Security incidents are inevitable, but how they’re dealt with can make or break an organization. Poor incident response negatively affects business practices, including workflow, revenue generation, and public image.
The incident response of most organizations is ad hoc at best. A formal management plan is rarely developed or adhered to, resulting in ineffective firefighting responses and inefficient allocation of resources.
Our Advice
Critical Insight
- Embrace the use of ready-made responses when handling incidents. These pre-established response plans can save valuable time and effort during a crisis. By relying on proven and tested procedures, your team can respond swiftly and efficiently, minimizing the impact of incidents and ensuring a consistent approach to resolving security breaches.
- Analyze, track, and review results of incident response regularly. Without a comprehensive understanding of incident trends and patterns, you can be revictimized by the same attack vector.
- Establish communication processes and channels well in advance of a crisis. Don’t wait until a state of panic. Collaborate and exchange information with other organizations to stay ahead of incoming threats.
Impact and Result
- Effective and efficient management of incidents involves a formal process of preparation, detection, analysis, containment, eradication, recovery, and post-incident activities.
- This blueprint will walk through the steps of developing a scalable and systematic incident response program relevant to your organization.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
9.6/10
Overall Impact
$34,221
Average $ Saved
28
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
Virginia Department of Health
Guided Implementation
10/10
$68,000
20
My experience has been great so far!!
City of Lynnwood
Workshop
10/10
$34,000
20
I now have clarity on who needs to make decisions between IT leadership and organizational leadership. My staff now have a detailed workflow to wor... Read More
Thompson Child & Family Focus
Guided Implementation
9/10
$6,800
10
New Brunswick Community College (NBCC)
Guided Implementation
10/10
$50,000
50
Info-Tech played a key role in shaping our incident response plans by providing valuable feedback and expert guidance throughout the process. Lever... Read More
Mustang Machinery Company, LLC
Guided Implementation
10/10
$54,400
10
Interaction with a knowledgeable resource to help guide and develop solution for our organization.
The Corporation of the City of Timmins
Guided Implementation
9/10
$27,500
10
The best part is that all runbooks are ready to be used, and the advisor is knowledgeable. The downside is that some tools contain grammatical err... Read More
St. Francis Xavier University
Guided Implementation
10/10
$37,500
16
Tohono O’Odham Gaming Enterprise dba Desert Diamond Casinos
Workshop
6/10
$13,600
10
Emphasis was placed on hitting time slots for each day's completion rather than on the accuracy and relevance of the information. This despite ulti... Read More
Government of Bermuda
Workshop
9/10
$136K
32
Best -Team collaboration Worst - Rabbit hole
Connexus Credit Union
Workshop
10/10
$34,000
26
Best part is having the whole suite of incident management references with 2 TTX's accomplished by end of workshop. Worst part is the minimal st... Read More
Meritrust Federal Credit Union
Workshop
10/10
$34,000
20
Horia was great to work with on this project.
UMWA Health and Retirement Funds
Guided Implementation
10/10
$2,584
10
I really enjoyed the interactive nature of the assistance through the case.
The President and Fellows of Harvard College, a Massachusetts nonprofit corporation, acting by and through Harvard Business School
Guided Implementation
10/10
N/A
20
Mike was awesome. He was able to help us think through how we could apply your blueprints to existing process, and was also a great sounding board... Read More
First Frame Networkers AG
Guided Implementation
9/10
$10,000
10
The State of Nevada Governor's Technology Office
Guided Implementation
10/10
$13,600
10
United Nations International Computing Centre
Guided Implementation
9/10
$21,760
14
Mike was able to immediately address our needs by providing straight to the point assistance. I would be happy to get help again in the future.
The American Institute of Architects
Workshop
10/10
$34,000
10
A big thank you to Horia for the outstanding job facilitating the security incident workshop and tabletop exercise. Your expertise and guidance mad... Read More
The City of Daytona Beach
Guided Implementation
10/10
$68,000
23
Petars insight into security and governance has really made a difference in our posture and preparedness. We can purchase solutions all day but not... Read More
Bob Barker Company, Inc.
Guided Implementation
10/10
$34,000
10
Petar Hristov did a phenomenal job of walking us through the Develop and Implement a Security Incident Management Program. His advice was extremely... Read More
Enable Ireland
Guided Implementation
10/10
$3,179
5
It was easy to engage with InfoTech. Also the security management blueprint from InfoTech was the closest to my requirements.
College of DuPage
Guided Implementation
9/10
$12,240
14
It's all laid out for you and ready to modify as needed. Our SME was very knowledgeable and patient with our team.
Government of the United States Virgin Islands
Workshop
9/10
N/A
35
The best parts of the experience was the customization of the workshop to meet our needs. This was accomplished through preparatory calls as well ... Read More
TANTUS Solutions Group Inc
Guided Implementation
8/10
$1,700
2
Intercity Transit
Guided Implementation
10/10
$34,250
10
The personal connection with an analyst.
