- The security team is unsure of governance needs and how to manage them.
- There is a lack of alignment between key stakeholder groups
- There are misunderstandings related to the role of policy and process.
Our Advice
Critical Insight
Good governance stems from a deep understanding of how stakeholder groups interact with each other and their respective accountabilities and responsibilities. Without these things, organizational functions tend to interfere with each other, blurring the lines between governance and management and promoting ad–hoc decision making that undermines governance.
Impact and Result
- The first phase of this project will help you establish or refine your security governance and management by determining the accountabilities, responsibilities, and key interactions of your stake holder groups.
- In phase two, the project will guide you through the implementation of essential governance processes: setting up a steering committee, determining risk appetite, and developing a policy exception-handling process.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
10.0/10
Overall Impact
$19,350
Average $ Saved
13
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
Donor Network West
Guided Implementation
10/10
$13,700
5
getting expert understanding in this space is very important to our organization. worst part is when the models don't have clear definition on the ... Read More
ATS CORPORATION
Guided Implementation
10/10
$25,000
20
Fritz Jean-Lois provided valuable guidance in quickly developing our security governance and management plan to support our goal of maturing the se... Read More
Sage Therapeutics
Workshop
10/10
N/A
N/A
The workshop was very insightful and I enjoyed the workshop immensely. Working through the charters and learning how to maximize our use of the to... Read More
NMB BANK PLC.
Guided Implementation
10/10
$12,599
50
The best experience was when Logan was explaining to me different options available with infotech, that opened my eyes for change of direction on m... Read More
The University Of Manchester
Guided Implementation
9/10
$152K
20
Wonder Brands Inc.
Guided Implementation
8/10
N/A
5
DAI Global, LLC
Guided Implementation
9/10
$12,399
5
I very much appreciate the knowledgeable experts who helped us quickly understand an approach to get our arms around a way to move forward with eva... Read More
Elementis Specialties
Guided Implementation
10/10
N/A
120
City of Kirkland
Guided Implementation
10/10
N/A
N/A
Allegis
Guided Implementation
10/10
$2,546
5
Filipe is very knowledgeable on the topic and the other resources that Infotech has available.
Clark Schaefer Hackett
Guided Implementation
10/10
$3,820
20
Having Kevin's expertise to help me through this project was very helpful.

Security Management
Establish the missing bridge between security and the business to support tomorrow's enterprise with minimal resources.
- Course Modules: 3
- Estimated Completion Time: 1 hour
Establish Effective Security Governance & Management
The key is in stakeholder interactions, not policy and process.
Analyst Perspective
It's about stakeholder interactions, not policy and process.
Many security leaders complain about a lack of governance and management in their organizations. They have policies and processes but find neither have had the expected impact and that the organization is teetering on the edge of lawlessness, with stakeholder groups operating in ways that interfere with each other (usually due to poorly defined accountabilities).
Among the most common examples is security's relationship to the business. When these groups don't align, they tend to see each other as adversaries and make decisions in line with their respective positions: security endorses one standard, the business adopts another.
The consequences of this are vast. Such an organization is effectively opposed to itself. No wonder policy and process have not resolved the issue.
At a practical level, good governance stems from understanding how different stakeholder groups interact, providing inputs and outputs to each other and modeling who is accountable for what. But this implied accountability model needs to be formalized (perhaps even modified) before governance can help all stakeholder groups operate as strategic partners with clearly defined roles, responsibilities, and decision-making power. Only when policies and processes reflect this will they serve as effective tools to support governance.

Logan Rohde
Senior Research Analyst, Security & Privacy
Info-Tech Research Group
Executive Summary
| Your Challenge | Common Obstacles | Info-Tech's Approach |
Ineffective governance and management processes, if they are adopted at all, can lead to:
|
Most governance and management initiatives stumble because they do not address governance as a set of interactions and influences that stakeholders have with and over each other, seeing it instead as policy, process, and risk management. Challenges include:
| You will be able to establish a robust governance model to support the current and future state of your organization by accounting for these three essential parts:
|
Info-Tech Insight
Good governance stems from a deep understanding of how stakeholder groups interact with each other and their respective accountabilities and responsibilities. Without these things, organizational functions tend to interfere with each other, blurring the lines between governance and management and promoting ad hoc decision making that undermines governance.
Your challenge
This research is designed to help organizations who need to:
- Establish security governance from scratch.
- Improve security governance despite a lack of cooperation from the business.
- Determine the accountabilities and responsibilities of each stakeholder group.
This blueprint will solve the above challenges by helping you model your organization's governance structure and implement processes to support the essential governance areas: policy, risk, and performance metrics.
