While Microsoft’s extensive product ecosystem includes a variety of security capabilities, organizations frequently find themselves with these tools unintentionally, as part of broader Microsoft bundles. Whether deliberately chosen or passively acquired, the inherent complexity of Microsoft’s security stack leaves users struggling to understand and fully leverage their value, resulting in underuse, redundancy, and a fragmented security posture. Our research offers a framework for demystifying Microsoft’s offerings, empowering you to take control of your security, optimize investments, and build a truly robust defense.
It can be hard to know whether your organization’s investment in Microsoft cybersecurity products is sound when you aren’t aware of what tools you are or aren’t using, leading to capability gaps and security tool bloat. That lack of knowledge also hinders your ability to justify using non-Microsoft products.
1. Take a capability-first approach.
Cost consolidation efforts can miss the mark when used to rationalize security tools, as they can result in unacknowledged security gaps. Looking beyond individual tools to focus on capabilities allows you to identify your security stack’s hidden strengths and weaknesses. This capability-first approach can fuel intentional, strategic decisions about what you have, helping you find cost efficiencies and optimizing your security environment.
2. Knowing is half the battle.
Up to 90% of an organization’s security potential goes unused, leading to increased risk, wasted resources, and missed opportunities. IT security leaders must prioritize understanding their full security arsenal to make informed decisions and optimize their defenses.
3. Don’t settle for “good enough.”
Microsoft’s sprawling security ecosystem can result in unintentional overlaps and hidden redundancies, lulling organizations into a false sense of security and masking the need for unique solutions. Don’t simply accept default Microsoft solutions, but assess each capability, justify the use of alternatives, and strategically supplement your Microsoft stack to achieve security outcomes that are right for your organization.
Use this structured framework to optimize your Microsoft tools and build a robust security system
Our research provides four-step guidance, workbooks, and other tools to take a capability-focused accounting of your Microsoft security products. Use this comprehensive framework to optimize Microsoft’s capabilities to your security needs while justifying the use of non-Microsoft products to fill any gaps.
- Conduct a security technology capability assessment to uncover hidden gaps, potential overlaps, and opportunities for optimization.
- Optimize your existing security posture by identifying essential capabilities that are currently not implemented or operating optimally.
- Eliminate duplication to fund new capabilities by making a cost comparison between desired Microsoft capabilities and non-Microsoft tools.
- Justify unused capabilities and overlaps by documenting the use of alternative solutions in place of Microsoft offerings and a clear rationale for each.
Build a Robust Security Architecture With Microsoft Technologies
Maximize your investment in Microsoft security tools, and justify where supplements are required.
Analyst perspective
Less is more: Solving the many problems created by security tool bloat.

The cybersecurity landscape is constantly evolving, with new threats emerging daily. In this environment, organizations are increasingly looking to standardize their security platforms to simplify management, reduce costs, and improve their overall security posture. Microsoft, with its comprehensive suite of security products and services, has emerged as a leading contender in this space. However, despite its dominance, Microsoft users face challenges in maintaining a secure environment. This paradox of dominance and vulnerability underscores the complexities of the cybersecurity landscape.
Massive capability leads to massive complexity, and that means underutilization, redundancy, and a fragmented security posture. This research provides a solution to this Microsoft-created problem, empowering organizations to take control of their security stack, optimize their investments, and build a truly robust defense.
What you’ll find here is a capability-driven approach to application rationalization that understands that capability gaps mean security holes. By prioritizing security capabilities instead of software products and conducting a thorough assessment of the Microsoft security stack, organizations can gain a clear understanding of their existing tools, identify gaps and overlaps, and make informed decisions. This approach empowers organizations to optimize their security posture, reduce costs, and build a more robust defense against cyberthreats.
