Cloud adoption has moved faster than the decisions and controls needed to manage it. The result is fragmented deployments, spiraling costs, and poor alignment with organizational needs. Even technically successful migrations are often marked by waste and governance gaps that turn cloud into a liability rather than a strategic asset. This blueprint offers a practical approach to building a cloud strategy grounded in organizational alignment, governance maturity, and pattern-driven decision-making.
A strong cloud strategy aligns deployment decisions, whether rehosting, refactoring, rebuilding, or buying, with proven strategic patterns and antipatterns across security, networking, access control, cost, and workload architecture. Success depends on adopting best-practice patterns (e.g. least privilege access) while avoiding antipatterns (e.g. broad permissions or manual IAM). A pattern-informed strategy ensures the right choices are made, at the right time, for the right reasons.
1. Start with a strategic framework or risk failure.
Without a strategy to guide workload placement, identity governance, architecture choices, and cost control, organizations may scale their cloud usage but not their cloud value. Strategy is not a delay; it’s a multiplier. A structured strategy rooted in best practices and reusable patterns turns cloud investment into long-term value.
2. Cloud waste is a strategy problem.
Overspending is another predictable outcome of poor cloud strategy. When organizations lack a unified approach, cloud costs balloon due to overprovisioning, shadow IT, and default lift-and-shift decisions. The failure lies with strategic alignment, not cost control.
3. You can’t govern what you can’t see.
Cloud environments often grow faster than the governance structures that are meant to control them, leading to misconfigurations, compliance violations, and budget overruns. Effective governance begins with observability: use tagging, cost attribution frameworks, and platform-native tools create the visibility needed to enforce strategy, detect risk, and ensure accountability at scale.
Use this step-by-step blueprint to take a strategic, pattern-driven approach to cloud decision-making
This research offers a practical framework supported by workbooks, templates, and a roadmap to build a cloud strategy backed by clear principles and informed by the right patterns. Follow this four-phased approach to ensure cloud adoption is structured, strategic, and set up to enable agility and innovation at scale.
- Determine your corporate goals and cloud drivers, identify success indicators, summarize your current state, and create your cloud mission, vision, guiding principles, and patterns.
- Assess key workloads using a structured tool and consider suitability for various cloud disposition strategies.
- Identify and mitigate risks by generating a categorized list of risks, roadblocks, and mitigation measures.
- Bridge the gap and create a strategy to inform your execution roadmap, including assigning initiatives and timelines, finalizing a decision framework, and creating a cloud vision statement.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
9.5/10
Overall Impact
$43,511
Average $ Saved
18
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
Oregon Enterprise Information Services
Workshop
10/10
$34,000
20
Worst part was our meeting tech (Oregon's fault). The best part was our conversations and the resulting progress. We made a big jump in 4 days.
City of Winter Park
Guided Implementation
10/10
$34,000
5
Frank is an expert in what he does.
Oregon Department of Revenue
Workshop
9/10
N/A
N/A
Nabeel was very knowledgeable and did a great job of getting information out of the attendees. He also explained things very well so the whole gro... Read More
Al Nahdi Medical
Guided Implementation
7/10
N/A
5
The best part was the instructor's patience and his ability to clearly explain all topics, along with his excellent follow-up to ensure I understoo... Read More
Fernco Inc
Workshop
9/10
$34,000
10
Best. Ability to have a facilitated discussion on the ERP Application current state on-premises deployment and possible future state Cloud ERP appl... Read More
Belcan, LLC
Workshop
10/10
$34,000
10
Our facilitator Jeremy was knowledgeable about this topic and made the workshop enjoyable for the group. Great balance of letting our group discuss... Read More
Town of Taber
Guided Implementation
10/10
$25,000
50
Interfor Corp
Workshop
10/10
$50,000
10
The engagement delivery has been one of the best workshops which I've attended. The framework guidance is incredibly helpful to address a well-roun... Read More
California Department of Social Services
Guided Implementation
10/10
N/A
47
Nabeel is very knowledgeable and patient. I feel things should be progressing faster, but all the delays have been on our end. I like how Nabeel fa... Read More
Jennison Associates
Workshop
9/10
$68,500
10
I've asked the rest of the team and we all agree that this was a great experience and exceeded expectations. Jeremy moved the conversation along. ... Read More
State of Minnesota - Minnesota State Retirement System
Workshop
9/10
$32,195
10
Best Part. Analyst was very knowledgeable (Nabeel) Worst Part. Workshop started slow. I think we could've covered more applications for potential ... Read More
City Of Avondale
Workshop
10/10
$65,075
5
1Path Managed Services, LLC
Guided Implementation
10/10
$19,883
18
Best Part - Nabeel... Does anything else need to be said about this? Worst Part - I wouldn't say there is a "worst" part. Perhaps, a place to impr... Read More
RiverStone Health
Workshop
10/10
N/A
N/A
Jeremy was fantastic at presenting data and keeping us focused on our goals. He was engaging, listened well, and was great at helping guide us thro... Read More
1Path Managed Services, LLC
Guided Implementation
10/10
$6,499
10
University of South Australia
Guided Implementation
9/10
$32,499
50
Working with Nabeel on Uni SA's Cloud Strategy was an exceptional experience. It was evident that a cloud strategy was essential, and using tools t... Read More
Daylight Transport, LLC
Workshop
9/10
$129K
10
Jeremy was an effective facilitator with a strong command of the content and possible options. He led the discussion well and offered doors we cou... Read More
University of South Australia
Guided Implementation
8/10
$64,999
20
Sharonview Federal Credit Union
Workshop
10/10
$27,880
5
Extremely thought provoking and engaging conversations. Jeremy was fantastic to work with and extremely knowledgeable!