Percentage of organizations that have yet to fully advance to a maturity-based approach to security
70%
Source: McKinsey, 2021
Common obstacles
These barriers make this challenge difficult to address for many organizations:
- The business does not wish to be governed and does not seek to align with security on the basis of risk.
- Various stakeholder groups essentially govern themselves, causing business functions to interfere with each other.
- Security teams struggle to differentiate between governance and management and the purpose of each.
Early adopter infrastructure
63%
Security leaders not reporting to the board about risk or incident detection and prevention.
Source: LogRhythm, 2021
46%
Those who report that senior leadership is confident cybersecurity leaders understand business goals.
Source: LogRhythm, 2021
Governance isn't just policy and process
Governance is often mistaken for an organization's formalized policies and processes. While both are important governance supports, they do not provide governance in and of themselves.
For governance to work well, an organization needs to understand how stakeholder groups interact with each other. What inputs and outputs do they provide? Who is accountable? Who is responsible? These are the questions one needs to ask before designing a governance structure. Failing to account for any of these three elements tends to result in overlap, inefficiency, and a lack of accountability, creating flawed governance.
Separate governance from management
Oversight versus operations
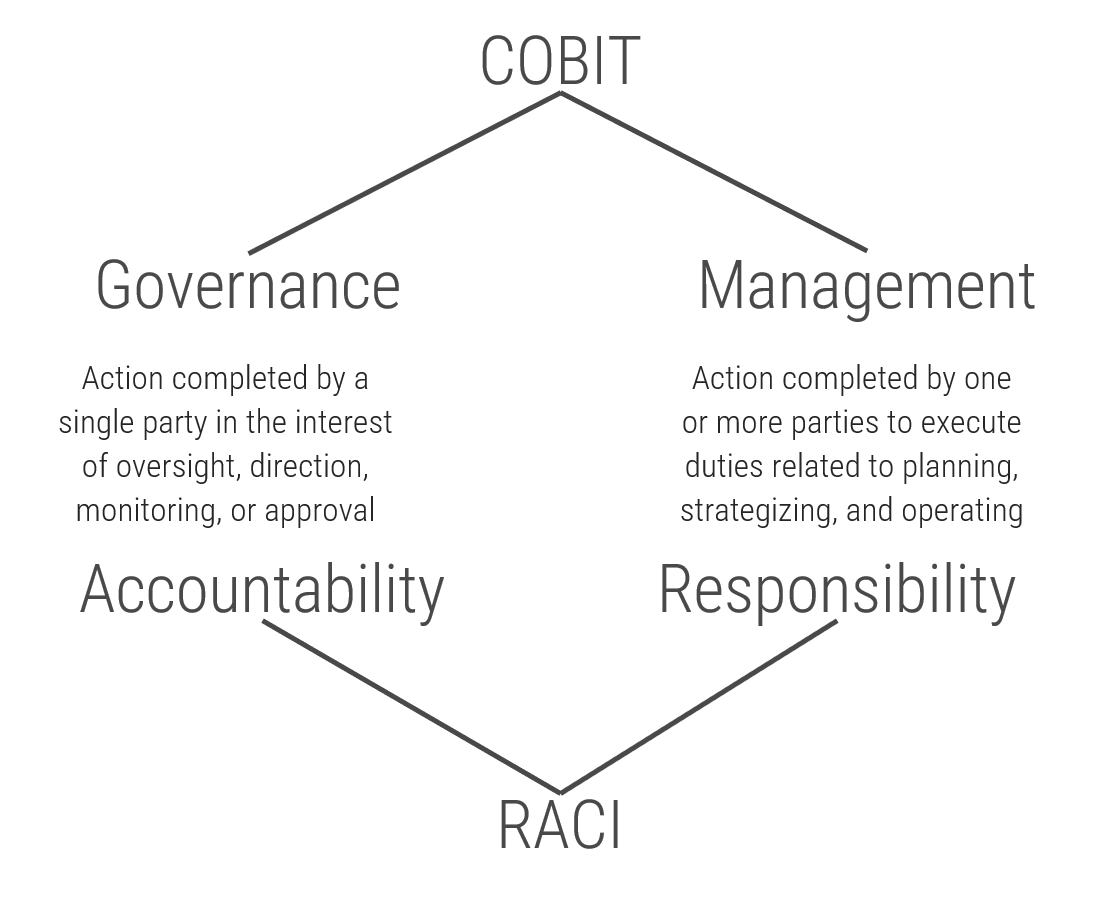
- COBIT emphasizes the importance of separating governance from management. These are complementary functions, but they refer to different parts of organizational operation.
- Governance provides a decision-making apparatus based on predetermined requirements to ensure smooth operations. It is used to provide oversight and direction and hinges on established accountabilities
- Simply put, governance refers to what an organization is and is not willing to permit in day-to-day operations, and it tends to make its presence known via the key areas of risk appetite, formal policy and process, and exception handling.