Fred Chagnon
Principal Research Director, Security & Privacy
Info-Tech Research Group
Executive summary
|
Your Challenge |
Common Obstacles |
Info-Tech’s Approach |
|---|---|---|
|
You’re struggling to maximize your Microsoft security investments.
|
Whether you’re deeply invested in Microsoft or you only use their productivity suite, Microsoft’s $20 billion investment in security tools has created a problem for you – you need to either use these tools or justify why you’re using something else. Navigating Microsoft's vast and evolving security landscape is complex. Organizations face challenges with keeping up with product iterations (and name changes), understanding licensing models, integrating various tools, and overcoming organizational silos. |
Our approach decomposes all the Microsoft security tools right down to their individual capabilities. That way we can perform an assessment of capabilities, rather than software tools, enabling you to:
|
Traditional application rationalization approaches undermine security.
Methodologies that focus primarily on cost consolidation miss the mark with security tools because they don’t factor in the potential for leaving security gaps. To mitigate this risk, dissect your Microsoft security stack with a capability-first approach. This way, you expose its hidden strengths and weaknesses, allowing you to make intentional, strategic decisions about every capability, leading to cost efficiencies and a truly optimized and secure environment.
You have security tools that you aren’t even using
- Maybe the features were implemented a few months ago, and you don’t even know they exist.
- Maybe you’ve been using another software solution since before Microsoft supported that capability.
- Maybe you just upgraded to Microsoft 365 E5 because you needed a phone system and inherited an entire security stack along with it!
No more excuses!
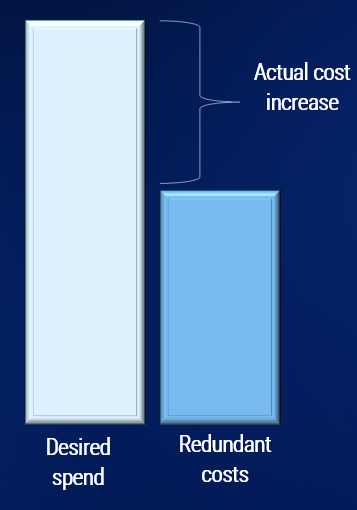
Security tool bloat is a real phenomenon, and it’s costing you money and holding your security defense back!
Our fix: Stop tracking tools and start tracking capabilities!
76: The average number of security tools used by most organizations, up from 64 in 2020 (+19%).
Source: Panaseer, 2022.
Small: 15-20 security tools
Medium: 50-60 security tools
Large: Over 130 security tools
You’re not getting full value from the tools you do use
- Maybe you have the functionality deployed, but the staff who deployed it have moved on and the knowledge is lost.
- Maybe you’re so busy battling false positive alerts that you haven’t invested the time to tune the systems causing them.
Don’t buy new solutions until you optimize the ones you have!
The “more is better” approach is a trap that encourages suboptimal implementation of processes and procedures.
Our fix: Analyze the capabilities you have today and create a plan for their full optimization!
“Security teams keep buying new technologies, looking for the silver bullet, almost praying that this will solve their problems. Many products just sit on the shelf because they don’t integrate well, they overlap, or they’re too labor-intensive to implement.”
– Olivia Rose, Founder, Rose CISO Group LLC, quoted in SiliconANGLE, 2024
Only 10%-20% of cybersecurity technology is actually used.
Source: Richard Watson, cybersecurity leader at Ernst & Young, quoted in SiliconANGLE, 2024
You’re paying multiple vendors for the same capabilities
- Maybe the non-Microsoft solution is more appropriate for your environment – has anyone challenged this?
- Maybe the cost recovered from that alternate solution could be used for fun new capabilities to fill gaps in your security defense.
You don’t need to use Microsoft’s solution for everything, but you will need to have a good reason for why you don’t!
Our fix: Make intentional decisions about where you use alternate solutions. Rationalize, but don’t compromise.
“Starting the consolidation journey without compromising security seems daunting. However, Microsoft’s suite of security solutions offers a compelling path forward. With the cybersecurity market leaning towards consolidation, aligning with a mega-vendor like Microsoft can future-proof strategies. They’re one of only a few key players driving this shift and their integrated approach can help you stay ahead.”
Source: Red Canary, 2024
You can’t afford the capabilities you actually need
- Maybe that upgrade from Microsoft 365 E3 to E5 is way out of your budget.
