent, resource-intensive, and costly, which makes adoption difficult for many organizations. These focus more on being reactive rather than proactive.
Human behavior compounds the risk, as employees tend to trust familiar voices and faces while resisting verification steps that they feel add friction to everyday work.
Info-Tech's Approach
The Deepfake Threat Assessment Tool helps organizations map their unique exposure by scoring likelihood and impact across common attack scenarios.
Info-Tech's framework builds defenses across people, process, and technology, ensuring that verification practices, employee training, and detection tools work together.
The goal is to give CIOs, CISOs, and CSOs a clear, business-centric strategy that strengthens resilience and preserves trust in digital communication. Leaders should understand and be prepared for the risks coming their way.
Info-Tech Insight
Deepfakes are ultimately a problem of trust and cannot be solved by technology alone. Understanding the cyberthreats posed by deepfakes to your organization and adopting a zero trust mindset during transactions are critical first steps to defending against them.
Your challenge
As a security leader, you need to preserve trust in every communication channel as deepfakes erode traditional signals of authenticity.
- Deepfakes now allow attackers to impersonate executives, vendors, or employees with unsettling accuracy, creating a serious threat to enterprise communication.
- A single successful attack can result in fraudulent transfers, exposure of sensitive data, or damage to customer trust that takes years to rebuild.
- For CIOs, CISOs, and CSOs, the challenge is ensuring communications remain trustworthy in an environment where traditional signals of authenticity no longer apply.
- It is crucial to understand what deepfake scenarios are likely to happen – and to be prepared to defend against them.
49% |
Nearly half (49%) of global businesses have already encountered deepfake scams (Regula, 2024). |
It takes as little as ten seconds of audio to clone a person's voice convincingly (OWASP, 2024). |
10 seconds! |
30% |
Only ~30% of organizations are fully aware of the threat of deepfakes (Regula, 2024). |
Deepfakes are a costly threat
Deepfakes have moved from novelty to enterprise risk. Nearly half of all organizations reported a deepfake attack in the past year (Regula, 2024), and global losses surpassed US$200 million in Q1 2025 alone (Fordham Now, 2025). The speed of adoption by criminals shows that this is no longer a hypothetical threat but an urgent reality for CIOs, CISOs, and CSOs.
The financial impact of a single incident can be severe. Deepfake voice scams cost organizations an average of US$600,000, with some cases exceeding US$25 million from one fraudulent transaction (Business Wire, 2024). For leaders, the question is not whether their organization will be targeted but whether they are prepared when it happens.
The damage extends beyond money. Deepfakes erode trust in leadership communications, expose organizations to regulatory penalties, and cause reputational harm that can take years to repair. With deepfakes now accounting for 6.5% of all fraud attempts (Signicat, 2025), organizations that fail to prepare risk losing far more than just dollars – they risk credibility.
62% of organizations hit by deepfake attacks in 2025 (Regula, 2024).
US$600,000 is the average loss per incident – some cases exceed US$25 million
(Business Wire, 2024).
The risk of deepfakes is high
Committing a deepfake attack is getting easier
60 seconds
As little as 60 seconds of recorded audio and video is all attackers need to create realistic deepfake clones (NPR, 2023).
Deepfakes are extremely hard to detect, and attackers are bypassing technology by exploiting human trust.
Blueprint deliverable
Use this blueprint to identify potential deepfake threats to the organization, assess your current controls, and rank the overall risk of potential scenarios.
Key deliverable:
Deepfake Threat Assessment Tool
Use the Deepfake Threat Assessment Tool to:
- Identify potential deepfake scenarios that will impact your organization.
- Assess your current processes and preparation for potential attacks.
- Rank the overall risk of potential deepfake scenarios and pave the way for the next steps of risk mitigation.
Insight summary
Deepfakes are a problem of trust
Deepfakes are ultimately a problem of trust and cannot be solved by technology alone. Understanding the cyberthreats posed by deepfakes to your organization and adopting a zero trust mindset during transactions are critical first steps to defending against them.
People are the first line of defense
Trained employees are the strongest safeguard. When staff know how to spot red flags such as unusual channels or urgent secrecy, they can stop attacks before damage occurs. A culture that supports questioning instructions gives people the confidence to act as defenders rather than targets.