Oneida Nation
Workshop
10/10
N/A
10
I think Jeremy was great as a facilitator for our cross-functional group. He was able to pull out a lot of great information from the various stak... Read More
County of Los Alamos
Guided Implementation
10/10
$2,599
5
great call and info. Solid direction. Looking forward to adding to the above numbers on subsequent calls/engagements.
Cobb EMC
Workshop
10/10
$64,999
23
Best: Jeremy’s engagement, flexibility, and expertise. Worst: none. Achieved session goals for me.
Collier County Board of County Commissioners
Workshop
9/10
$389K
90
Very agile, informative, and provided by the experience of Jeremy's insights the "what everybody else is doing or seen" so we do not re-invent the ... Read More
Stockman Bank
Workshop
10/10
$71,499
23
Washington Technology Solutions
Guided Implementation
7/10
N/A
N/A
Good appreciative questions, time-bound proposed way-ahead that acknowledges past prep work.
Health Canada
Guided Implementation
10/10
$4,000
20
The best part was the ability for the analyst to quickly understand my situation and we could take advantage of this commonality to discuss next st... Read More
Monroe #1 BOCES
Workshop
10/10
$129K
50
The workshop was fantastic! The feedback from our entire team was highly positive. Jeremy is very versed in Cloud Strategy and kept things intere... Read More
ENERGYUNITED ELECTRIC MEMBERSHIP CORPORATION
Workshop
10/10
$1.3M
90
Jeremy's ability to engage our team enabled us to maximize the value of this workshop. We never felt rushed to get through the agenda, yet we manag... Read More
Denver Water
Workshop
10/10
$519K
50
Jeremy is a fantastic facilitator of this topic - he's knowledgeable and is able to leverage prior experiences with other organizations to help us.... Read More
Canadian Blood Services
Workshop
8/10
$95,000
23

Infrastructure & Cloud Strategy
Learners will be able to understand the unique aspects of the cloud, evaluate workloads for cloud suitability, address associated risks and challenges, create a systematic cloud strategy, and communicate the cloud vision to their organization.
- Course Modules: 7
- Estimated Completion Time: 1.5 hours
Workshop: Empower Your Business With a Proven Cloud Strategy
Workshops offer an easy way to accelerate your project. If you are unable to do the project yourself, and a Guided Implementation isn't enough, we offer low-cost delivery of our project workshops. We take you through every phase of your project and ensure that you have a roadmap in place to complete your project successfully.
Module 1: Understand the Cloud
The Purpose
Understand the cloud components.
Key Benefits Achieved
Determine cloud readiness.
Activities
Outputs
Align business goals.
- Success indicators
Create mission and vision statement for cloud strategy.
- Current state summaries
State cloud vision, mission, guiding principles, and patterns.
- Vision, mission, guiding principles, and patterns
Module 2: Assess Workloads
The Purpose
Select workloads for assessment.
Key Benefits Achieved
Gain a foundation for evidence-based decisions by combining data-driven insights with expert input.
Activities
Outputs
Identify target workloads.
- Completed workload assessments
Assess workloads using strategy tool.
