Fortify against emerging and advanced threats in an unpredictable era.
Security leaders head into 2026 with the ground constantly shifting beneath them. They’re grappling with advanced AI threats, a volatile global economy, geopolitical tension, and regulatory compliance changes. To navigate this unpredictability, they must foster a resilience mindset across the entire organization. Security must go above and beyond responding to threats. Now, it’s all about supporting secure innovation, even as IT budgets and spending face rising scrutiny in the year to come.
Our Security Priorities 2026 report unveils five initiatives to help transform your security program in the year ahead, then breaks them down into actionable recommendations to translate strategy into real results.
Five key security priorities for 2026
This report reveals critical findings based on data from the Info-Tech Future of IT 2026 survey plus insightful interviews with 20 security matter experts. It outlines five key priorities to reassess and realign enterprise security in 2026.
1. Strengthen Data Resilience
Protect data against evolving ransomware and AI threats.
AI has armed cyber criminals with a whole new arsenal of powerful weapons. Boost your defenses with a mitigation plan that’s both proactive and adaptive. Build a robust data security program to enhance data governance and develop a resilient response plan to improve business continuity.
2. Enable Scalable Compliance
Manage diverging regulations across geographies.
Data privacy and security regulations are emerging across the globe far too quickly for manual monitoring efforts to keep up. Develop continuous compliance monitoring, leverage automation, and scale your compliance strategy to ensure it meets changing global standards.
3. Reduce Vendor Sprawl
Optimize converging security tool portfolio.
With a challenging economy putting IT budgets under pressure, the opportunity to streamline costs by tackling tool bloat is being prioritized. Discard tools with overlapping capabilities or little organizational value. Focus on interoperability and look for ways to optimize ROI through AI, automation, and integrated security platforms.
4. Minimize Implicit Trust.
Anchor zero trust architecture to identities.
Adoption of zero trust security has been thwarted by legacy systems, whose implicit trust model fails to reverify users or devices after initial login. But don’t let your zero trust efforts fail. Build a core security framework around strong identity management practice. Harness the capabilities of AI and automation to streamline your zero trust efforts and continuously monitor machine identities.
5. Drive Secure Innovation
Transform application security for the agentic AI era.
While agentic AI is turbocharging coding and application development, it’s also introducing new risks that traditional security practices aren’t designed to handle. It’s time to enhance DevSecOps and SDLC initiatives for this new generation of AI-driven development. Give automation a starring role here – but balance it with strategic human oversight.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
10.0/10
Overall Impact
$88,400
Average $ Saved
32
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
Kansanshi Mining PLC
Guided Implementation
10/10
$88,400
32
Security Priorities 2026
INTRODUCTION
Analyst Perspective
Fortifying against emerging and advanced threats during times of uncertainty.
The turn of the century marked the emergence of opportunities and challenges being addressed by innovative technologies. From advanced robotics to extended reality and the implementation of AI, organizations are spearheading initiatives to stay competitive and foster continuous improvement. Throughout the years, new technologies such as generative and agentic AI and the advancement of quantum computing have enabled not only IT but security teams to adopt innovative solutions to modernize their people, process, and technology and address emerging threats. This allowed organizations stay ahead of the technology curve with certainty but also prepare to respond to an evolving threat landscape. However, a quarter of a century in, various global disruptions have impacted organizations who are now navigating uncertainty, affecting digital transformation and security modernization. Financial market volatility has resulted in conservative IT budgets and spending scrutiny on security initiatives. Global changes in regulatory compliance have required stronger data protection across jurisdictions. The impact of global unpredictability has resulted in organizations assessing key security priorities to address continuous shifts in the technology landscape. Over 50% of organizations are prioritizing cybersecurity and data privacy compliance to address regulatory changes, citing the importance of addressing uncertainty from a compliance approach (PwC, 2025).
Furthermore, security threats continue to be a business disruptor with over 60% of organizations indicating a severe impact from a cybersecurity incident over the past year (CompTIA, 2025). These impacts, which have caused the average data breach to increase by 9% to US$10.22M, show the urgency for security teams to adopt an organization-wide, resilient mindset to address continuous threats and efficiently respond to them (“Cost of a Data Breach Report,” IBM, 2025).
In this year’s report, we highlight five important priorities security leaders should focus on. We address the implications of these priorities, the benefits of adopting them, and the risks of neglecting these initiatives in your security strategy. We present applicable use cases where organizations adopted these priorities and show the impact it had on their security program. We also discuss actionable next steps organizations should implement to spearhead the initiatives for each priority and provide resources to support the development of their strategy. Having these priorities in mind will ensure you are addressing the most pressing matters in cybersecurity to not only respond to threats and build a resilient cybersecurity program but also support IT’s moment in adopting a technology-first solution for uncertain times.

Ahmad Jowhar
Senior Research Analyst, Security & Privacy
Info-Tech Research Group
INTRODUCTION
Methodology
We formulated the security priorities through a multifaceted approach to ensure the most important security priorities are addressed.
Info-Tech Research Group derived this year’s security priorities through a comprehensive assessment of our annual Future of IT Survey, which asks IT decision-makers about their responses to emerging IT trends and how their organizations are addressing the opportunities, risks, and implications of emerging technology. Our analysts conducted additional interviews with security experts to learn about their priorities, the current measures they have in place, and what areas they need guidance on.
FUTURE OF IT 2026 SURVEY
We conducted the Future of IT 2026 Survey between May and June 2025. The online survey received 738 responses from IT decision-makers across a broad range of industries and regions, with a focus on North America. Almost six out of ten respondents hold director-level seniority or higher. Each chart included in the report will specify the sample size received for the specific question or respondent group.
PRIORITIES INTERVIEW
Info-Tech analysts conducted in-depth interviews with IT leaders between August and October 2025 to collect insights on priority-making and agenda-setting for 2026. In total, we completed 20 interviews with security subject matter experts, with interviewees from industries such as healthcare, government, and higher education. The interviewees are from various continents and countries and have extensive security experience.
INTRODUCTION
Cybersecurity is a continuing disruptor to the business
Cybersecurity impacts various business factors.
With more organizations leveraging innovative capabilities to stay competitive within their industry, addressing key factors that would disrupt the business is important to improve their oversight on key initiative and investment priorities. Given the increase in financial and operational impact of a cybersecurity incident, coupled with the heightened board-level concern, cybersecurity has shifted from just an IT risk to a strategic risk, requiring mitigation efforts to drive resiliency and gain a competitive advantage.