- Maybe you’re looking at Microsoft Security Copilot but the cost of the security compute units (SCUs) are a barrier to entry.
Time to do some cost accounting.
Our fix: Subsidize your wish list by recovering the costs incurred by tool duplication.
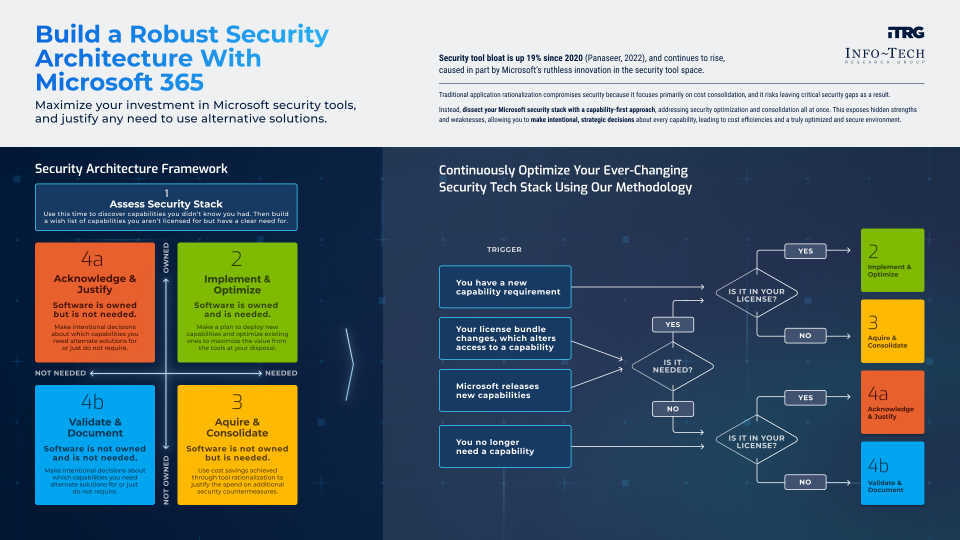
Info-Tech’s methodology for building a robust security architecture with Microsoft Technologies
|
1. Assess |
2. Optimize |
3. Rationalize |
4. Justify |
|
|---|---|---|---|---|
|
Phase Steps |
|
|
|
|
|
Phase Outcomes |
Capabilities are assessed against multiple dimensions based on whether they’re licensed, deployed, missing, covered by an alternative, or simply not needed. This exercise sorts the capabilities into categories that become the focus of the phases that follow. |
This phase yields a list of initiatives to further the operational improvement of deployed capabilities. These initiatives can be incorporated into an existing information security strategy or program. |
This phase yields a cost recovery balance sheet showing that the true cost of capability acquisition may be offset by the cost of capability rationalization. |
This phase provides an opportunity to validate and justify all instances of capability overlap where a preferred alternative is in place as well as where capabilities are not needed. |
Insight summary
Traditional application rationalization approaches undermine security
Methodologies that focus primarily on cost consolidation miss the mark with security tools because they don’t factor in the potential for leaving security gaps. To mitigate this risk, dissect your Microsoft security stack with a capability-first approach. This way, you expose its hidden strengths and weaknesses, allowing you to make intentional, strategic decisions about every capability, leading to cost efficiencies and a truly optimized and secure environment.
Use it or lose it
Most organizations use only a fraction of their capabilities, missing opportunities to strengthen defenses and optimize investments. Take control of your security arsenal. Dive deep into your Microsoft licenses, uncover hidden functionalities, and make informed decisions to build a truly robust and resilient security posture.
Use tool duplication to your advantage
Your security budget holds hidden potential. By identifying and divesting redundant tools, you can unlock funds to acquire critical capabilities and optimize your security posture. Transform your budget from a constraint to an enabler, strengthening your defenses without overspending.
Leave no stone unturned
Don't let Microsoft's abundance of security features become a liability. Take control of your security strategy by meticulously documenting and justifying every technology choice. This transparency eliminates ambiguity, fosters accountability, and strengthens your security posture, ensuring a strategic and defensible approach to protecting your organization.