- Cloud placement decision guidelines
Review results and next steps.
Module 3: Identify and Mitigate Risks
The Purpose
Identify risks and roadblocks.
Key Benefits Achieved
Determine risks and remediation tasks.
Activities
Outputs
Generate a list of risks and roadblocks.
- Categorized list of risks and roadblocks
Identify mitigations.
- List of mitigations
Generate initiatives from the mitigations.
Module 4: Bridge the Gap and Create the Strategy
The Purpose
Build a roadmap.
Key Benefits Achieved
Create a working document for execution.
Activities
Outputs
Review and assign work items.
- Assigned initiatives
Finalize the decision framework.
- Finalized decision framework
Create a cloud vision statement
- Cloud vision statement
Make confident cloud decisions with a strategy grounded in patterns, principles, and purpose.
Turn cloud decisions into competitive advantage with a strategic, pattern-driven approach.
EXECUTIVE BRIEF
Analyst perspective
A structured approach to aligning cloud decisions with strategic goals
As cloud adoption continues to accelerate, the challenge is no longer whether to use the cloud but how to use it with insight, vision and direction. Without a cohesive strategy, organizations risk fragmented deployments, uncontrolled costs, and misaligned investments.
This blueprint presents a practical approach to building a cloud strategy rooted in business alignment, governance maturity, and pattern-driven decision-making. By identifying best-practice patterns – and proactively avoiding common antipatterns – IT leaders can transform cloud complexity into a structured framework for execution.
Through a balance of vision, policy, and technical readiness, organizations can leverage the cloud not only as an infrastructure solution but as a strategic enabler of agility, innovation, and competitive differentiation.
In addition, to be able to govern effectively, organizations must first ensure observability – through a combination of tagging discipline, identity-aware dashboards, cost allocation frameworks, and platform-native tools (like Azure Resource Graph, AWS Config, or GCP Asset Inventory). These provide the factual baseline from which patterns and antipatterns can be identified, measured, and managed.

John Donovan
Principal Research Director, I&O
Info-Tech Research Group
Executive summary
Your Challenge
Cloud strategies often falter not because of technical failure but due to inconsistent or uninformed deployment decisions, such as:
- Inconsistent implementations across business units.
- Security misconfigurations due to antipatterns like over-provisioned access or unmanaged IAM.
- Poor workload placement that impacts performance, cost, and scalability.
- Low reusability or automation, especially when patterns aren't codified across teams.
Common Obstacles
- Decision-Making Without Context: Cloud decisions are often driven by short-term pressures (e.g. contract expiration, “move fast”) instead of long-term strategic value.
- Siloed Knowledge and Inconsistent Adoption: Different teams use different tools, IAM models, deployment processes, or security controls, leading to operational inefficiencies.
- Tooling Without Governance: DevOps, AI/ML, and cloud-native tools are deployed without architectural standards, introducing risk and debt.
Info-Tech’s Approach
Info-Tech shifts cloud strategy from tactical enablement to pattern-based alignment that informs when and why to adopt specific cloud models across IaaS, PaaS, and SaaS.
- Define Strategic Patterns: Build a shared library of patterns and antipatterns that apply across cloud deployment models, including security, networking, access control, cost optimization, and workload architecture.
- Map Patterns to Deployment Decisions: Align each cloud decision (rehost, refactor, rebuild, buy) with the most applicable patterns to guide architecture and governance choices.
Info-Tech Insight
To build a strong cloud strategy, organizations must align deployment decisions – whether rehosting, refactoring, rebuilding, or buying – with a clear understanding of strategic patterns and antipatterns. Each decision introduces risks and opportunities, and success depends on adopting best-practice patterns (e.g. least privilege access) while avoiding antipatterns like broad permissions or manual IAM. A pattern-informed strategy ensures the right choices are made, at the right time, for the right reasons – enabling secure, scalable, and goal-aligned cloud adoption.
Challenges
Cloud spend spirals out of control without a strategy or governance.
Global investment wasted.
50% — According to a global survey reported by Broadcom, nearly half of organizations estimate that more than a quarter of their public cloud investment is wasted, and 31% believe waste exceeds 50%. (Source: Broadcom, 2025)
35% — KPMG states that many organizations overspend by 35% relative to what is needed to meet business objectives, often because they default to “lift-and-shift” migrations and neglect optimization or architectural discipline. (Source: KPMG)
Most IT leaders recognize that their cloud usage has grown substantially, but many still struggle to realize its full value. The mismatch often stems from fragmented decision-making, lack of governance, and absence of a unifying framework (patterns) to steer adoption.