The impact of cybersecurity on organizations is evident from Info-Tech’s Future of IT Survey: cybersecurity incidents are one of the top three factors organizations believe would disrupt their business within the next 12 months (n=525). The ranking, which measures from least (1) to most disruptive (5), mirrors last year’s finding, where cybersecurity incidents were identified as the third most impactful factor on business operations (behind talent shortage and AI). However, this year’s ranking has “AI and emerging technologies” as the most impactful factor, followed by government-enacted and regulatory changes, which was behind cybersecurity in last year’s report. As organizations continue to view cyberthreats as critical drivers, it’s important to understand the implications across several other business disruptors.
“AI and emerging technologies" has shifted from a key driver to the most impactful factor for business operations. The shift is driven not only by advanced capabilities but also the scale of adoption and the domains where AI is being leveraged. Organizations continue to leverage AI to strengthen their defense operations, with an 11% increase in the use of AI and automation for cybersecurity (“Cost of a Data Breach Report,” IBM, 2025).
The impact of increased government-enacted regulatory changes is further driven by emerging security and privacy laws to protect customer data and critical infrastructure. The consequence of noncompliance is drastic, including both financial and reputational risks. Hence, organizations are prioritizing the navigation of emerging regulations to not only stay competitive but also reduce the likelihood and impact of a security incident. Although cybersecurity incidents were not the most impactful factor identified, the impact is disruptive to various business operations, and strengthening an organization’s security posture will have a significant effect on addressing strategic risks impacting business resilience.
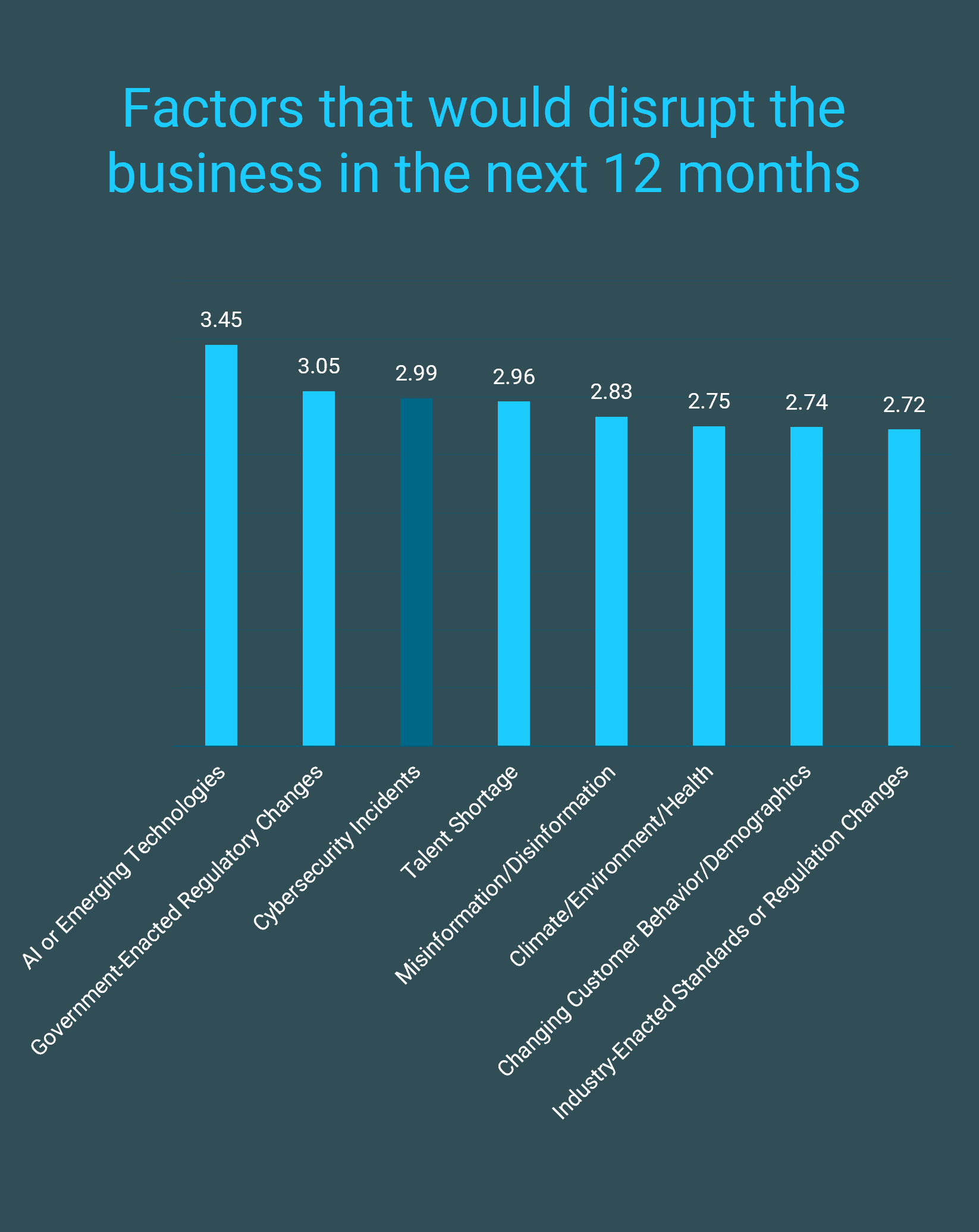
Future of IT 2026 Survey; n=525
INTRODUCTION
Cybersecurity spending is increasing, but where is it being invested?
AI investments are prioritizing strengthening security posture.
As organizations navigate through uncertainties and identify approaches to pursue IT excellence, they prioritize investments into emerging technologies, adopting a technology-first solution. Over 80% of organizations have an AI strategy in place, but only 26% have an AI strategy for IT, signaling the opportunity for innovation to slash an organization’s AI transformation timeline with enhanced capabilities (Future of IT Survey 2026; n=260). With over 40% of organizations prioritizing investments into AI-powered IT service management solutions, a systematic pursuit of transformative IT will improve operational efficiency and cut costs. This will help IT move from reactive issue resolution to proactive service delivery.
