- There is an onslaught of security data – generating information in different formats, storing it in different places, and forwarding it to different locations.
- The organization lacks a dedicated enterprise security team. There is limited resourcing available to begin or mature a security operations center.
- Many organizations are developing ad hoc security capabilities that result in operational inefficiencies, the misalignment of resources, and the misuse of security technology investments.
- It is difficult to communicate the value of a security operations program when trying to secure organizational buy-in to gain the appropriate resourcing.
- There is limited communication between security functions due to a centralized security operations organizational structure.
Our Advice
Critical Insight
- Security operations is no longer a center, but a process. The need for a physical security hub has evolved into the virtual fusion of prevention, detection, analysis, and response efforts. When all four functions operate as a unified process, your organization will be able to proactively combat changes in the threat landscape.
- Functional threat intelligence is a prerequisite for effective security operations – without it, security operations will be inefficient and redundant. Eliminate false positives by contextualizing threat data, aligning intelligence with business objectives, and building processes to satisfy those objectives.
- If you are not communicating, you are not secure. Collaboration eliminates siloed decisions by connecting people, processes, and technologies. You leave less room for error, consume fewer resources, and improve operational efficiency with a transparent security operations process.
Impact and Result
- A unified security operations process actively transforms security events and threat information into actionable intelligence, driving security prevention, detection, analysis, and response processes, addressing the increasing sophistication of cyberthreats, and guiding continuous improvement.
- This blueprint will walk through the steps of developing a flexible and systematic security operations program relevant to your organization.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
8.0/10
Overall Impact
$34,000
Average $ Saved
47
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
Oklahoma State University
Guided Implementation
8/10
$34,000
47
Petar was very helpful. Some of the most challenging aspects of this project was fitting the Blueprint into the higher education industry. The conc... Read More
INFO-TECH RESEARCH GROUP
Develop a Security Operations Strategy
Transition from a security operations center to a threat collaboration environment.
Info-Tech Research Group, Inc. is a global leader in providing IT research and advice. Info-Tech’s products and services combine actionable insight and relevant advice with ready-to-use tools and templates that cover the full spectrum of IT concerns.
© 1997-2017 Info-Tech Research Group Inc.
ANALYST PERSPECTIVE
“A reactive security operations program is no longer an option. The increasing sophistication of threats demands a streamlined yet adaptable mitigation and remediation process. Protect your assets by preparing for the inevitable; unify your prevention, detection, analysis, and response efforts and provide assurance to your stakeholders that you are making information security a top priority.”

Edward Gray,
Consulting Analyst, Security, Risk & Compliance
Info-Tech Research Group
Our understanding of the problem
This Research Is Designed For:
|
This Research Will Help You:
|
This Research Will Also Assist:
|
This Research Will Help Them
|
Executive summary
Situation
- Current security practices are disjointed, operating independently with a wide variety of processes and tools to conduct incident response, network defense, and threat analysis. These disparate mitigations leave organizations vulnerable to the increasing number of malicious events.
- Threat management has become resource intensive, requiring continuous monitoring, collection, and analysis of massive volumes of security event data, while juggling business, compliance, and consumer obligations.
Complication
- There is an onslaught of security data – generating information in different formats, storing it in different places, and forwarding it to different locations.
- The organization lacks a dedicated enterprise security team. There is limited resourcing available to begin or mature a security operations center.
- Many organizations are developing ad hoc security capabilities that result in operational inefficiencies, the misalignment of resources, and the misuse of their security technology investments.
- It is difficult to communicate the value of a security operations program when trying to secure organizational buy-in to gain the appropriate resourcing.
- There is limited communication between security functions due to a centralized security operations organizational structure.
Resolution
- A unified security operations process actively transforms security events and threat information into actionable intelligence, driving security prevention, detection, analysis, and response processes, addressing the increasing sophistication of cyberthreats, and guiding continuous improvement.
- This blueprint will walk through the steps of developing a flexible and systematic security operations program relevant to your organization.
Info-Tech Insight
- Security operations is no longer a center, but a process. The need for a physical security hub has evolved into the virtual fusion of prevention, detection, analysis, and response efforts. When all four functions operate as a unified process, your organization will be able to proactively combat changes in the threat landscape.
- Functional threat intelligence is a prerequisite for effective security operations – without it, security operations will be inefficient and redundant. Eliminate false positives by contextualizing threat data, aligning intelligence with business objectives, and building processes to satisfy those objectives.
- If you are not communicating, you are not secure. Collaboration eliminates siloed decisions by connecting people, processes, and technologies. You leave less room for error, consume fewer resources, and improve operational efficiency with a transparent security operations process.
Data breaches are resulting in major costs across industries