Don’t settle for “good enough”
Microsoft's sprawling security ecosystem, while offering a wealth of capabilities, often leads to unintentional overlaps and hidden redundancies. Its "good enough" strategy can lull organizations into a false sense of security, masking the need for specialized solutions.
Intentionally assess each capability, justify your reliance on alternatives, and strategically supplement your Microsoft stack to achieve a truly robust security posture.
Knowing is half the battle
Organizations are leaving 80%-90% of their security potential on the table. This lack of awareness leads to missed opportunities, wasted resources, and increased risk. IT security leaders must prioritize understanding their full security arsenal to make informed decisions and optimize their defenses.
Blueprint deliverables
As you work through this storyboard, you will be prompted to complete activities in the Security Capability Assessment Workbook. The results of these activities are used as inputs to populate the Microsoft Security Stack Capability Report.
Security Capability Assessment Workbook
Use this tool to conduct a full capability analysis of your Microsoft security tool suite.
Microsoft Security Stack Capability Assessment Report
Distill your findings from the Security Capability Assessment Workbook into an impactful stakeholder presentation.

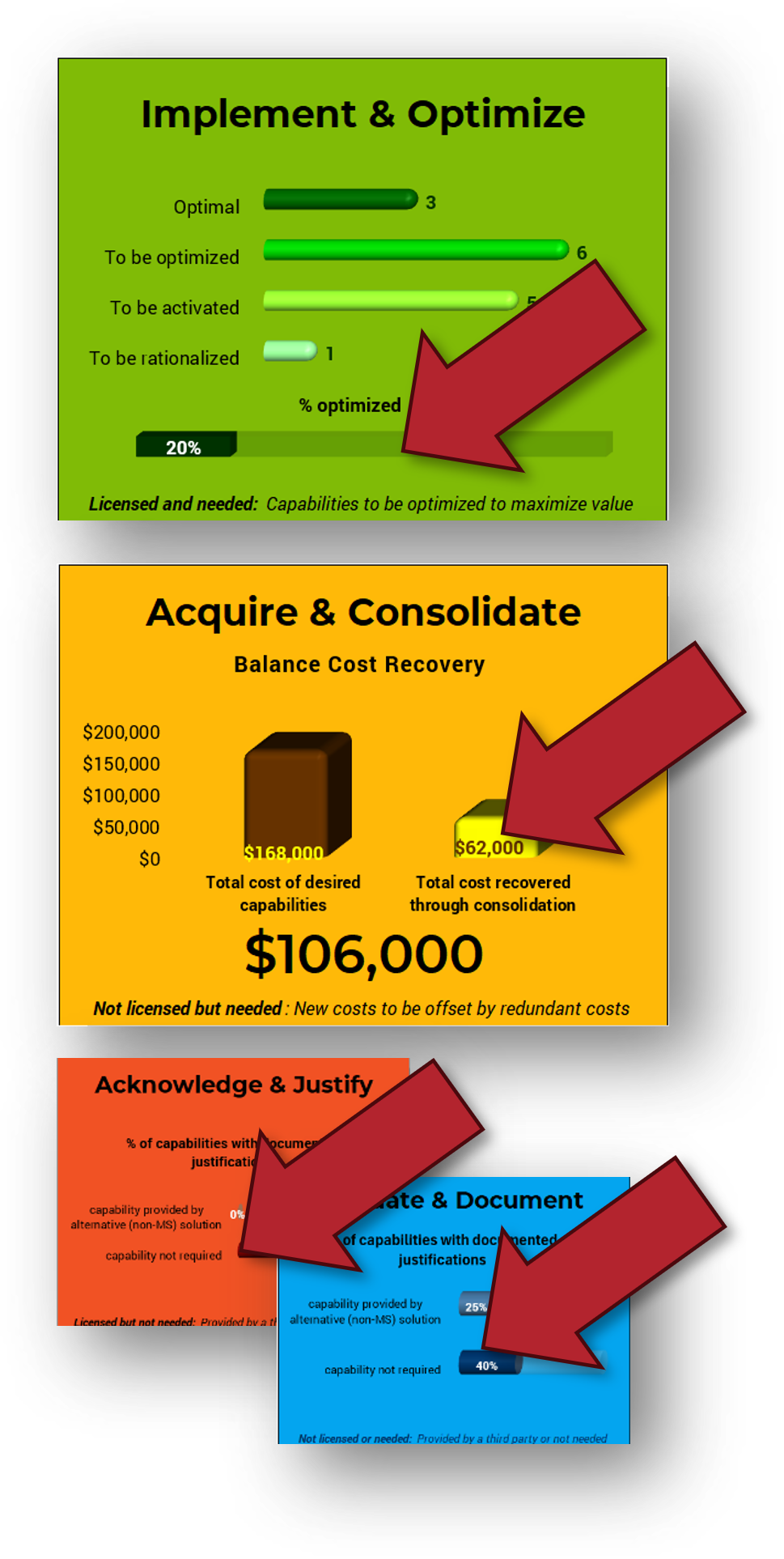
One assessment, four reports
- A report on the % of owned capabilities with a list of your justifications.