As investments into AI-powered solutions increase across the organization, security spend is also being prioritized to ensure the right guardrails are in place to support innovation. With the goal of supporting faster delivery of AI solutions at scale, strengthening security defenses would provide assurance of an organization’s ability to continuously support strategic goals. With over 80% of organizations planning to increase their spending on cybersecurity solutions, it is evident that security is seen as a strategic priority to address the growing threat landscape, tackle compliance and regulatory pressures, and advance digital transformation demands (Future of IT Survey 2026; n=525). Furthermore, security spending has also expanded to proactively modernize an organization’s security posture, leveraging AI-enhanced capabilities to streamline operations. Over 50% of organizations identified cybersecurity solutions as their top investment priorities for AI-powered solutions, signaling the importance of responding to the complexity of emerging threats with sophisticated capabilities (Future of IT Survey 2026; n=385). Moreover, 65% of organizations are already making considerable investments into AI to enhance their cybersecurity defenses, depicting the importance of adopting a predictive, automated, and adaptive security model (Future of IT Survey 2026; n=412). This shift in spending and prioritization shows the importance of cybersecurity as a business enabler, allowing organizations to securely expand into new markets, technologies, and services.
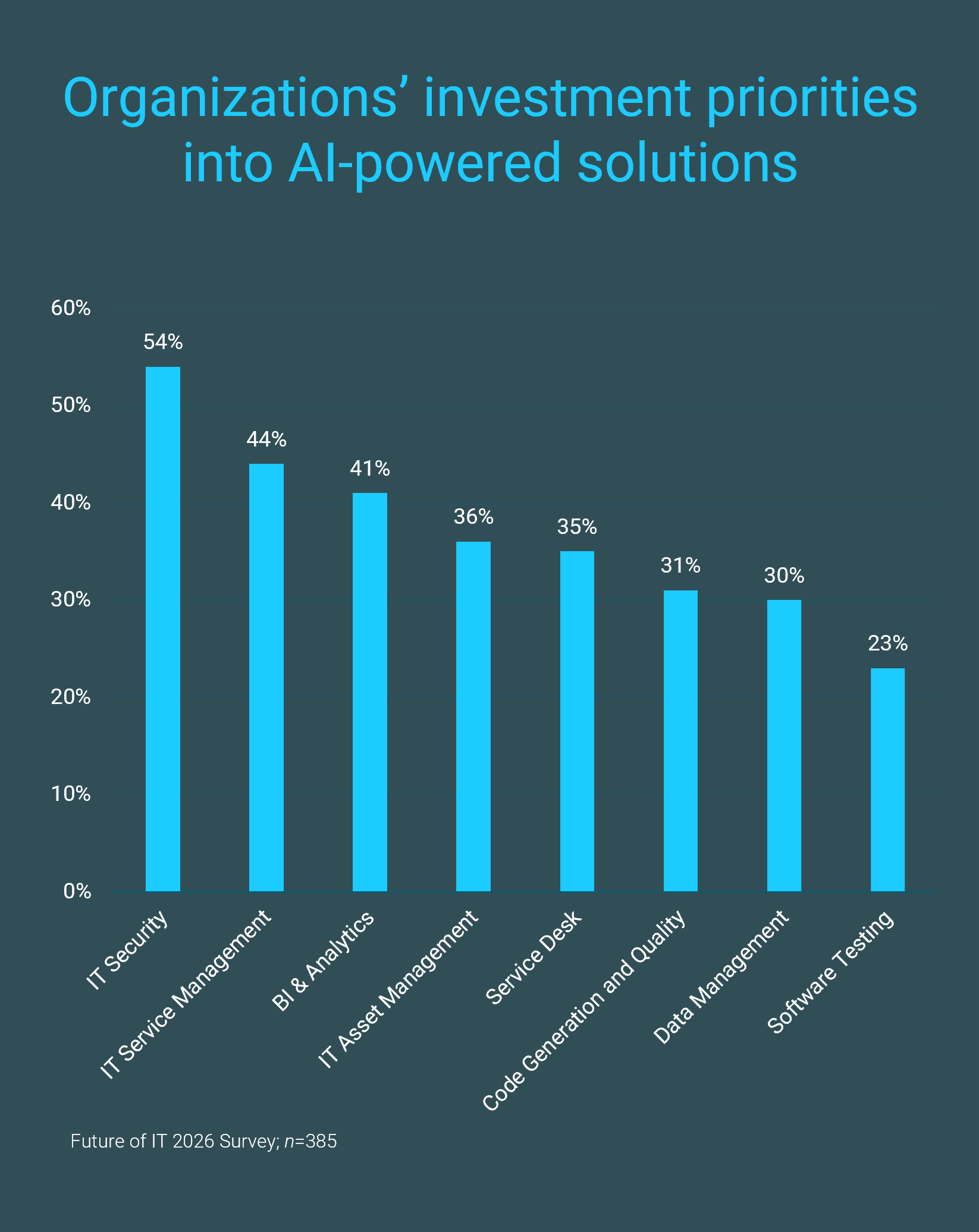
INTRODUCTION
Security & privacy risks influence vendor contracts
Addressing third-party risks at the procurement stage is essential for building a secure and resilient vendor ecosystem.
As organizations continue to expand their technology footprint and partner with vendors to leverage their innovative capabilities, the security risks increase as the attack surface expands with every additional vendor. Issues of data privacy due to poor data security practices could result in regulatory noncompliance as vendors are handling more sensitive data. The lack of appropriate access management controls could also result in credential compromise attacks due to credential misuse and lateral movement. It is obvious why supply chain compromise was the among the top attack vectors, falling behind just phishing attacks (“Cost of a Data Breach Report,” IBM, 2025). Moreover, they took the longest to detect and contain due to the exploited trust that was established between vendors and customers. Even as organizations capitalize on AI-driven innovation, third-party risks are still eminent, with 30% of organizations citing a supply chain compromise as the root cause of an AI security incident, ranking first ahead of model inversion and evasion (“Cost of a Data Breach Report,” IBM, 2025). Given the growing reliance on and increased threat of vendors, organizations are prioritizing mitigation strategies to reduce the likelihood and impact of these incidents.