- Note: These key areas do not provide governance in and of themselves. Rather, governance emerges in accordance with the decisions an organization has made regarding these areas. Sometimes, however, these "decisions" have not been formally or consciously made and the current state of the organization's operations becomes the default - even when it is not working well.
- Management, by contrast, is concerned with executing business processes in accordance with the governance model, essentially, governance provides guidance for how to make decisions during daily management.
"Information security governance is the guiding hand that organizes and directs risk mitigation efforts into a business-aligned strategy for the entire organization."
Steve Durbin,
Chief Executive,
Information Security Forum, Forbes, 2023
Models for governance and management
Info-Tech's Governance and Management research uses the logic of COBIT's governance and management framework but distills this guidance into a practical, easy-to-implement series of steps, moving beyond the rudimentary logic of COBIT to provide an actionable and personalized governance model.


Clear accountabilities and responsibilities
Complementary frameworks to simplify governance and management
The distinction that COBIT draws between governance and management is roughly equivalent to that of accountability and responsibility, as seen in the RACI* model.
There can be several stakeholders responsible for something, but only one party can be accountable.
Use this guidance to help determine the accountabilities and responsibilities of your governance and management model.
*Responsible, Accountable, Consulted, Informed
Security governance framework
A security governance framework is a system that will design structures, processes, accountability definitions, and membership assignments that lead the security department toward optimal results for the business.
Governance is performed in three ways:
| 1 Evaluate | 2 Direct | 3 Monitor |
|---|---|---|
| For governance to be effective it must account for stakeholder interests and business needs. Determining what these are is the vital first step. | Governance is used to determine how things should be done within an organization. It sets standards and provides oversight so decisions can be made during day-to-day management. | Governance needs change and inefficiencies need to be revised. Therefore, monitoring key performance indicators is an essential step to course correct as organizational needs evolve. |
"Governance specifies the accountability framework and provides oversight to ensure that risks are adequately mitigated, while management ensures that controls are implemented to mitigate risks. Management recommends security strategies. Governance ensures that security strategies are aligned with business objectives and consistent with regulations."
- EDUCAUSE

 Assess and Manage Security Risks
Assess and Manage Security Risks
 Assess Your Cybersecurity Insurance Policy
Assess Your Cybersecurity Insurance Policy
 Achieve Digital Resilience by Managing Digital Risk
Achieve Digital Resilience by Managing Digital Risk
 Prevent Data Loss Across Cloud and Hybrid Environments
Prevent Data Loss Across Cloud and Hybrid Environments
 Build an IT Risk Management Program
Build an IT Risk Management Program
 Develop and Deploy Security Policies
Develop and Deploy Security Policies
 Fast Track Your GDPR Compliance Efforts
Fast Track Your GDPR Compliance Efforts
 Build a Security Compliance Program
Build a Security Compliance Program
 Embed Privacy and Security Culture Within Your Organization
Embed Privacy and Security Culture Within Your Organization
 Establish Effective Security Governance & Management
Establish Effective Security Governance & Management
 Improve Security Governance With a Security Steering Committee
Improve Security Governance With a Security Steering Committee
 Develop Necessary Documentation for GDPR Compliance
Develop Necessary Documentation for GDPR Compliance
 Reduce and Manage Your Organization’s Insider Threat Risk
Reduce and Manage Your Organization’s Insider Threat Risk
 Satisfy Customer Requirements for Information Security
Satisfy Customer Requirements for Information Security
 Master M&A Cybersecurity Due Diligence
Master M&A Cybersecurity Due Diligence
 Integrate IT Risk Into Enterprise Risk
Integrate IT Risk Into Enterprise Risk
 Present Security to Executive Stakeholders
Present Security to Executive Stakeholders
 Deliver Customer Value by Building Digital Trust
Deliver Customer Value by Building Digital Trust
 Address Security and Privacy Risks for Generative AI
Address Security and Privacy Risks for Generative AI
 Protect Your Organization's Online Reputation
Protect Your Organization's Online Reputation
 Develop an AI Compliance Strategy
Develop an AI Compliance Strategy
 Get Started With AI Red-Teaming
Get Started With AI Red-Teaming
 Achieve CMMC Compliance Effectively
Achieve CMMC Compliance Effectively
 Building Info-Tech’s Chatbot
Building Info-Tech’s Chatbot
 Building the Road to Governing Digital Intelligence
Building the Road to Governing Digital Intelligence
 An Operational Framework for Rolling Out AI
An Operational Framework for Rolling Out AI
 Discover and Classify Your Data
Discover and Classify Your Data