- Mounting pressure from increasingly complex operations, a growing threat landscape, and stricter regulations are forcing leaders to bridge the gap between planning and execution.
- Failure to demonstrate operational resilience when responding to incidents, recovering systems, and continuing operations can result in significant financial and reputational damage.
- Traditional approaches to resilience planning rely on rigid playbooks, which do not impart the skills teams need to handle unexpected challenges in an actual crisis.
Our Advice
Critical Insight
- The map is not the terrain.
- A plan is not enough; you must practice it under realistic conditions. Organizations that practice their procedures have better outcomes.
Impact and Result
- Implement a structured and interactive tabletop planning program that guides organizations through exercise design, execution, and continuous improvement.
- Focus on specific objectives and measurable outcomes to assess response readiness and refine plans after each exercise.
- Build long-term resilience by regularly practicing and updating incident response, disaster recovery, and continuity plans to ensure they remain effective in evolving threat environments.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
10.0/10
Overall Impact
$16,793
Average $ Saved
14
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
Champaign Residential Services Inc
Guided Implementation
10/10
N/A
N/A
Thank you for going over the blueprint and giving me an idea of each step of the process. Looking forward to working on this in the fall :-)
New Brunswick Community College (NBCC)
Guided Implementation
10/10
$2,000
2
The guided discussions and material reviews, along with the online resources, were crucial in designing, executing, and reviewing our institution's... Read More
Long Island Power Authority
Guided Implementation
10/10
$27,880
20
Able to schedule time with experts and the. Utilize the expert as a coach to bounce back ideas.
Corporation Of The City Of Orillia
Guided Implementation
10/10
$20,500
20
Erik was great to work with and has so much knowledge. We had a quote from a third party for a table top exercise at $15,000 cdn. This saved us eno... Read More
American Bankers Association
Guided Implementation
10/10
$12,599
5
Michele was great - very flexible with his scheduling, very hands one, knowledgeable. worst part - we aren't quite done with table tops to validat... Read More
Workshop: Improve Organizational Resilience With a Tabletop Program
Workshops offer an easy way to accelerate your project. If you are unable to do the project yourself, and a Guided Implementation isn't enough, we offer low-cost delivery of our project workshops. We take you through every phase of your project and ensure that you have a roadmap in place to complete your project successfully.
Module 1: Define program objectives
The Purpose
Define program objectives.
Key Benefits Achieved
Understand program objectives.
Activities
Outputs
Define purpose and scope.
Identify program resources.
Review program criteria and milestones.
- Program charter
Review capability assessment.
- Capability assessment
Module 2: Design scenario and plan sessions
The Purpose
Design scenario and plan sessions.
Key Benefits Achieved
Complete scenario and plan for tabletop session.
Activities
Outputs
Define exercise concept.
- Exercise format and logistics
Design scenarios.
- 1-2 tabletop scenarios customized to your environment
Prepare materials.
- Completed tabletop facilitation scripts with discussion prompts and assessment metrics
Plan logistics.
Module 3: Facilitate sessions
The Purpose
Facilitate sessions.
Key Benefits Achieved
Completed tabletop sessions.
Activities
Outputs
Run sessions.
- Facilitated tabletop planning sessions with technical and leadership groups.
Document actions and decisions.
Module 4: Review outcomes
The Purpose
Review outcomes.
Key Benefits Achieved
Understand lessons and recommendations from sessions.
Activities
Outputs
Debrief sessions.
- Documented lessons learned from the sessions.
Gather program feedback.
- Feedback on the tabletop planning program.
Process improvement opportunities.
Improve Organizational Resilience With a Tabletop Program
Don’t just plan for resilience – practice it.
EXECUTIVE BRIEF
Analyst Perspective
Don’t just plan for resilience – practice it.
Organizations often find that even detailed operational resilience plans fail to translate into effective real-world responses during crises. This disconnect creates a false sense of preparedness, leaving teams vulnerable to unexpected challenges in incident response, disaster recovery, and continuity operations. The gap between planning and execution poses significant operational and reputational risk.
Bridging this gap requires a shift toward immersive, crisis-based training that fosters adaptive decision-making under pressure. Regular tabletop exercises offer teams the opportunity to move beyond rigid playbooks, honing their ability to react dynamically in complex situations. These exercises also provide a controlled environment to fail safely, extract valuable lessons, and improve response capabilities.
Don’t just plan for resilience – practice it. Implementing realistic, hands-on training will fortify your organization’s ability to manage disruptions effectively and thrive in a volatile threat landscape.