With supply chain attacks ranking among the top five risks organizations are concerned about, along with ransomware and cyber-enabled fraud, adopting a modernized approach to vendor security is prioritized to address the growing threats (Accenture, 2025). This is demonstrated at the vendor contract level, where organizations are placing more emphasis on the security and privacy of their data as part of their procurement process. This can include right-sizing their vendor security process with a risk-based approach to develop a resource-efficient vendor security assessment or developing an end-to-end security risk management process that includes assessments and risk treatment plans to continuously monitor vendors. With 40% of organizations citing third-party risk management as their second top security priority, this underscores how critical vendor ecosystems have become in strengthening security strategies (Future of IT Survey 2026; n=157). Since over 80% of organizations identify security and privacy as their top vendor risk prior to contracting, additional guardrails and measures should be adopted in the procurement process to ensure appropriate due diligence is established to safeguard your organization’s crown jewels (Future of IT Survey 2026; n=260).
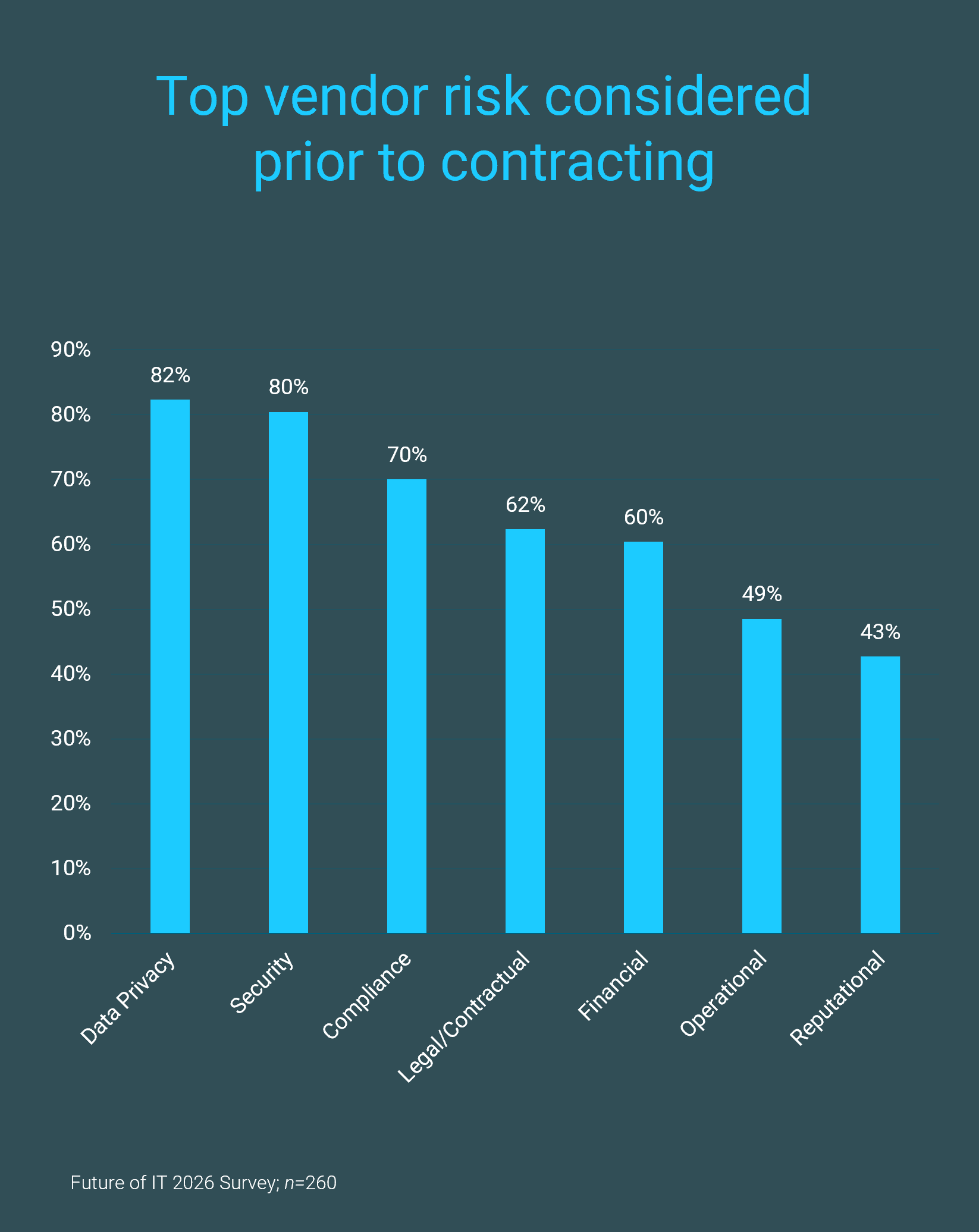