Guelph Police Services
Workshop
9/10
$50,000
14
The best part was coming together as a consortium and forcing ourselves, with Horia's assistance to dedicate the time to complete this incredibly i... Read More
Pitt County
Guided Implementation
10/10
$32,195
10
Uganda Revenue Authority
Guided Implementation
10/10
$13,700
105
Willingness to provide guidance and followup
Opal Packaging
Guided Implementation
10/10
N/A
20
Robert is very knowledgeable providing practical advice and guidance. The facilitation of the tabletop exercise was a beneficial exercise to comple... Read More
Pitt County
Guided Implementation
10/10
$19,865
10
Keeneland Association
Guided Implementation
10/10
$2,603
2
Frank presented the materials very professioinally and shared some content he'd done for a client to help us continue down the project path.
Workshop: Develop and Implement a Security Incident Management Program
Workshops offer an easy way to accelerate your project. If you are unable to do the project yourself, and a Guided Implementation isn't enough, we offer low-cost delivery of our project workshops. We take you through every phase of your project and ensure that you have a roadmap in place to complete your project successfully.
Module 1: Prepare Your Incident Response Program
The Purpose
- Understand the purpose of incident response.
- Formalize the program.
- Identify key players and escalation points.
Key Benefits Achieved
- Common understanding of the importance of incident response.
- Various business units becoming aware of their roles in the incident management program.
- Formalized documentation.
Activities
Outputs
Assess the current process, obligations, scope, and boundaries of the incident management program.
- Understanding of the incident landscape
Identify key players for the response team and for escalation points.
- An identified incident response team
Formalize documentation.
- A security incident management charter
- A security incident management policy
Prioritize incidents requiring preparation.
- A list of top-priority incidents
- A general security incident management plan
- A security incident response RACI chart
Module 2: Develop Incident-Specific Runbooks
The Purpose
- Document the clear response procedures for top-priority incidents.
Key Benefits Achieved
- As incidents occur, clear response procedures are documented for efficient and effective recovery.
Activities
Outputs
For each top-priority incident, document the workflow from detection through analysis, containment, eradication, recovery, and post-incident analysis.
- Up to five incident-specific runbooks
Module 3: Maintain and Optimize the Program
The Purpose
- Ensure the response procedures are realistic and effective.
- Identify key metrics to measure the success of the program.
Key Benefits Achieved
- Real-time run-through of security incidents to ensure roles and responsibilities are known.
- Understanding of how to measure the success of the program.
Activities
Outputs
Limited scope tabletop exercise.
- Completed tabletop exercise
Discuss key metrics.
- Key success metrics identified
Develop and Implement a Security Incident Management Program
Create a scalable incident response program without breaking the bank.
EXECUTIVE BRIEF
Analyst Perspective
In today’s digital landscape, security incidents are an unavoidable reality for organizations, regardless of their size or industry. From data breaches and ransomware attacks to insider threats and phishing scams, the range of security incidents keeps growing. This demands a proactive and robust approach to security incidents.
It has been found that organizations with well-formalized incident response plans experience, on average, 55% lower costs and are 50% faster in containing incidents (IBM, 2020). When faced with a security incident, organizations cannot afford to waste time deliberating how to respond and must have designated roles and responsibilities so that everyone can act decisively.
As well, organizations need to track and measure key performance indicators (KPIs) such as response time, success rate, and recovery time regularly. Tracking these KPIs can provide valuable insights for continuous improvement and fine-tune response strategies.
Ultimately, a proactive security incident management approach empowers organizations to navigate security incidents with confidence and mitigate potential consequences swiftly when an incident occurs.

|
Nitin Mukesh
|
Executive Summary
Your Challenge
- Security incidents are inevitable, but how they’re dealt with can make or break an organization. A poor incident response negatively affects business practices, including workflow, revenue generation, and public image.
- The incident response of most organizations is ad hoc, at best. A formal management plan is rarely developed or adhered to, resulting in ineffective firefighting responses and an inefficient allocation of resources.
Common Obstacle
- Tracked incidents are often classified using ready-made responses that are not necessarily applicable to an organization. With so many classifications, tracking becomes inefficient and indigestible, allowing major incidents to fall through the cracks.
- As well, outcomes of incident-response tactics may not be formally tracked or communicated, resulting in the lack of a comprehensive understanding of trends and patterns regarding incidents. This may lead to an organization being revictimized by the same vector.
- However, even having a formal incident response document to meet compliance requirements is not useful if no one is adhering to it.
Info-Tech’s Approach
- Effective and efficient management of incidents involves a formal process of preparation, detection, analysis, containment, eradication, recovery, and post-incident activities.