Info-Tech Insight
Without a strategic framework to guide workload placement, identity governance, architecture choices, and cost control, organizations may scale their cloud usage but not their cloud value. Strategy is not a delay; it’s a multiplier.
Obstacles
Cloud spend spirals out of control without a strategy or governance.
Over 70% of cloud migrations fail or stall due to strategy gaps.
70% — EPI‑USE (citing industry practice) claims that more than 70% of cloud migration initiatives fail or stall (including missed goals, cost overruns, performance gaps, or rollback), often due to inadequate planning, strategic misalignment, or underestimated complexity. (Source: EPI-USE, 2024)
80% — Crayon reports that 80% of organizations globally overspend on their cloud infrastructure budgets – often attributed to a lack of strategy, poor cost control, or misaligned deployments. (Source: Crayon, 2022)
The promise of cloud transformation often falls short of reality. Even when migrations succeed technically, 80% of organizations overspend
Info-Tech Insight
Cloud success isn’t just about getting there – it’s about getting there the right way. Without a strategy to align goals, guide decisions, and enforce guardrails, organizations risk delays, overruns, and disappointment. A structured strategy rooted in best practices and reusable patterns turns cloud investment into long-term value.
Components of a strategy
Info-Tech’s working definition of a cloud strategy has six major areas.
- Mission: To define a strategy and have it understood in context, you must first define your function (in the strategic context) and reason for existence.
- Vision: The strategic vision encompasses the desired future state, focusing on the ends – not the means used to get there.
- Goals: The goals are broad statements of direction that support the vision and mission of a strategy.
- Drivers: The drivers of a strategy describe the “why now?” and outline the reasons for the strategic direction.
- Guiding Principles: The guiding principles outline the boundaries of the strategy. In the absence of a specific strategic direction, they provide guidance.
- Strategic Initiatives: The strategic initiatives are the major programs that will encompass the initiatives needed to execute the strategy and adhere to standards.
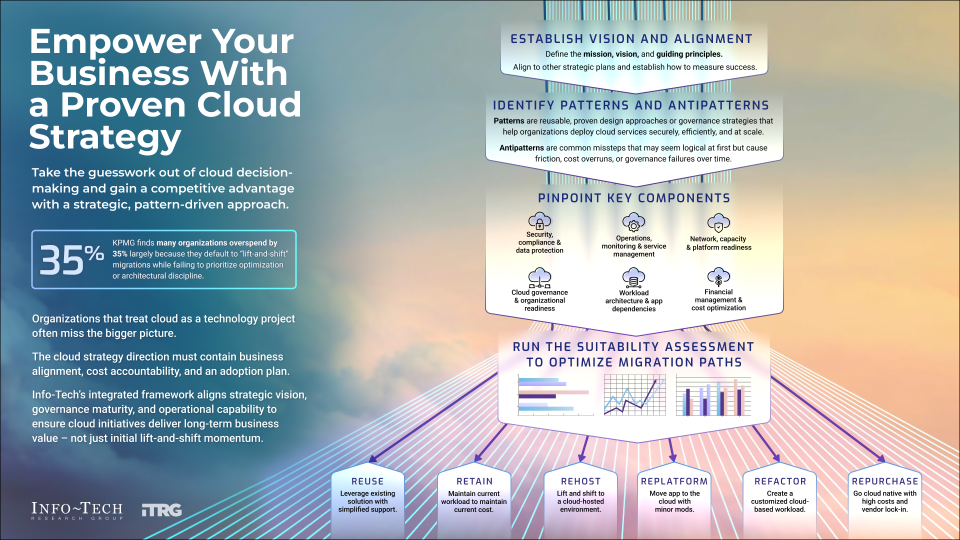
Info-Tech’s methodology for empowering your business with a cloud strategy
1. Understand the cloud |
2. Assess workloads |
3. Identify and mitigate risk |
4. Bridge the gap and create a strategy |
|
Activities |
|
|
|
|
Deliverables |
|
|
|
|
Insight summary
Develop a strategic framework
Without a strategic framework to guide workload placement, identity governance, architecture choices, and cost control, organizations may scale their cloud usage but not their cloud value. Strategy is not a delay; it’s a multiplier.