INTRODUCTION
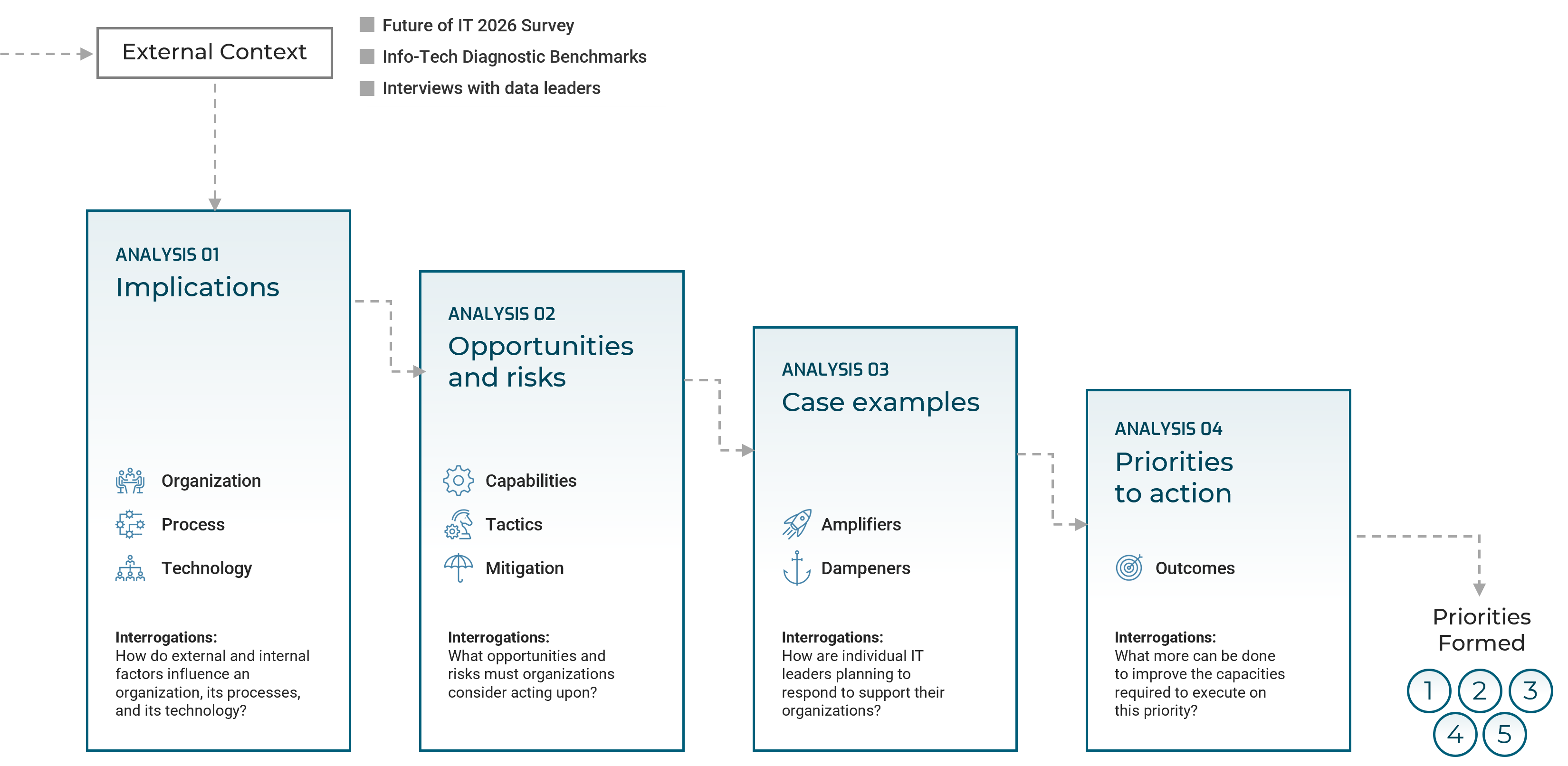
Moving from trends to priorities
Understand the security priorities by analyzing both how security leaders respond to trends in general and how specific security leaders responded in the context of their organization.
CONTEXTUAL INSIGHTS
A priority is created when external factors hold strong synergy with internal goals and an organization responds by committing resources to either avert risk or seize opportunity.
PRIORITY INSIGHTS
For each priority, this report will examine how security leaders are responding to the implications of the external trends impacting their organization. We'll consider the capabilities that play a role in responding to the opportunities and threats and suggest an initiative to improve them. Case studies from security leaders planning for 2026 provide specific insight, and Info-Tech resources are recommended to help clients take action on priorities.
PRIORITY
01
Strengthen Data Resilience
Protect data against evolving ransomware and AI threats
Safeguard your critical assets against growing threats
STRENGTHEN DATA RESILIENCE
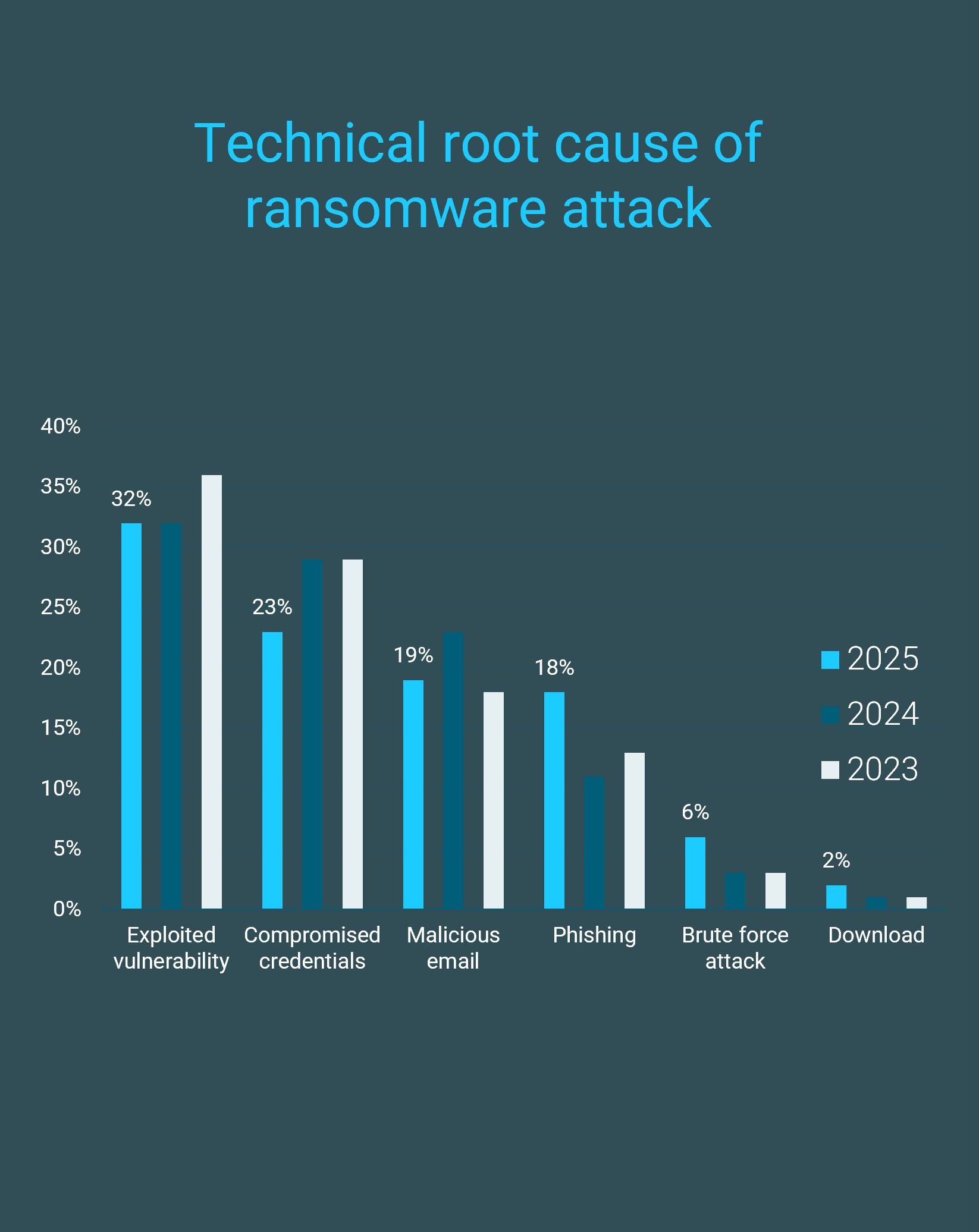
AI-driven threats are amplifying ransomware impact
Security teams face growing challenges defending against AI-enhanced ransomware that prioritizes data exfiltration.