- This blueprint will walk you through the steps of developing a scalable and systematic incident response program that is relevant to your organization.
Info-Tech Insight
Embrace the use of ready-made responses when handling incidents. These pre-established response plans can save valuable time and effort during a crisis. By relying on proven and tested procedures, your team can respond swiftly and efficiently, minimizing the impact of incidents and ensuring a consistent approach to resolving security breaches.
Challenges of inadequate security incident management
Lack of preparedness: A security incident management program helps to prepare your organization for potential security incidents by establishing clear roles, responsibilities, and procedures. Without such a program, your team may be ill-prepared to handle incidents, resulting in confusion, chaos, and a higher likelihood of errors or mistakes during the response.
Incomplete incident documentation: It is important to ensure that incidents are properly documented and there are measures for dealing with and resolving them. Without an incident management system, your organization may not have the structures to report and document incidents, which could impede root-cause identification, post-incident analysis, and the ability to learn from previous incidents in order to enhance future security measures.
Regulatory noncompliance: Some industries have specific regulations and legal requirements for incident management, data protection, and breach notification. Without an updated plan that reflects these regulations and requirements, your organization may fail to meet compilatory needs, which could lead to regulatory consequences, financial sanctions, or even a bad reputation.
207 days – Mean time to identify a data breach
70 days – Mean time to contain a data breach
(Source: “Cost of a Data Breach Report 2022,” IBM, 2022)
Defining security incident management
-
IT Incident
An IT incident is any event that is not part of the standard operation of a service and that causes, or may cause, an interruption to, or a reduction in, the quality of this service. -
Security Event
A security event is any event or occurrence that could potentially have information security implications.- For example, a spam email is a security event because it may contain links to malware.
- Organizations may be hit with thousands, or perhaps millions, of identifiable security events each day.
- These security events are typically handled by automated tools or simply logged.
-
Security Incident
A security incident is a security event that results in damage, such as lost data.- A security incident can also be a security event that does not involve damage but is a viable risk.
- For example, an employee clicking on a link in a spam email that made it through filters may be viewed as a security incident.
It’s not a matter of if you will have a security incident, but when
The increasing complexity and prevalence of threats have finally caught the attention of corporate leaders. Prepare for the inevitable with an incident response program.
- The average breach cost savings at organizations with an incident response (IR) team that tested an IR plan is US$2.66 million.
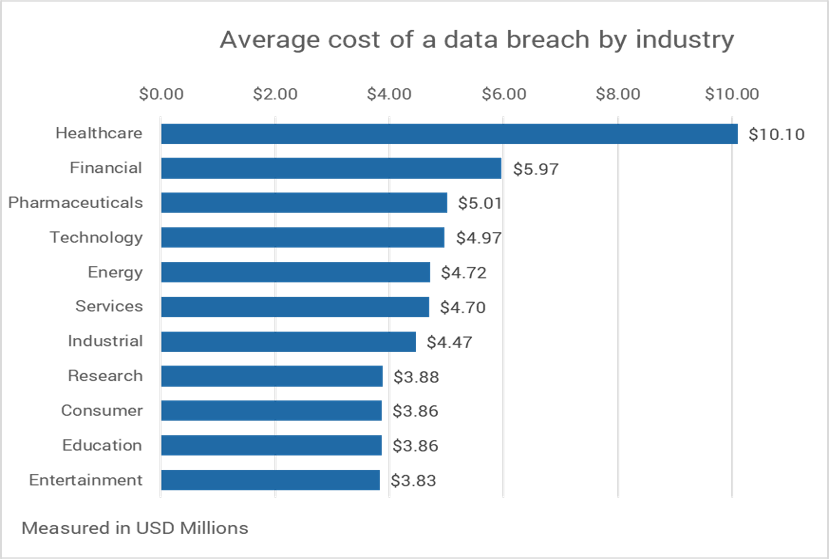
- US organizations lost an average of US$9.44 million per data breach as a result of increased customer attrition and diminished goodwill. The Middle East and Canada follow at US$7.46 and US$5.64 million, respectively.
- 83% of organizations have experienced multiple data breaches, with 60% of them having to increase the price of their services or products because of a data breach.
- 45% of breaches happened in the cloud, where organizations with a hybrid cloud model had shorter breach lifecycles than those with a private or public cloud model.
- The average cost of a data breach is greater by US$1 million if remote work was a factor.
(Source: “Cost of a Data Breach Report 2022,” IBM, 2022)
This research is designed for a chief information security officer (CISO) who is dealing with:
- Inefficient use of time and money when retroactively responding to incidents that negatively affect business revenue and workflow.
- Resistance from management to adequately develop a formal incident response plan.
- Lack of closure of incidents, resulting in being revictimized by the same vector.
This research will also assist business stakeholders who are responsible for:
- Improving workflow and managing operations in the event of a security incident to reduce any adverse business impacts.