- A view of capability optimization and a plan to remediate suboptimal capabilities.
- A report on capabilities that are not needed and a list of your justifications.
- A cost recovery report that compares the cost of acquisition to recovered cost from duplication.
This unique approach to security rationalization is a win/win
|
IT Benefits |
Business Benefits |
|---|---|
|
Improved Security Posture: By identifying and addressing security gaps, optimizing tool configurations, and implementing unused capabilities, IT teams can significantly strengthen the organization's overall security posture and reduce the risk of cyberattacks. Reduced Complexity: Consolidating redundant tools and streamlining the security stack simplifies IT management, reduces administrative overhead, and improves efficiency. Enhanced Visibility and Awareness: Gaining a clear understanding of the organization's security capabilities and their utilization provides better visibility into the security landscape and enhances control over security operations. |
Reduced Costs: Consolidating redundant tools and optimizing licensing can lead to significant cost savings, allowing the organization to allocate resources more effectively. Improved Productivity: A more secure and streamlined IT environment leads to fewer security incidents and disruptions, improving employee productivity and reducing downtime. Enhanced Reputation and Trust: A strong security posture and a proactive approach to risk management can enhance the organization’s reputation and build trust with customers and partners. |
Measure the value of this blueprint with these three key metrics
|
|
Info-Tech offers various levels of support to best suit your needs
|
DIY Toolkit |
Guided Implementation |
Workshop |
Executive & Technical Counseling |
Consulting |
|---|---|---|---|---|
|
“Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful.” |
“Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track.” |
“We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place.” |
“Our team and processes are maturing; however, to expedite the journey we’ll need a seasoned practitioner to coach and validate approaches, deliverables, and opportunities.” |
“Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project.” |
Diagnostics and consistent frameworks are used throughout all five options.
Guided Implementation
What does a typical GI on this topic look like?
| Assess | Assess | Optimize | Rationalize | Justify |
|---|---|---|---|---|
|
Call #1: Scope requirements, objectives, and your specific challenges. |
Call #2: Start the capability analysis. Call #3: Review and complete the capability analysis. |
Call #4: Derive initiatives for optimization. |
Call #5: Repackage capabilities into bundles for budgeting. Call #6: Repackage overlapped capabilities into bundles for cost recovery estimates. |
Call #7: Justify preferred alternatives. Call #8: Justify unused capabilities. |
A Guided Implementation (GI) is a series of calls with an Info-Tech analyst to help implement our best practices in your organization.
A typical GI is 8 to 12 calls over the course of 4 to 6 months.