|
Michel Hébert |
Executive Summary
Your Challenge
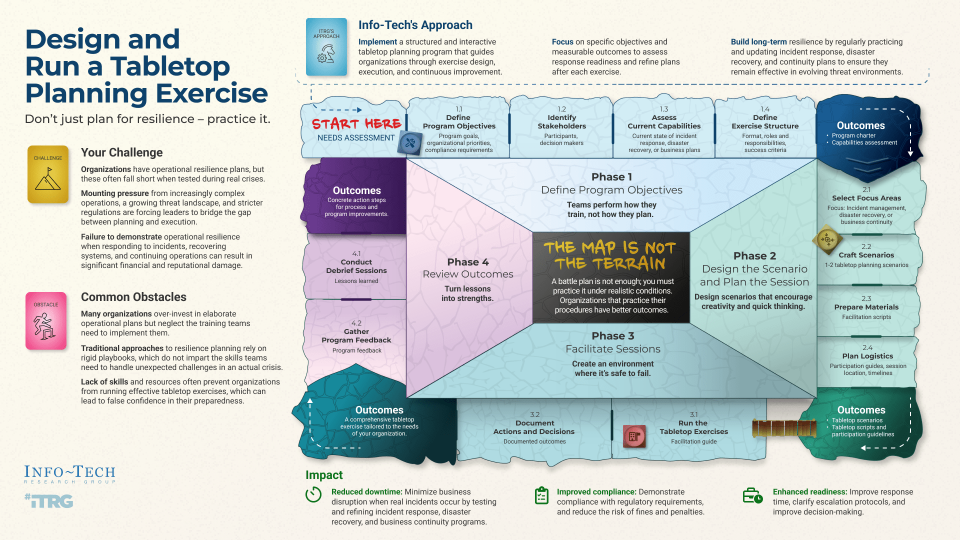
- Organizations have operational resilience plans, but these often fall short when tested during real crises.
- Mounting pressure from increasingly complex operations, a growing threat landscape, and stricter regulations are forcing leaders to bridge the gap between planning and execution.
- Failure to demonstrate operational resilience when responding to incidents, recovering systems, and continuing operations can result in significant financial and reputational damage.
Common Obstacles
- Many organizations over-invest in elaborate operational plans but neglect the training teams need to implement them.
- Traditional approaches to resilience planning rely on rigid playbooks, which do not impart the skills teams need to handle unexpected challenges in an actual crisis.
- Lack of skills and resources often prevent organizations from running effective tabletop exercises, which can lead to false confidence in their preparedness.
Info-Tech’s Approach
- Implement a structured and interactive tabletop planning program that guides organizations through exercise design, execution, and continuous improvement.
- Focus on specific objectives and measurable outcomes to assess response readiness and refine plans after each exercise.
- Build long-term resilience by regularly practicing and updating incident response, disaster recovery, and continuity plans to ensure they remain effective in evolving threat environments.
The map is not the terrain.
A plan is not enough; you must practice it under realistic conditions. Organizations that practice their procedures have better outcomes.
Your challenge
Leaders have resilience plans, but these often fall short in real crises
- Paper plans are failing. Organizations struggle to test and refine their incident response, disaster recovery, and business continuity plans. Plans might exist on paper, but they often falter when faced with an actual crisis, leading to confusion, slow decision-making, and operational losses.
- Pressure is mounting. With rising threats, stricter regulations, and increasing operational complexity, technology leaders face growing pressure to close the gap between plans on paper and actual readiness. They must demonstrate resilience by proving the organization's ability to respond effectively to cyberattacks and service outages, recover systems swiftly, and maintain business operations without interruption.
- Resources are limited. Time constraints and a lack of skilled facilitators make it difficult to establish regular, crisis-based training, gather key participants, and run effective planning exercises.
Common obstacles
Plans without practice create a false sense of preparedness
- Over-investment in planning, under-investment in training. Many organizations allocate substantial resources to developing detailed operational resilience plans but fail to provide adequate training for their teams to execute these plans effectively. Without hands-on training, teams remain unprepared for real-world scenarios, reducing the effectiveness of crisis response plans.
- Rigid playbooks hinder adaptability. Traditional resilience strategies rely heavily on inflexible playbooks that outline specific responses. However, these playbooks often do not impart the adaptive skills needed to respond to unforeseen challenges during a crisis, leaving teams vulnerable to disruptions.
- A lack of resources leads to false confidence. Insufficient skills and resources prevent many organizations from conducting regular tabletop exercises. As a result, teams may falsely believe they are prepared, without ever having tested their response strategies in practice.
Info-Tech’s approach
Level up your operational resilience training
- Structured guidance. Implement a structured and interactive tabletop planning program that walks teams through the key steps of exercise design, execution, and continuous improvement. This approach ensures that teams are systematically prepared and that each exercise builds on the lessons learned from the previous ones.
- Immersive exercises. Design and run immersive tabletop exercises to strengthen the organization’s ability to handle high-impact incidents, disaster recovery, and business continuity scenarios. These exercises foster muscle memory, ensuring teams can react effectively in real crises.