Processes generate confidence
Zero trust must extend beyond networks and systems to human communication. No voice, video, or message should be assumed authentic without verification. Clear workflows such as secondary confirmations, code words, or out-of-band checks reduce human error under pressure and make verification a default behavior.
Technology supports vigilance
Detection tools add value but cannot be relied on alone. AI deepfakes evolve too quickly for technology to solve the problem outright. When used correctly, tools amplify human vigilance by flagging anomalies and supporting verification steps.
You have to earn the trust
Organizations that embed verification into every interaction will transform deepfakes from a looming threat into a manageable risk.
Case study: Ferrari – stopping a deepfake CEO scam
Trained and prepared employees on the frontline are the best defense against deepfakes.
Challenge
In July 2024, Ferrari faced a deepfake attempt targeting one of its senior executives. Attackers used WhatsApp voice messages that convincingly mimicked CEO Benedetto Vigna, pressing for secrecy around a supposed acquisition. The goal was to manipulate the executive into compliance and bypass normal checks.
Solution
Instead of complying, the executive recognized several red flags: the request came from an unfamiliar number, the tone of the message felt slightly mechanical, and the urgency was unusual. Drawing on prior awareness training, the executive asked a personal verification question about a book the real CEO had recommended. The impostor could not answer, and the executive ended the call immediately.
Results
No sensitive information was shared and the scheme collapsed without financial or reputational loss. This case shows how a vigilant, empowered employee can be the decisive line of defense against sophisticated scams. It reinforces the importance of training, clear verification protocols, and encouraging staff to trust their instincts when something feels off.
Blueprint benefits
IT Benefits |
Business Benefits |
|---|---|
|
|
Deepfake risk assessment checklist
Follow this checklist to ensure you are creating a successful risk assessment for your organization.
Download the Deepfake Threat Assessment Tool
- Leverage Info-Tech's list of deepfake scenarios along with their attack vectors and descriptions to decide on which scenarios are applicable to your organization.
- Assess your organization's risk factors and answer each question based on your organization's current controls and processes.
- Choose whether to adjust or leave predetermined weightings and analyze which scenarios pose the highest risk to your organization.
- Enter these scenarios into your risk register and plan to adjust training, controls, and processes to mitigate the threat of these scenarios.
What are deepfakes?
- A deepfake is an image, video, or audio recording that has been synthetically altered using AI to make it appear real, even when it is not.
- The most common deepfakes today are video impersonations – where a person's face or voice is swapped with another's – often used in scams, misinformation, or manipulated media.
- Deepfakes are created using AI techniques such as generative adversarial networks (GANs), which learn from real images and voices to generate lifelike synthetic content.
- While some are used for harmless entertainment or research, malicious deepfakes can enable fraud, reputational damage, and disinformation, undermining public trust.
"The threat of deepfakes and synthetic media comes not from the technology used to create it, but from people's natural inclination to believe what they see" (Department of Homeland Security, 2022).
Why a risk assessment?
A structured assessment provides the clarity needed to build targeted, cost-effective defenses.
Identifies Where You're Most Exposed
Deepfake risks vary by organization – a risk assessment highlights which roles, communication channels, or processes are most vulnerable to impersonation or manipulation.
Prioritizes Effort and Investment
By scoring likelihood and impact, leaders can focus resources on the most critical deepfake scenarios instead of spreading defenses too thin.
Aligns People, Process, and Technology
The assessment bridges technical and human factors, ensuring that awareness training, verification workflows, and detection tools reinforce each other.
Builds Executive Confidence and Accountability
Documented risks and mitigation priorities support governance discussions, budget decisions, and ongoing reporting to the board or risk committee.
Info-Tech Insight
You can't defend what you haven't defined. A deepfake risk assessment transforms uncertainty into actionable insight.
Value of this research
- The Deepfake Threat Assessment Toolhelps organizations systematically evaluate where they are most exposed to AI-driven impersonation threats. Its value lies in creating structure, consistency, and visibility – transforming deepfake risk management from a reactive discussion into a measurable, repeatable process.
- The tool streamlines scenario identification, risk scoring, and prioritization, helping leaders focus resources where they matter most.
- Value can be measured through efficiency gains (faster completion and clearer prioritization), improved decision confidence (stronger executive alignment on risks), and risk reduction outcomes (fewer incidents or faster response times).
- By proactively mitigating high-impact deepfake risks, organizations also avoid the potential financial losses, operational disruptions, and reputational damage that can result from a successful impersonation attack.