Cloud waste is a strategy problem
Organizations without a unified cloud strategy often overspend by 25%-35% due to a mix of overprovisioning, shadow IT, and lift-and-shift approaches with no optimization layer. This isn’t a cost problem – it’s a strategic alignment failure.
Cloud success isn’t about where you host, it’s about how you adopt
To evolve from fragmented cloud adoption to a scalable program, organizations must embed strategic cloud patterns aligned with business goals. Avoiding antipatterns reduces waste, risk, and rework – ensuring every cloud decision is timely, governed, and fit for purpose.
You can’t govern what you can’t see
In many organizations, cloud environments evolve faster than the governance structures designed to control them. Misconfigurations, compliance violations, orphaned resources, and runaway costs often go unnoticed until they become audit findings or budget crises.
Tactical insight
Antipatterns drain budgets and delay outcomes. Identifying and correcting misaligned practices early prevents cost overruns and rework.
Tactical insight
A successful cloud strategy isn’t just about technology – it’s about alignment, accountability, and adoption. Organizations that treat the cloud as a technology project often miss the bigger picture.
Blueprint benefits
IT Benefits
- Improved Alignment Between Workloads and Cloud Architectures
Leveraging strategic patterns ensures the right cloud services and deployment models are chosen for each workload – minimizing complexity, improving performance, and reducing rework. - Operational Efficiency Through Repeatable Patterns
Standardized patterns (e.g. automation, security baselines, identity models) reduce manual effort, speed up deployment cycles, and simplify environment management. - Stronger Governance and Risk Mitigation
Embedding patterns into the strategy brings clarity to cloud guardrails, improving visibility, enforcing least-privilege access, and minimizing policy drift across multicloud environments.
Business Benefits
- Faster Time-to-Value for Cloud Investments
With clear strategy and repeatable deployment patterns, business units can accelerate solution delivery while staying within guardrails, shortening the timeline between investment and outcomes. - Cost Optimization and Predictability
Avoiding antipatterns such as overprovisioning and siloed services helps reduce cloud waste, prevent budget overruns, and drive financial accountability for cloud spend. - Strategic Agility and Innovation Enablement
A well-structured cloud strategy empowers the business to adapt quickly – whether by scaling up services, integrating AI/ML, or pivoting delivery models – without being constrained by fragmented infrastructure decisions.
Case study

INDUSTRY: Oil & Gas | SOURCE: Tech Monitor
BP adopts hybrid cloud and moves applications and datacenter operations to Azure.
Challenge
BP operated a large global datacenter footprint across 70+ countries, which created high operational overhead, capital expenses, and complexity.
Some workloads needed to remain local or on-prem due to regulatory, compliance, or data sovereignty constraints, requiring a hybrid approach rather than pure cloud.
Early in the migration, BP tried to “lift and shift” existing behaviors to the cloud, which didn’t unlock full value, forcing the organization to rethink cloud-native approaches.
Solution
BP adopted a cloud-first strategy and began moving both applications and infrastructure to Microsoft Azure.
It built a hybrid architecture, retaining on-prem or edge components (e.g. Azure Stack) where needed for locations with compliance or connectivity concerns.
It used Azure networking tools (like ExpressRoute and hub-and-spoke designs) to ensure high‑performance, low-latency, and secure connectivity between on-prem and cloud.
Results
BP has exited or decommissioned at least one mega data center and is on a path to reduce further data center overhead.
It achieved greater agility and scalability, being able to spin up resources on demand rather than preprovisioning massive infrastructure.
BP reduced operational burden, shifting resources away from pure infrastructure management toward higher-value development and innovation.
Info-Tech offers various levels of support to best suit your needs
DIY Toolkit |
Guided Implementation |
Workshop |
Consulting |
| “Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful.” | “Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track.” | “We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place.” | “Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project.” |
Diagnostics and consistent frameworks are used throughout all four options. |
|||
Project metrics
Track adoption. Reduce risk. Optimize value.
KPI |
Outcome |
Impact |
Cloud adoption rate |
Increased % of targeted workloads/services migrated to cloud | Accelerate infrastructure modernization |
Average time to provision new cloud infrastructure or services |
Faster delivery of IT services to business | Increase innovation, ability to respond to business needs |
Availability and uptime of cloud services |
Higher reliability and performance | Increase end user satisfaction, improve business continuity |
Cloud skills adoption |
Increased % of IT staff trained/certified on cloud technologies | Reduce risk of third-party partner dependency, become a place people want to work and develop new skills |
Cloud governance maturity |
Increased % of cloud services covered by formal governance (tagging, FinOps team, Cloud Center of Excellence) | Reduce risk, optimize costs where possible, apply consistent policies |
Acceleration of digital transformation |
Increased number of new cloud-enabled services/features delivered per quarter | Increase innovation and competitive differentiation |
Measure the value of this blueprint
Don’t take our word for it:
- Document Your Cloud Strategy has been available for several years in various forms as both a workshop and as an analyst-led Guided Implementation.