Average data breach costs per compromised record hit an all-time high of $217 (in 2015); $74 is direct cost (e.g. legal fees, technology investment) and $143 is indirect cost (e.g. abnormal customer churn). (Source: Ponemon Institute, “2015 Cost of Data Breach Study: United States”) |
 



(Source: The Network, “ Cisco 2017 Security Capabilities Benchmark Study”) |
Persistent issues
- Organizational barriers separating prevention, detection, analysis, and response efforts.
Siloed operations limit collaboration and internal knowledge sharing. - Lack of knowledgeable security staff.
Human capital is transferrable between roles and functions and must be cross-trained to wear multiple hats. - Failure to evaluate and improve security operations.
The effectiveness of operations must be frequently measured and (re)assessed through an iterative system of continuous improvement. - Lack of standardization.
Pre-established use cases and policies outlining tier-1 operational efforts will eliminate ad hoc remediation efforts and streamline operations. - Failure to acknowledge the auditor as a customer.
Many compliance and regulatory obligations require organizations to have comprehensive documentation of their security operations practices.
60% Of organizations say security operation teams have little understanding of each other’s requirements.
40% Of executives report that poor coordination leads to excessive labor and IT operational costs.
38-100% Increase in efficiency after closing operational gaps with collaboration.
(Source: Forbes, “The Game Plan for Closing the SecOps Gap”)
The solution

|
“Empower a few administrators with the best information to enable fast, automated responses.” Insufficient security personnel resourcing has been identified as the most prevalent challenge in security operations… When an emergency security incident strikes, weak collaboration and poor coordination among critical business functions will magnify inefficiencies in the incident response (IR) process, impacting the organization’s ability to minimize damage and downtime. The solution: optimize your SOC. Info-Tech has seen SOCs with five analysts outperform SOCs with 25 analysts through tools and process optimization. Sources: |
Maintain a holistic security operations program
| Legacy security operations centers (SOCs) fail to address gaps between data sources, network controls, and human capital. There is limited visibility and collaboration between departments, resulting in siloed decisions that do not support the best interests of the organization. | ||

Security operations is part of what Info-Tech calls a threat collaboration environment, where members must actively collaborate to address cyberthreats affecting the organization’s brand, business operations, and technology infrastructure on a daily basis. |
Prevent: Defense in depth is the best approach to protect against unknown and unpredictable attacks. Diligent patching and vulnerability management, endpoint protection, and strong human-centric security (amongst other tactics) are essential. | Detect: There are two types of companies – those who have been breached and know it and those who have been breached and don’t know it. Ensure that monitoring, logging, and event detection tools are in place and appropriate to your organizational needs |
| Analyze: Raw data without interpretation cannot improve security and is a waste of time, money, and effort. Establish a tiered operational process that not only enriches data but also provides visibility into your threat landscape. | Respond: Organizations can’t rely on an ad hoc response anymore – don’t wait until a state of panic. Formalize your response processes in a detailed incident runbook in order to reduce incident remediation time and effort. | |
Info-Tech’s security operations blueprint ties together various initiatives

|
Vulnerability Management
Vulnerability management revolves around the identification, prioritization, and remediation of vulnerabilities. Vulnerability management teams hunt to identify which vulnerabilities need patching and remediating. |
Deliverables
|

|
Threat Intelligence
Threat intelligence addresses the collection, analysis, and dissemination of external threat data. Analysts act as liaisons to their peers, publishing actionable threat alerts, reports, and briefings. Threat intelligence proactively monitors and identifies whether threat indicators are impacting your organization. |
|

|
Operations
Security operations include the real-time monitoring and analysis of events based on the correlation of internal and external data sources. This also includes incident escalation based on impact. Analysts are constantly tuning and tweaking rules and reporting thresholds to further help identify which indicators are most impactful during the analysis phase of operations. |
|

Develop and Implement a Security Incident Management Program |
Incident Response
Effective and efficient management of incidents involves a formal process of analysis, containment, eradication, recovery, and post-incident activities. IR teams coordinate root-cause analysis and incident gathering while facilitating post-incident lessons learned. Incident response can provide valuable threat data that ties specific indicators to threat actors or campaigns. |
|
This blueprint will…
…better protect your organization with an interdependent and collaborative security operations program.
Phase 01Assess your operational requirements. |
Phase 02Optimize and further mature your security operations processes |
Phase 3aDevelop the process flow and specific interaction points between functions |
Phase 3bTest your current capabilities with a table top exercise |
| Briefly assess your current prevention, detection, analysis, and response capabilities.
Highlight operational weak spots that should be addressed before progressing. |
Develop a prioritized list of security-focused operational initiatives.
Conduct a holistic analysis of your operational capabilities. |
Define the operational interaction points between security-focused operational departments.
Document the results in comprehensive operational interaction agreement. |
Test your operational processes with Info-Tech’s security operations table-top exercise. |
Info-Tech integrates several best practices to create a best-of-breed security framework