Reassessing periodically with the tool allows security teams to track maturity and demonstrate continuous improvement in trust resilience over time. - These outcomes can be quantified through KPIs:
- Efficiency gains, measured by reduced average incident response time and faster completion of risk assessments.
- Decision confidence, tracked through executive alignment surveys or risk committee approval rates.
- Risk reduction outcomes, reflected in fewer deepfake incidents, lower financial losses, and improved mean time to detect (MTTD) and respond (MTTR).
Deepfake threat risk assessment
Identify
Assess
Prioritize
Mitigate
Step 1: Identify deepfake threat scenarios
Addressing the most applicable deepfake scenarios is the first step in defending against deepfake attacks.
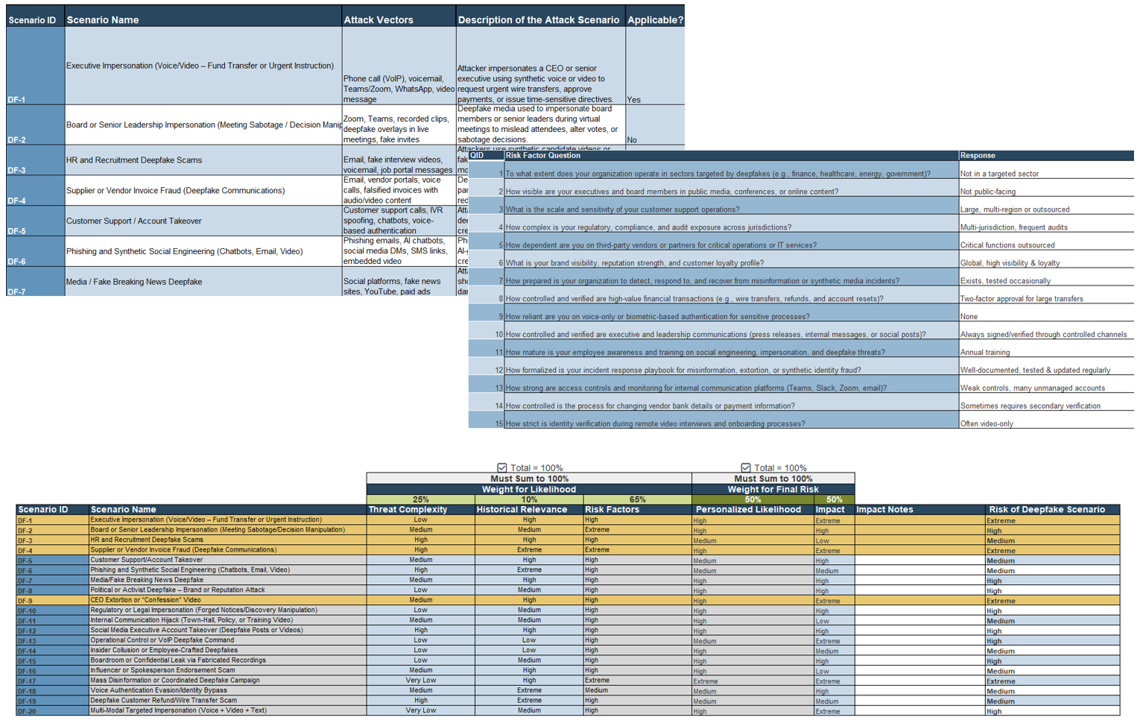
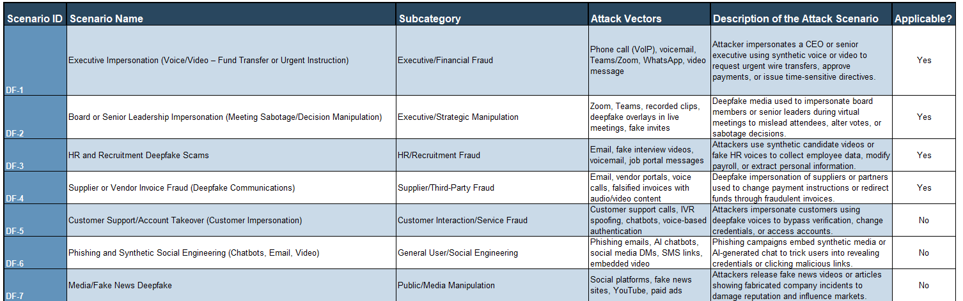
- Info-Tech's Deepfake Threat Assessment Tool provides organizations with the 20 most applicable deepfake scenarios industry-wide, along with attack vectors and detailed descriptions to help understand which may be a threat to your organization.