Workshop overview
Contact your account representative for more information.
workshops@infotech.com 1-888-670-8889
| Day 1 | Day 2 | Day 3 | Day 4 | Day 5 | |
|---|---|---|---|---|---|
|
Security Capability Deep Dive |
Optimize |
Rationalize |
Justify |
Steps and Wrap-Up (offsite) |
|
|
Activities |
1.1 Determine your licensed capabilities. 1.2 Assess capability status. |
2.1 Derive initiatives for optimization. 2.2 Create a roadmap/project plan for security capability optimization. |
3.1 Repackage the capabilities into bundles to be procured. 3.2 Itemize the capabilities to be consolidated. |
4.1 Justify preferred alternatives. 4.2 Justify unused capabilities. |
5.1 Complete in-progress deliverables from previous four days. 5.2 Set up review time for workshop deliverables and to discuss next steps. |
|
Deliverables |
|
|
|
|
|
Phase 1
Security Technology Capability Assessment
Assess | Optimize | Rationalize | Justify |
|---|---|---|---|
1.1 Determine your licensed capabilities 1.2 Assess your capability status | 2.1 Derive initiatives for optimization | 3.1 Repackage the capabilities into bundles to be procured 3.2 Itemize the capabilities to be consolidated | 4.1 Justify preferred alternatives 4.2 Justify unused capabilities |
This phase will walk you through the following activities:
The capability assessment activity involves a systematic review of your organization's security needs and the Microsoft technologies available to meet those needs. It includes identifying and documenting the status of each capability, determining whether it's implemented, optimized, or superseded by alternative solutions.
This process helps uncover hidden gaps, potential overlaps, and opportunities for optimization, enabling informed decision-making about your security investments and ultimately leading to a stronger and more cost-effective security posture.
Phase insight
Don’t get clouded by the productization of security tools. Traditional tool-focused evaluations miss crucial vulnerabilities and redundancies. Dissect your Microsoft security stack, analyze each capability, and compare it with alternatives. This granular approach reveals hidden opportunities to optimize your investments and build a truly robust security strategy.
Analysis at the software product level doesn’t provide a granular enough comparison
We’re not comparing apples to apples. To truly build a robust architecture, you need to decompose the products into their component capabilities.
Our capability analysis tool has done this for most Microsoft product suites