As organizations expand their digital footprint by leveraging emerging technologies, threat actors are following suit to enhance techniques and expand their attack vector. This impacts security teams who are defending against a challenging threat landscape. One threat that has impacted organizations for decades and has been further enhanced due to AI capabilities is ransomware. Techniques have scaled from basic encryption to sophisticated operations that run data-driven extortion campaigns. The average cost of a data breach due to ransomware increased by 4% to US$5.08M (“Cost of a Data Breach Report,” IBM, 2025). Security leaders identify ransomware as the most concerning risk, ahead of supply chain attacks and malicious insiders (Accenture, 2025).
The growing risk of ransomware can be mainly attributed to threat actors leveraging AI capabilities to exploit vulnerabilities. Threat actors are accelerating and intensifying their attack vectors by exploiting known and unknown gaps using advanced tactics (Sophos, 2025). Eighty percent of ransomware attacks leverage AI, which depicts how the growth in AI is actively reshaping ransomware tactics (MIT, 2025). From leveraging AI-based phishing kits, such as voice cloning-as-a-service tools to conduct “vishing” attacks, to AI-enhanced reconnaissance to scan for exploitable systems, AI will reshape the threat landscape by accelerating data theft, reducing time to exfiltration, and enhancing social engineering techniques. The emergence of agentic AI will further the sophistication of adversaries in scaling their attack surface by developing and deploying AI-driven agents to execute different phases of a ransomware attack autonomously. This will shift their approach to an adaptive, on-demand attack engine that will further strain security resources to respond to its threats.
Sophos, 2025
STRENGTHEN DATA RESILIENCE
Shift in ransomware tactics and response plan
Threat actors and organizations are changing their approach to deploying and responding to ransomware attacks.
DATA EXFILTRATION ON THE RISE
Ransomware groups are pivoting from data encryption to data exfiltration and double extortion tactics, enabling adversaries to not only encrypt an organization’s data but also steal to maximize pressure on the organization. The shift is enabled by enhanced capabilities for faster and more targeted data theft and the proliferation of ransomware-as-a-service (RaaS) platforms enabling attackers to monetize stolen data at scale. The shift to exfiltration ransomware resulted in a 29% decrease in data encryption attempts compared to 2024 (Sophos, 2025).
This shift toward data theft as the central component of ransomware operations requires organizations to revamp their ransomware resilience by adapting strategies to the rise of exfiltration. As organizations explore opportunities to maximize productivity and ROI by leveraging their data, adversaries are capitalizing by stealing “crown jewels,” knowing any disclosed sensitive data could have drastic financial and reputational implications.
RANSOMWARE PAYMENTS IN DECLINE
Despite this, the number of ransomware payments and overall recovery costs have decreased. Average ransom demand decreased 34%, while the average cost to recover dropped by 44% (Sophos, 2025). Moreover, organizations are implementing improved incident response plans, stronger backup strategies, and effective detection tools that help speed up the recovery process, with 53% of organizations fully recovering from a ransomware after a week, compared to 35% in 2024 (Sophos, 2025). However, costs of data breaches are still increasing due to regulatory fines and legal costs.
94% of ransomware attacks involve data exfiltration.
BlackFog, 2024
STRENGTHEN DATA RESILIENCE
Strengthen ransomware resilience through a data visibility and incident response plan
Combat emerging ransomware threats with a proactive and adaptive mitigation plan.
To address the shift in ransomware tactics, organizations must implement a resilience mindset. This includes the prioritization of cyber resilience measures such as reliable offline backups, modernized network segmentation tactics to adopt a layered preventive control, and a tested incident response plan to address AI-driven threats.
BUILD A ROBUST DATA CLASSIFICATION PROGRAM
The first step in protecting your data is to understand not only where your data is stored but also the severity level applied to ensure appropriate classification. Adopting a resilience mindset starts from understanding your current data security posture and implementing measures to mature your program that will enable more accurate threat modeling and security control investments.
IMPROVE BUSINESS CONTINUITY THROUGH A RESILIENT RESPONSE PLAN
Strengthening data resiliency requires an effective incident response plan to prepare for and mitigate the impact of a ransomware incident. With over 60% of organizations not paying a ransom, the shift lies in quick recovery to minimize business disruptions (“Cost of a Data Breach Report,” IBM, 2025). This includes integrating incident response with business continuity planning to reduce downtime. Developing table exercises to simulate real-world incidents will help identify and address potential gaps and ensure post-incident reviews are in place. Having the right guardrails in place to effectively respond to ransomware incidents will improve cost savings from reduced downtime, promote faster response time, and enhance confidence, internally and externally, in the organization’s preparedness and resilience.
60% of organizations did not pay a ransom.