- These scenarios have been researched in depth, derived from references such as:
- The Open Web Application Security Project (OWASP)
- NIST Cybersecurity Framework (CSF)
- Deloitte Insights
- The scenarios include a diverse breadth of topics that are likely to happen based on future AI trends and historical relevance.
Info-Tech Insight
Understand and prepare for specific threats to create more precise and targeted processes to defend against attacks rather than just putting in broad measures.
1.1 Identify applicable deepfake threat scenarios
- Review the list of 20 defined deepfake threat scenarios provided Tab 2.
- Read each scenario's description and associated attack vectors (e.g. voice, video, text).
- Determine which scenarios are applicable to your organization based on operations, exposure, and digital presence.
- Use the drop-down in the "Applicable?" column to mark "Yes" or "No" for each scenario.
Step 2: Assess your organization's risk factors
Answer each question based on your organization's current operations.
- After identifying the scenarios that are most applicable to your organization, the next step is to assess your organization's controls, processes, and general practices. Info-Tech has developed a list of questions to help assess where your organization stands in relation to defending against deepfakes.
- Each risk factor question helps assess the risk level of specific deepfake scenarios happening within your organization. Each question has different levels of answers that determine if your risk of a deepfake attack is Very Low, Low, Medium, High, or Extreme.
- Answering all risk factor questions will help determine the likelihood of certain deepfake scenarios happening. It is important to remember that these answers are not the final answers. After assessing your organization, you may feel the need to address certain risk factors, and if your organization's practices change, your answers will as well.
Info-Tech Insight
By answering these questions, you will understand exactly how well your organization is prepared for these scenarios, leading to better preparation to improve processes and employee readiness.
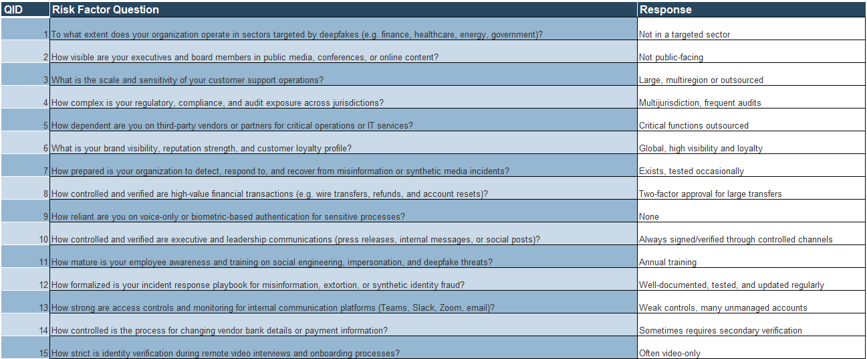
1.2 Assess organizational risk factors
- Review the 25 predefined risk factor questions on Tab 3.
- Select an appropriate response from the drop-down for each question based on your organization's current controls.
- Each response will automatically generate a numerical risk score from 1-5.
- Ensure all responses are completed to produce an accurate organizational risk profile.
Step 3: Prioritize relevant deepfake scenarios
Prioritize which deepfake scenarios pose the largest risk to the organization.
- After completing the risk factor questions, prioritize the scenarios based on their risk to the organization.