- After each engagement, Info-Tech sends a survey that asks members how they benefited from the experience. Those who have worked through Info-Tech’s cloud strategy material have given overwhelmingly positive feedback.
- Additionally, members reported saving an average 41 days and $308,264.
- Measure the value by calculating the time saved as a result of using Info-Tech’s framework vs. a home-brewed cloud strategy alternative and comparing the overall cost of a Guided Implementation or workshop with the equivalent offering from another firm. We’re confident you’ll come out ahead.
9.7/10 Average reported satisfaction
41 Days Average reported time savings
$308,264 Average cost savings
Blueprint deliverables
Key deliverable:
Cloud Strategy Workbook
Drive alignment through assessment and planning. This interactive Excel workbook guides you through key activities: capability assessments, pattern selection, prioritization, and domain readiness. It enables collaborative working sessions and provides a living record of strategic decisions.
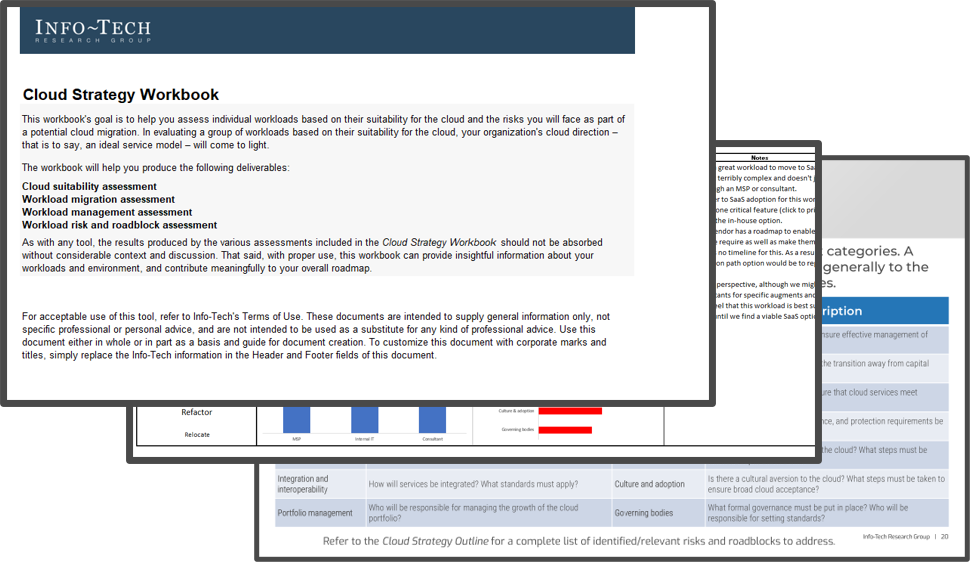
Each step of this blueprint is accompanied by supporting deliverables to help you accomplish your goals:
Cloud Strategy Executive Presentation
Use this deck as a template to socialize the cloud strategy across business and IT leadership, accelerate decision-making, and build alignment on next steps.

Cloud Strategy Workbook
This interactive workbook guides you through workload selection, risk, and mitigations to form an informed strategy.
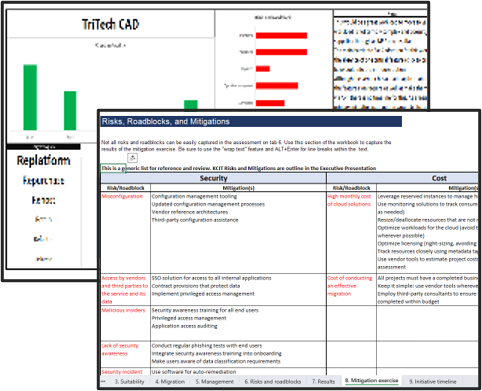
Cloud Strategy Document Template
Use this template to ensure the overall vision is executed effectively.

Cloud Strategy Roadmap
Use this roadmap to manage your short-, medium-, and long-term projects and initiatives.