- Measurable outcomes. Focus on specific objectives and measurable outcomes during each exercise to assess response readiness. Regularly refining plans based on these assessments helps build long-term resilience, ensuring teams are better prepared for future challenges.
Before you proceed
Goals and constraints
- Choose a focus area. Start by identifying a focus area, such as incident response, disaster recovery, business continuity, or all three. For example, a ransomware scenario can comprehensively test organizational resilience, although it will challenge even the most mature teams. If you’re new to tabletop planning, it’s advisable to begin with one area and expand over time.
- Best for mature procedures. These exercises are best suited for organizations with documented procedures, such as incident response, disaster recovery, or business continuity plans. Operational maturity plays a key role in maximizing the benefits of these sessions.
- Tabletops as discovery sessions. It’s still possible to design and run a tabletop session without established operational plans. In this case, the exercise serves as a discovery process, helping you identify essential elements for plans and runbooks. This will ultimately guide you in developing more effective procedures.
Build operational resilience first
These projects will strengthen your readiness for more advanced exercises
- If your organization lacks the operational maturity, consider setting the groundwork with more foundational projects.
- The following resources can help you build a strong operational base, and at your discretion, you can incorporate a single tabletop planning session to enhance your readiness:
- If you need to develop a security incident plan, see Develop and Implement a Security Incident Management Program.
- If you need to improve the organization’s resilience to ransomware, see Build Resilience Against Ransomware Attacks.
- If you need to develop a disaster recovery plan, see Create a Right-Sized Disaster Recovery Plan.
- If you need to develop a business continuity plan, see Develop a Business Continuity Plan.
Info-Tech’s methodology to design and run a tabletop program
1. Design Program Objectives |
2. Design the Scenario and Plan the Sessions |
3. Facilitate the Sessions |
4. Identify Outcomes and Next Steps |
|
Phase Steps |
1.1 Define program objectives. 1.2 Identify participants. 1.3 Assess current capabilities. 1.4 Establish exercise format and structure. |
2.1 Select focus areas. 2.2 Design scenarios. 2.3 Prepare materials. 2.4 Plan logistics. |
3.1 Run the tabletop sessions. 3.2 Document actions and decisions. |
4.1 Debrief tabletop sessions. 4.2 Gather program feedback. |
Phase Outcomes |
|
|
|
|
Insight summary
The map is not the terrain.
A plan is not enough; you must practice it under realistic conditions. Organizations that practice their procedures have better outcomes.
Teams perform how they train, not how they plan.
There's a gap between planning and performance. Many organizations over-invest in elaborate plans but neglect practical training. Frequent, immersive exercises directly improve real-world responses.
Adaptability trumps predictability.
Traditional approaches rely on rigid playbooks, but real-time adaptability helps teams handle unexpected challenges more effectively. Design scenarios to foster creativity and quick thinking, making teams more resilient.
Failure is the best teacher if it’s safe to fail.
The most valuable insights come not from avoiding failure but from embracing failure in a controlled setting. Facilitating tabletop sessions in a way that allow teams to fail safely will create a safe space to experiment and learn, leading to more resilient systems and plans.
Turn lessons into strengths.
Review tabletop session outcomes to identify gaps and actionable insights. By refining response plans and strengthening teamwork, each lesson learned becomes a building block for greater resilience.
Blueprint deliverables
Each step of this blueprint is accompanied by supporting deliverables to help you accomplish your goals:
Key deliverable
Successful Tabletop Session
A comprehensive tabletop exercise and post-exercise debrief report, with concrete action steps for improvement.
Needs Assessment
Use the needs assessment to quickly evaluate the value and feasibility of executing a tabletop planning program.
Tabletop Program Charter
The charter is a concise, high-level document that outlines the program's purpose, goals, and scope.