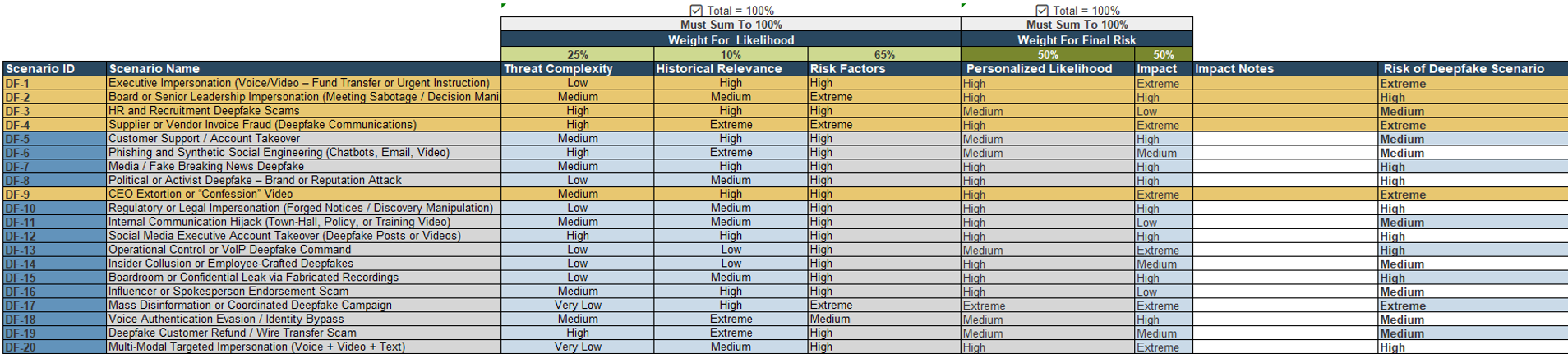
- On Tab 4, Risk Assessment, you will see each scenario's historical relevance and threat complexity. Info-Tech has predetermined these factors, but you can edit them if you need to. After selecting the weightings of the historical relevance and threat complexity, you get a personalized likelihood of the deepfake attack happening to your organization.
- You can then determine the impact of the scenario on your organization. Use the "Weight for Final Risk" column to choose how much the risk is influenced by the likelihood and impact of the scenario.
- This will provide you with the final risk of the specific deepfake scenarios so you can prioritize which scenarios you would like to focus on based on their level of risk to the organization.
Info-Tech Insight
Not all deepfake threats are equal. Prioritize based on business impact, not fear. Structured weighting of historical relevance and threat complexity turns subjective concern into objective, defensible prioritization.

 Assess and Manage Security Risks
Assess and Manage Security Risks
 Assess Your Cybersecurity Insurance Policy
Assess Your Cybersecurity Insurance Policy
 Achieve Digital Resilience by Managing Digital Risk
Achieve Digital Resilience by Managing Digital Risk
 Prevent Data Loss Across Cloud and Hybrid Environments
Prevent Data Loss Across Cloud and Hybrid Environments
 Build an IT Risk Management Program
Build an IT Risk Management Program
 Develop and Deploy Security Policies
Develop and Deploy Security Policies
 Fast Track Your GDPR Compliance Efforts
Fast Track Your GDPR Compliance Efforts
 Build a Security Compliance Program
Build a Security Compliance Program
 Embed Privacy and Security Culture Within Your Organization
Embed Privacy and Security Culture Within Your Organization
 Establish Effective Security Governance & Management
Establish Effective Security Governance & Management
 Improve Security Governance With a Security Steering Committee
Improve Security Governance With a Security Steering Committee
 Develop Necessary Documentation for GDPR Compliance
Develop Necessary Documentation for GDPR Compliance
 Reduce and Manage Your Organization’s Insider Threat Risk
Reduce and Manage Your Organization’s Insider Threat Risk
 Satisfy Customer Requirements for Information Security
Satisfy Customer Requirements for Information Security
 Master M&A Cybersecurity Due Diligence
Master M&A Cybersecurity Due Diligence
 Integrate IT Risk Into Enterprise Risk
Integrate IT Risk Into Enterprise Risk
 Present Security to Executive Stakeholders
Present Security to Executive Stakeholders
 Deliver Customer Value by Building Digital Trust
Deliver Customer Value by Building Digital Trust
 Address Security and Privacy Risks for Generative AI
Address Security and Privacy Risks for Generative AI
 Protect Your Organization's Online Reputation
Protect Your Organization's Online Reputation
 Develop an AI Compliance Strategy
Develop an AI Compliance Strategy
 Get Started With AI Red-Teaming
Get Started With AI Red-Teaming
 Achieve CMMC Compliance Effectively
Achieve CMMC Compliance Effectively
 Building Info-Tech’s Chatbot
Building Info-Tech’s Chatbot
 Building the Road to Governing Digital Intelligence
Building the Road to Governing Digital Intelligence
 An Operational Framework for Rolling Out AI
An Operational Framework for Rolling Out AI
 Discover and Classify Your Data
Discover and Classify Your Data
 Defend Against Deepfake Cyberattacks
Defend Against Deepfake Cyberattacks