|
Benefits of a collaborative and integrated operations program
Effective security operations management will help you do the following:
|
ImpactShort term:
Long term:
|
Understand the cost of not having a suitable security operations program
A practical approach, justifying the value of security operations, is to identify the assets at risk and calculate the cost to the company should the information assets be compromised (i.e. assess the damage an attacker could do to the business).
| Cost Structure | Cost Estimation ($) for SMB (Small and medium-sized business) |
Cost Estimation ($) for LE (Large enterprise) |
|
| Security controls | Technology investment: software, hardware, facility, maintenance, etc.
Cost of process implementation: incident response, CMBD, problem management, etc. Cost of resource: salary, training, recruiting, etc. |
$0-300K/year | $200K-2M/year |
| Security incidents (if no security control is in place) |
Explicit cost:
|
$15K-650K/year | $270K-11M/year |
Workshop Overview
Contact your account representative or email Workshops@InfoTech.com for more information.
| Workshop Day 1 | Workshop Day 2 | Workshop Day 3 | Workshop Day 4 | Workshop Day 5 | |
| Activities |
|
|
|
|
|
| Deliverables |
|
|
|
All Final Deliverables |
Develop a Security Operations Strategy
PHASE 1
Assess Operational Requirements
1Assess Operational Requirements |
2Develop Maturity Initiatives |
3Define Interdependencies |
This step will walk you through the following activities:
- Determine why you need a sound security operations program.
- Understand Info-Tech’s threat collaboration environment.
- Evaluate your current security operation’s functions and capabilities.
Outcomes of this step
- A defined scope and motive for completing this project.
- Insight into your current security operations capabilities.
- A prioritized list of security operations initiatives based on maturity level.
Info-Tech Insight
Security operations is no longer a center, but a process. The need for a physical security hub has evolved into the virtual fusion of prevention, detection, analysis, and response efforts. When all four functions operate as a unified process, your organization will be able to proactively combat changes in the threat landscape.
Warm-up exercise: Why build a security operations program?
Estimated time to completion: 30 minutes
Discussion: Why are we pursuing this project?What are the objectives for optimizing and developing sound security operations? Stakeholders Required:
Resources Required
|
|
Info-Tech Best Practice
Don’t develop a security operations program with the objective of zero incidents. This reliance on prevention results in over-engineered security solutions that cost more than the assets being protected.
Decentralizing the SOC: Security as a function
Before you begin, remember that no two security operation programs are the same. While the end goal may be similar, the threat landscape, risk tolerance, and organizational requirements will differ from any other SOC. Determine what your DNA looks like before you begin to protect it.
Security operations must provide several fundamental functions:
|
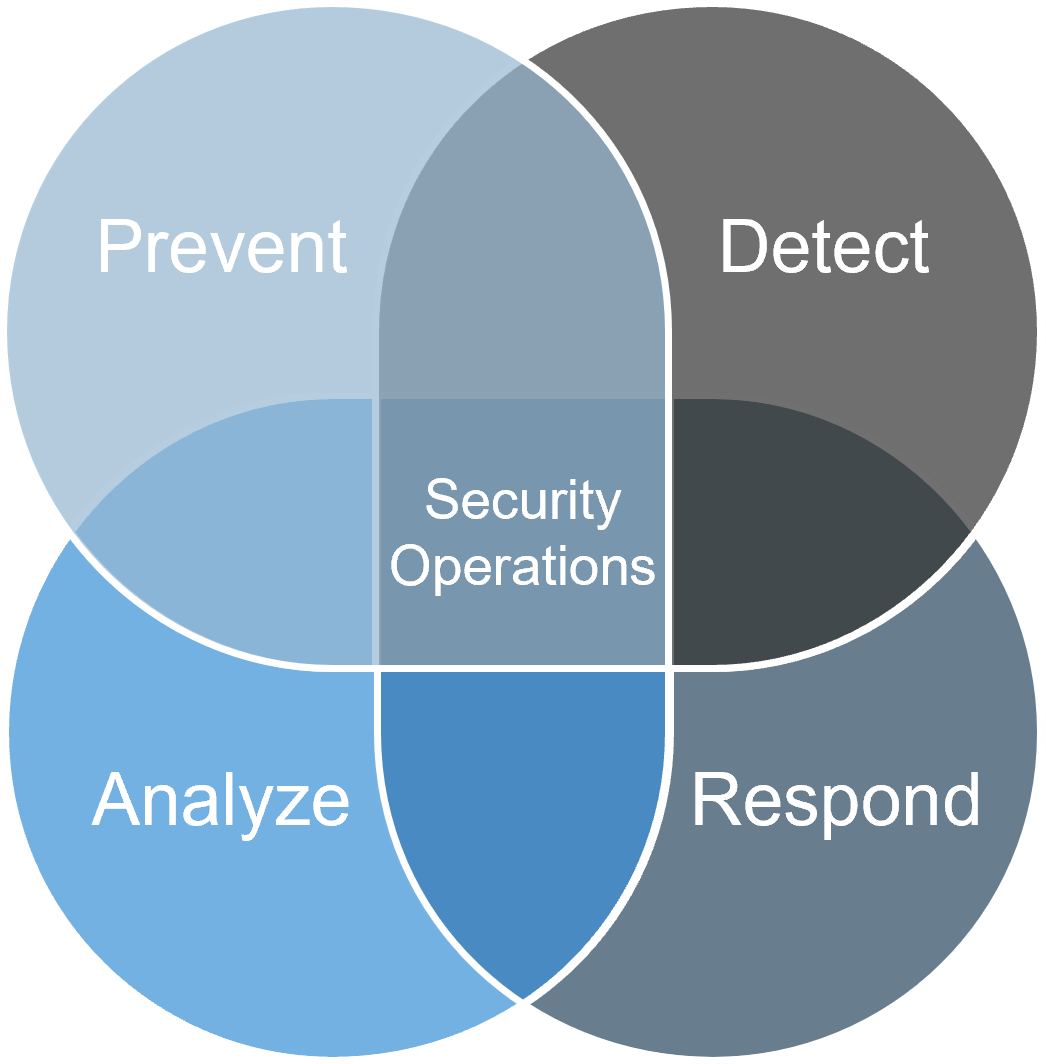 At its core, a security operations program is responsible for the prevention, detection, analysis, and response of security events. |
Optimized security operations can seamlessly integrate threat and incident management processes with monitoring and compliance workflows and resources. This integration unlocks efficiency.
Understand the levels of security operations
Take the time to map out what you need and where you should go. Security operations has to be more than just monitoring events – there must be a structured program.
| Foundational | Operational | Strategic | ||
|
|
|
||
| ——Security Operations Capabilities—–› | ||||
Understand security operations: Establish a unified threat collaboration environment
 | Security operations is part of what Info-Tech calls a threat collaboration environment, where members must actively collaborate to address threats impacting the organization’s brand, operations, and technology infrastructure.
Info-Tech Best PracticeEnsure that information flows freely throughout the threat collaboration environment – each function should serve to feed and enhance the next. | |||||
 | ||||||
 | ||||||
 Develop and Implement a Security Incident Management Program |