“Cost of a Data Breach Report,” IBM, 2025
STRENGTHEN DATA RESILIENCE
Ransomware kill chain
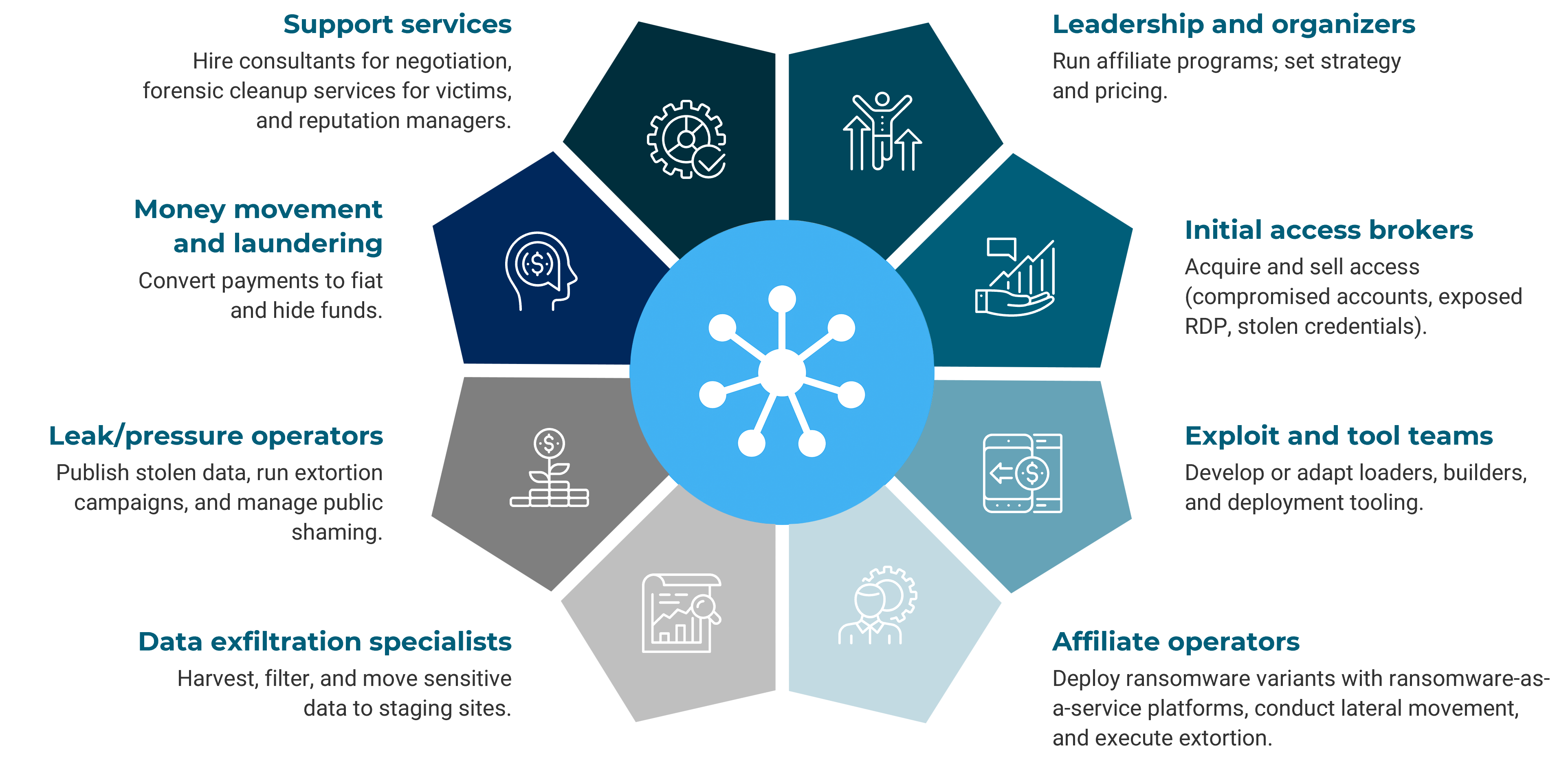
STRENGTHEN DATA RESILIENCE
Mitigation steps

STRENGTHEN DATA RESILIENCE
Opportunities
IMPROVED INCIDENT RESPONSE
A strengthened data resilience strategy with adaptive data governance will improve an organization’s incident response with faster recovery and reduced downtime. Immutable data backups minimize threat actors’ efforts in encrypting or deleting data, mitigating the risks of data encryption attacks. With over 37% and 35% of organizations increasing their investments into data security and incident response efforts respectively, it is evident these initiatives will strengthen preventive measures and build resiliency for faster detection (“Cost of a Data Breach Report,” IBM, 2025).
STRONGER DATA GOVERNANCE
Improving defenses to prevent and detect unauthorized access will apply additional guardrails to protect an organization’s crown jewels. This would be implemented through a robust data classification program that develops and enforces strong data governance and tools, such as DLP solutions to monitor and encrypt data movements. Strong data governance will also limit threat actors’ ability to steal data with appropriate classification tags, which enables DLP solutions to apply tailored controls. With almost 50% of organizations citing data loss prevention as a top priority for 2026, strengthening data security with enhanced data visibility and resilient systems will enable timely restoration of operations, minimize business disruptions and reputational damage, and support innovation through the secure monetization of data (Splunk, 2025).
AMPLIFIERS
Enhanced ransomware resilience;
Alignment with data protection regulations; Improved visibility
46% of organizations have data loss prevention as their top priority for 2026.
Splunk, 2025
STRENGTHEN DATA RESILIENCE
Risks
EXTENDED BUSINESS DISRUPTIONS AND COSTLY RECOVERY
As organizations strive to maintain business operations and minimize downtime, developing a ransomware-resilient response plan should be a priority. The lack of a predefined recovery playbook with regular testing can further exacerbate response efforts and result in business disruptions and reputational damage. Ransomware attacks increased 27% year over year from 2024 (BlackFog, 2025). Ransomware is increasing at scale, targeting not only organizations that store sensitive and proprietary data but also entities such as critical infrastructure that could cause catastrophic damage. Not implementing a mature ransomware response process will have not only a greater effect on data theft but also greater business disruption and escalating recovery costs.
INCREASED EXPOSURE TO AI-DRIVEN THREATS
As 80% of ransomware incidents and 16% of all breaches involved attackers using AI, organizations are challenged to respond to adaptive ransomware tactics. Ransomware attacks are not only increasing in frequency but also in the volume of new strains, with a 65% increase in the number of new variants in 2024 (BlackFog, 2025). This furthers strains security teams as they respond to increased attacks as threat actors continue to leverage AI to proliferate their attack vector for maximum impact.
IMPLICATIONS
Loss of customer trust and reputational damage;
Regulatory and legal fines
27% year-over-year increase in ransomware victims.