- Ensuring that incident response compliance requirements are being adhered to.
Benefits of an incident management program
Effective incident management will help you …
- Improve efficacy.
Develop structured processes to increase process consistency across the incident response team and the program as a whole. Expose operational weak points, and transition teams from firefighting to innovating. - Improve threat detection, prevention, analysis, and response.
Enhance your pressure posture through a structured and intelligence-driven incident handling and remediation framework. - Improve visibility and information sharing.
Promote both internal and external information sharing to enable good decision making. - Create and clarify accountability and responsibility.
Establish a clear level of accountability throughout the incident response program and ensure role responsibility for all tasks and processes involved in service delivery. - Control security costs.
Establish effective incident management operations to provide visibility into your remediation processes, enabling cost savings from misdiagnosed issues and incident reduction. - Identify opportunities for continuous improvement.
Increase visibility into current performance levels and accurately identify opportunities for continuous improvement with a holistic measurement program.
Short-Term Impact
- Streamlined security incident management program
- Formalized and structured response process
- Comprehensive list of operational gaps and initiatives
- Detailed response runbooks that predefine necessary operational protocol
- Compliance and audit adherence
Long-Term Impact
- Reduced incident costs and remediation time
- Increased operational collaboration between prevention, detection, analysis, and response efforts
- Enhanced security pressure posture
- Improved communication with executives about relevant security risks to the business
- Preserved reputation and brand equity
Develop and Implement a Security Incident Management Program
Create a scalable incident response program without breaking the bank.
Create and follow a pre-established workflow for every security incident encountered
Predefined workflows for each stage
- Detection Constantly monitor until signs of an incident are detected
- Analysis Leverage data to analyze the incident
- Containment Contain the incident and affected system
- Eradication Eliminate malignant components of the incident
- Recovery Restore and monitor the affected systems
- Post-Incident Activities Collaborate with stakeholders to review the incident's cause, effect, and remediation
Embrace ready-made incident responses to save time and respond swiftly during crises. Relying on proven procedures minimizes impact and ensures consistency in resolving security breaches.
Problem
- Your organization lacks a formal and structured incident management plan or relies on one that is outdated.
- There is a reactive approach to incidents on a case-by-case basis in the absence of a standardized processes.
- The inefficient incident responses and resource allocation due to ad hoc handling of incidents result in negative impacts on critical business practices.
Challenges
- Inadequacies in incident documentation hinder post-incident analysis and learning, while the lack of a structured incident Management System impedes future security measures.
- Non-compliance risks from failure to meet data protection and breach notification requirements exposes organizations to legal and financial consequences.
- Without a security incident management program, organizations lack preparedness, clear roles, and procedures, leading to confusion and errors during incident handling.
Benefits
Control security costs
Effective incident management operations will provide visibility into your remediation processes, enabling cost savings from the reduction in misdiagnosed issues and incidents.
Improve efficacy
Develop structured processes to increase process consistency across the incident response team and the program as a whole. Expose operational weak points and transition teams from firefighting to innovating.
Impacts
Short term
- Detailed response runbooks that predefine necessary operational protocol
- Compliance and audit adherence
Long term
- Reduced incident costs and remediation time
- Enhanced security pressure posture
Malware | Malicious Email | Ransomware | Data Breach | Credential Compromise | Third-Party Incident | DDoS Attack
Maintain a holistic security operations program

Prevent: Defense in depth is the best approach to protect against unknown and unpredictable attacks. Diligent patching and vulnerability management, endpoint protection, and strong human-centric security (among other tactics) are essential.
Detect: There are two types of companies: those that have been breached and know it, and those that have been breached and don’t know it. Ensure that monitoring, logging, and event detection tools are in place and appropriate to your organizational needs.
Analyze: Raw data without interpretation cannot improve security and is a waste of time, money, and effort. Establish a tiered operational process that not only enriches data but also provides visibility into your threat landscape.
Respond: Organizations cannot rely on an ad hoc response anymore – don’t wait until a state of panic. Formalize your response processes in a detailed incident runbook to reduce incident remediation time and effort.

 Develop and Implement a Security Incident Management Program
Develop and Implement a Security Incident Management Program
 Build Resilience Against Ransomware Attacks
Build Resilience Against Ransomware Attacks
 Build a Vendor Security Assessment Service
Build a Vendor Security Assessment Service
 Implement Risk-Based Vulnerability Management
Implement Risk-Based Vulnerability Management
 Improve Organizational Resilience With a Tabletop Program
Improve Organizational Resilience With a Tabletop Program
 Master Your Security Incident Response Communications Program
Master Your Security Incident Response Communications Program
 Design a Coordinated Vulnerability Disclosure Program
Design a Coordinated Vulnerability Disclosure Program