 Build Your Security Operations Program From the Ground Up
Build Your Security Operations Program From the Ground Up
 Develop a Security Operations Strategy
Develop a Security Operations Strategy
 Develop and Deploy Security Policies
Develop and Deploy Security Policies
 Build an Effective IT Controls Register
Build an Effective IT Controls Register
 Select a Security Outsourcing Partner
Select a Security Outsourcing Partner
 Embed Security Into the DevOps Pipeline
Embed Security Into the DevOps Pipeline
 Reinforce End-User Security Awareness During Your COVID-19 Response
Reinforce End-User Security Awareness During Your COVID-19 Response
 Cybersecurity Priorities in Times of Pandemic
Cybersecurity Priorities in Times of Pandemic
 Build a Security Metrics Program to Drive Maturity
Build a Security Metrics Program to Drive Maturity
 Build a Service-Based Security Resourcing Plan
Build a Service-Based Security Resourcing Plan
 Secure IT/OT Convergence
Secure IT/OT Convergence
 Integrate Physical Security and Information Security
Integrate Physical Security and Information Security
 Prepare for Post-Quantum Cryptography
Prepare for Post-Quantum Cryptography
 Build an Automation Roadmap to Streamline Security Processes
Build an Automation Roadmap to Streamline Security Processes
 Build an Autonomous Security Delivery Roadmap
Build an Autonomous Security Delivery Roadmap
 Build a Robust Security Architecture With Microsoft Technologies
Build a Robust Security Architecture With Microsoft Technologies
 Implement Agentic Security Operations
Implement Agentic Security Operations