BlackFog, 2025
STRENGTHEN DATA RESILIENCE
Leading university established ransomware resilience efforts to address emerging tactics
SITUATION
As one of the leading public universities in southeast England, Canterbury Christ Church University (CCCU) offers academic and professional programs across various fields. Given its growing academic presence, IT and security leaders within the university were prioritizing the management of sensitive data to mitigate the growing risk of ransomware attacks. The higher education sector was an increased target from threat actors given the vast amount of sensitive data that could be exfiltrated for various social, financial, and political gains. Furthermore, the lack of guardrails in place for most universities limited their visibility into sensitive data risks. The lack of data oversight introduced a security gap that could allow threat actors to perform data exfiltration tactics undetected, furthering data breach costs and recovery efforts. CCCU deployed a strategy to strengthen its data protection through a data security and incident response readiness effort.
ACTION
CCCU partnered with data security company Rubrik to support resiliency efforts. Its solutions provided 1) capabilities to proactively alert CCCU on anomalous events, 2) immutable backup and recovery solutions to maintain critical systems, and 3) adaptive data governance controls, which improved visibility into where sensitive or regulated information resides across backups and systems.
This solution enabled CCCU to strengthen its data access and storage practices, reducing the risk of threat actors exfiltrating high-value data. It also improved visibility into CCCU’s data and compliance status and optimized its data handling efforts, reducing backup data search requests from three days to 12 hours. Focusing on strengthening data protection efforts has transformed CCCU’s ransomware defenses, improved its compliance efforts, and enhanced security and operational efficiency.
Key Benefits
Stronger ransomware resilience
Improved visibility and compliance
Enhanced incident response
STRENGTHEN DATA RESILIENCE
Recommended actions
Follow these steps to spearhead your AI governance principles by ensuring the security and privacy of your AI initiatives.
|
Discover and |
Improve Organizational Resilience With a Tabletop Program |
Build Resilience Against Ransomware Attacks |
|---|---|---|
|
|
|
|
FEATURED RESEARCH: |
FEATURED RESEARCH: |
FEATURED RESEARCH: |
PRIORITY
02
Enable Scalable Compliance
Manage diverging regulations across geographies
Effectively navigate the global regulatory landscape
ENABLE SCALABLE COMPLIANCE
Compliance landscape grows more complex each year
Emerging technologies introduce new regulations.
Although the advent of emerging technologies has brought various benefits to organizations, it also introduced various challenges aside from security and privacy risks. The rise of various global compliance standards has increased the complexity of managing and adhering to multiple regulations. Regulations are increasing across jurisdictions, mainly enforcing data privacy laws to address consumer demands to better protect their data. The rapid regulatory changes have also exacerbated organizations’ efforts to track and comply with overlapping requirements globally. Many organizations find it challenging to keep up with the rapid pace of change, citing traditional compliance approaches as insufficient to address modern regulatory amendments. Furthermore, the rise in stricter enforcement and increased fines by jurisdictions has transformed noncompliance into not only a reputational risk but also a financial and operational threat to the organization. The increased penalties, expanded regulatory scope, and public pressure have affected organizations, especially as executives are becoming more concerned about the impact. With 82% of organizations citing compliance complexity negatively affecting senior leadership, action must be taken to adopt a resilience approach to managing diverging regulations (PwC, 2025).
COMPLIANCE CHALLENGES AFFECTING DIGITAL TRANSFORMATION
The rise of compliance complexity has also affected organizations in implementing emerging technologies to drive innovation and stay competitive within their industries. Rapid changes and increases in regulatory requirements have become major barriers to organization change, with digital transformation programs being delayed or scaled back due to resources and efforts shifting to adhere to evolving regulations. Initiatives such as AI adoption, digital modernization, and cloud migration, which are influenced by security, are being impacted, creating a friction between driving innovation and meeting regulatory obligations. A modernized approach to addressing compliance complexity is required to reduce risks, gain leadership confidence, and stay competitive within an evolving regulatory landscape.
81% of organizations report compliance complexity negatively impacted transformation priorities.
PwC, 2025

 Design and Implement a Business-Aligned Security Program
Design and Implement a Business-Aligned Security Program
 Build an Information Security Strategy
Build an Information Security Strategy
 Secure Operations in High-Risk Jurisdictions
Secure Operations in High-Risk Jurisdictions
 Develop a Security Awareness and Training Program That Empowers End Users
Develop a Security Awareness and Training Program That Empowers End Users
 Build, Optimize, and Present a Risk-Based Security Budget
Build, Optimize, and Present a Risk-Based Security Budget
 Hire or Develop a World-Class CISO
Hire or Develop a World-Class CISO
 Fast Track Your GDPR Compliance Efforts
Fast Track Your GDPR Compliance Efforts
 Build a Cloud Security Strategy
Build a Cloud Security Strategy
 Identify the Components of Your Cloud Security Architecture
Identify the Components of Your Cloud Security Architecture
 Security Priorities 2022
Security Priorities 2022
 2020 Security Priorities Report
2020 Security Priorities Report
 Manage Third-Party Service Security Outsourcing
Manage Third-Party Service Security Outsourcing
 Select a Security Outsourcing Partner
Select a Security Outsourcing Partner
 Improve Security Governance With a Security Steering Committee
Improve Security Governance With a Security Steering Committee
 The First 100 Days as CISO
The First 100 Days as CISO
 Determine Your Zero Trust Readiness
Determine Your Zero Trust Readiness
 Cost-Optimize Your Security Budget
Cost-Optimize Your Security Budget
 Threat Preparedness Using MITRE ATT&CK®
Threat Preparedness Using MITRE ATT&CK®
 Build a Zero Trust Roadmap
Build a Zero Trust Roadmap
 Security Priorities 2023
Security Priorities 2023
 Security Priorities 2024
Security Priorities 2024
 Grow Your Own Cybersecurity Team
Grow Your Own Cybersecurity Team
 Security Priorities 2025
Security Priorities 2025
 Create a Zero Trust Implementation Plan
Create a Zero Trust Implementation Plan
 Build Adaptive Security Services
Build Adaptive Security Services
 Run IT By the Numbers
Run IT By the Numbers
 Transform IT, Transform Everything
Transform IT, Transform Everything
 The Race to Develop Talent
The Race to Develop Talent
 Assessing the AI Ecosystem
Assessing the AI Ecosystem
 Bring AI Out of the Shadows
Bring AI Out of the Shadows
 IT Spend and Staffing Benchmarking
IT Spend and Staffing Benchmarking
 The Security Playbook
The Security Playbook
 Security Priorities 2026
Security Priorities 2026