|
Defender |
Sentinel |
Entra |
Intune |
Purview |
Priva |
|---|---|---|---|---|---|
|
Capabilities include:
|
Capabilities include:
|
Capabilities include:
|
Capabilities include:
|
Capabilities include:
|
Capabilities include:
|
Microsoft’s suite may not represent an exhaustive set of capabilities
Microsoft is a fast follower, so it’s likely missing capabilities that are still in early adoption
- When using Microsoft’s portfolio as the backdrop for your security tool evaluation, keep in mind that nascent markets and leading-edge capabilities remain out of scope.
- Microsoft’s product suite has habitually only integrated features that are well developed and at parity with other like tools in the market.
- In fact, Microsoft has the effect of rapidly commoditizing certain software markets when they enter the space – a phenomenon we explore further in the research linked below.
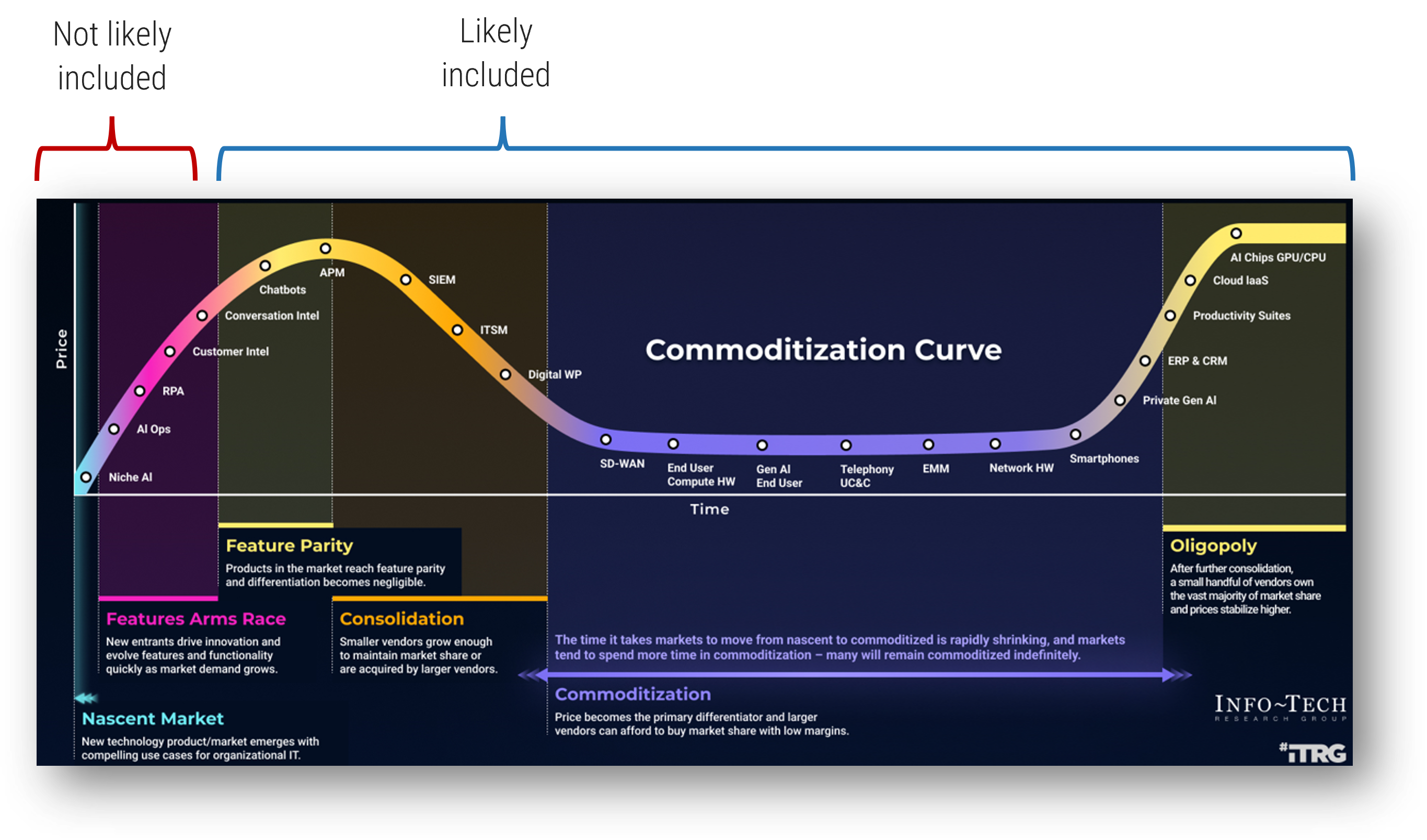
Additional Research: Stop Wasting Time Evaluating Commoditized Products and Services

 Build Your Security Operations Program From the Ground Up
Build Your Security Operations Program From the Ground Up
 Develop a Security Operations Strategy
Develop a Security Operations Strategy
 Develop and Deploy Security Policies
Develop and Deploy Security Policies
 Build an Effective IT Controls Register
Build an Effective IT Controls Register
 Select a Security Outsourcing Partner
Select a Security Outsourcing Partner
 Reinforce End-User Security Awareness During Your COVID-19 Response
Reinforce End-User Security Awareness During Your COVID-19 Response
 Cybersecurity Priorities in Times of Pandemic
Cybersecurity Priorities in Times of Pandemic
 Build a Security Metrics Program to Drive Maturity
Build a Security Metrics Program to Drive Maturity
 Build a Service-Based Security Resourcing Plan
Build a Service-Based Security Resourcing Plan
 Secure IT/OT Convergence
Secure IT/OT Convergence
 Integrate Physical Security and Information Security
Integrate Physical Security and Information Security
 Prepare for Post-Quantum Cryptography
Prepare for Post-Quantum Cryptography
 Build an Automation Roadmap to Streamline Security Processes
Build an Automation Roadmap to Streamline Security Processes
 Build an Autonomous Security Delivery Roadmap
Build an Autonomous Security Delivery Roadmap
 Build a Robust Security Architecture With Microsoft Technologies
Build a Robust Security Architecture With Microsoft Technologies
 Implement Agentic Security Operations
Implement Agentic Security Operations