Tabletop Scenario Generation Tool
The tool generates an LLM prompt based on attributes you choose. Use the prompt to generate a skeleton scenario.

Scenario Templates
A library of security incident, disaster recovery, and business continuity scenarios to inspire script design.

Tabletop Facilitation Script Template
Scenario script template to capture the scenario, run the facilitation, and capture lessons learned.

Deliverables accelerate your success
Improve Organizational Resilience With a Tabletop Program
-
START HERE:
TABLETOP SCENARIO GENERATION TOOL- Design a scenario based on your organizational context, focus area, and desired outcomes.
-
LLM
- Capture the LLM prompt from the Tabletop Scenario Generation Tool and paste it in your favorite LLM.
-
LLM
- Modify the prompt, experiment with different LLMs, and iterate until you are satisfied with the draft scenario.
-
TABLETOP SCENARIO TEMPLATE
- Capture the scenario in the Tabletop Scenario Template. Edit it until you are satisfied with the final draft.
-
OR START HERE:
PREGENERATED TABLETOP SCENARIOS- Conversely, you can choose a pre-generated tabletop scenario and edit it until you are satisfied with the draft.
-
FACILITATION SCRIPT
- Capture the scenario in the Tabletop Facilitation Script.
-
FACILITATION SCRIPT
- Facilitate the tabletop session and collect lessons learned.
Tabletops benefit IT and the business
How can you measure the business value of your tabletop planning program?
- According to IBM’s 2023 Data Breach Report, a data breach can cost an organization millions. The report also found that having a plan and regularly testing that plan is one of the most cost-effective ways to mitigate those costs.
- Cost reductions are achieved through faster response times – incident response teams detect and contain threats sooner, disaster recovery teams restore systems more quickly, and business continuity teams implement operational continuity plans more effectively.
- The return on investment (ROI) of a tabletop program can be seen in three areas:
- Financial: Savings from improved incident response, reduced downtime, and retained business.
- Time: Faster response and more efficient decision-making during crises.
- Perception: Enhanced confidence internally and externally in the organization’s preparedness and resilience.
US $4.45M — Average cost of a data breach, a 15.3% increase since 2020.
US $1.49M — Average data breach cost reduction of having a plan and testing it.
Complete a needs assessment
Assess the urgency, feasibility, and value of establishing a tabletop program at your organization
- The Rapid Needs Assessment for Tabletop Planning Programs is designed to help evaluate the benefits of creating and running a tabletop planning program in your organization.
- The assessment takes into consideration:
- Business impact alignment
- Compliance and regulatory needs
- Audit findings
- Participant readiness
- Time commitment
- Available resources
- Current capabilities
- Measurable ROI
- Customization potential
- The assessment quickly evaluates the urgency, feasibility, and value of implementing a tabletop program.