Guided Implementation
A Guided Implementation (GI) is a series of calls with an Info-Tech analyst to help implement our best practices in your organization.
A typical GI is 8 to 12 calls over the course of 4 to 6 months.
What does a typical GI on this topic look like?
Phase 1 |
Phase 2 |
Phase 3 |
Phase 4 |
| Call #1: Define scope requirements, objectives, and your specific challenges. Align business and IT goals and cloud drivers. | Call #2: Define cloud strategy components.
Discuss AI/ML capabilities impact on your bank. Call #3: Complete cloud workload assessments and placement decision guidelines. |
Call #4: Generate list of risks and roadblocks and define categories.
Call #5: Generate initiatives from the mitigations. |
Call #6: Review and assign work items.
Call #7: Build roadmap/task list. Call #8: Finalize decision framework. Call #9: Create cloud vision statement. |
Workshop overview
Contact your account representative for more information.
workshops@infotech.com 1-888-670-8889
Day 1 |
Day 2 |
Day 3 |
Day 4 |
Offsite day |
|
Understand the Cloud |
Assess Workloads |
Identify and Mitigate Risks |
Bridge the Gap and Create the Strategy |
Next Steps and Wrap-Up (offsite) |
|
Activities |
|
|
|
|
|
Outcomes |
|
|
|
|
|
Empower Your Business With a Proven Cloud Strategy
Phase 1
Align Business and IT Goals
Phase 11.1 Business goal alignment 1.2 Mission and vision statement for cloud strategy 1.3 Cloud vision, mission, guiding principles and patterns |
Phase 22.1 Identify target workloads 2.2 Assess workloads using tool 2.3 Review results and decide next steps |
Phase 33.1 Generate list of risks and roadblocks 3.2 Identify mitigations 3.3 Generate initiatives from mitigations |
Phase 44.1 Review and assign work items 4.2 Finalize decision framework 4.3 Create a cloud vision statement |
This phase will walk you through the following activities:
Develop your organization’s:
- Corporate goals and cloud drivers
- Success indicators
- Current state summary
- Mission, vision, guiding principles, and patterns
This phase involves the following participants:
- CIO
- Senior IT team
- Infrastructure leaders
1.1.1 Generate organizational goals
1-3 hours
Input: Strategy documentation
Output: Organizational goals
Materials: Whiteboard (digital/physical)
Participants: IT leadership, Infrastructure, Applications, Security
- As a group, brainstorm organizational goals, ideally based on existing documentation.
- Review relevant corporate and IT strategies.
- If you do not have access to internal documentation, review the standard goals on the next slide and select those that are most relevant for you.
- Record the most important business goals in the Cloud Strategy Executive Presentation. Include descriptions where possible to ensure wide readability.
- Make note of these goals. They should inform the answers to prompts offered in the Cloud Strategy Workbook and should be a consistent presence in the remainder of the visioning exercise. If you’re conducting the session in person, leave the goals up on a whiteboard and refer to them throughout the workshop.
Download the Cloud Strategy Executive Presentation

 Effectively Acquire Infrastructure Services
Effectively Acquire Infrastructure Services
 Empower Your Business With a Proven Cloud Strategy
Empower Your Business With a Proven Cloud Strategy
 Next-Generation InfraOps
Next-Generation InfraOps
 Create a Game Plan to Implement Cloud Backup the Right Way
Create a Game Plan to Implement Cloud Backup the Right Way
 Build a Cloud Security Strategy
Build a Cloud Security Strategy
 Take Control of Cloud Costs on AWS
Take Control of Cloud Costs on AWS
 Take Control of Cloud Costs on Microsoft Azure
Take Control of Cloud Costs on Microsoft Azure
 Identify the Components of Your Cloud Security Architecture
Identify the Components of Your Cloud Security Architecture
 Govern Microsoft 365
Govern Microsoft 365
 Design Your Cloud Operations
Design Your Cloud Operations
 Passwordless Authentication
Passwordless Authentication
 Legacy Active Directory Environment
Legacy Active Directory Environment
 Considerations for a Hub and Spoke Model When Deploying Infrastructure in the Cloud
Considerations for a Hub and Spoke Model When Deploying Infrastructure in the Cloud
 Get Started With FinOps
Get Started With FinOps
 Build a FinOps Strategy to Enable Dynamic Cloud Cost Management
Build a FinOps Strategy to Enable Dynamic Cloud Cost Management