Download the Tabletop Program Rapid Needs Assessment
Measure the benefits of tabletop planning
A tabletop program will have a measurable impact on organizational resilience.
- Reduced downtime:
Mean Time to Recovery (MTTR) is a key metric here. MTTR measures the average time it takes for your team to restore normal operations after an incident. A lower MTTR directly translates into reduced downtime. - Improved compliance:
Tabletop exercises can help ensure that organizations meet regulatory compliance standards, such as SOC 2 or GDPR. A useful metric here is the number of compliance gaps identified and closed after each exercise. Regular exercises ensure that critical compliance areas are covered, reducing the risk of fines or penalties. - Enhanced readiness:
You can track Mean Time to Detect (MTTD) and Mean Time to Contain (MTTC), which measure how quickly your team can detect, acknowledge, and contain an incident. Post-exercise improvements in these times can demonstrate enhanced readiness.
Measure the value of this blueprint
How can you measure the value of following Info-Tech’s approach?
The cost and effort involved in designing and delivering a single tabletop exercise varies depending on the size and scope of the project. The average cost of a well-designed and executed tabletop exercise ranges from US $30,000 to US $45,000.
| With Info-Tech Resources | Without Info-Tech Resources | ||
Project Steps |
Time |
Average Cost (USD) |
Time |
| Pre-Tabletop Exercise Planning | 0.5-1 day | $4,000 – $6,000 | 1-5 days |
| Tabletop Exercise Scenario Design | 0.5-1 day | $10,000 - $15,000 | 14-21 days |
| Final Tabletop Exercise Logistics and Preparation | 0.5-1 day | $4,000 - $6,000 | 1-5 days |
| Tabletop Exercise Delivery | 1 day | $8,000 - $12,000 | 1-2 days |
| Post-Exercise Analysis and Recommendations | 0.5-1 day | $4,000 - $6,000 | 1-5 days |
Effort |
3-5 days |
$30,000 - $45,000 |
28-36 days |
The blueprint will accelerate the creation of your own tabletop planning program and support the delivery of tabletop exercises with guidance, tools, and templates.
Reach out to advisory services for assistance as you work through the blueprint or request a workshop engagement and let us do the heavy lifting.
Case Study

INDUSTRY: Healthcare | SOURCES: Info-Tech Engagement
A hospital designs and runs a tabletop program to improve its cyber-resilience.
Challenge
In 2022, healthcare organizations faced increasing ransomware threats as criminal syndicates stepped up attacks worldwide. Their activities lead to significant operational disruption and financial and reputational losses.
Oak Valley Health is a community healthcare organization in Ontario, Canada. They knew that the increasing risk posed a threat to their financial stability and the safety of the patients they served. The hospital partnered with Info-Tech Research Group to establish a tabletop planning program to strengthen incident response and crisis management capabilities.
Solution
Oak Valley began with a ransomware scenario targeting the internal systems that supported critical systems and housed sensitive data. Info-Tech designed the scenario, prepared participants, and facilitated the exercises. Initial sessions focused on improving response times and coordination.
Over time, the scenarios evolved to include business continuity challenges and ransomware attacks involving third-party providers, improving the organization's cybersecurity preparedness.
Results
The tabletop planning program expanded over the next two years to include scenarios of increasing complexity involving both technical and leadership teams. It significantly improved security awareness, informed better training, tools, and processes, and boosted the hospital's overall organizational resilience.
This comprehensive approach strengthened incident response, disaster recovery, and business continuity and helped safeguard patient safety by minimizing the impact of potential disruptions.
Case Study

INDUSTRY: Engineering | SOURCES: Info-Tech Engagement
An engineering firm implements tabletops to mitigate business risks.
Challenge
Kleinfelder is an engineering, construction management, design, and environmental professional services firm. As it emerged from the pandemic, the firm faced increasing cyber-threats, rising cyber-insurance costs, and strict compliance requirements. These posed security risks to its assets and client data and threatened its ability to grow the business.
The firm implemented a tabletop planning program to mitigate these critical business risks. It partnered with Info-Tech to design a tabletop program tailored to its environment and facilitate tabletop planning sessions.
Solution
The first set of sessions reviewed the firm’s incident management plan, engaged security, infrastructure, and operations teams in response exercises, and involved leadership in crisis management planning.
A customized set of scenarios simulated a cyberattack on critical systems across the firm’s many locations. The open-ended discussions encouraged adaptability and problem-solving and facilitated peer learning. The flexible approach promoted creative thinking under pressure, preparing the firm for evolving threats.
Results
The program significantly enhanced security awareness and readiness across the organization. Lessons from the technical sessions improved incident management plans and runbooks. Meanwhile, leadership tabletop exercises identified gaps in communication and business continuity plans, which led to targeted training and process updates.
The firm established an annual exercise program to anticipate emerging risks and followed up with more complex scenarios the next year.
Case Study

INDUSTRY: Higher Education | SOURCES: Info-Tech Engagement
A mature organization improves its cyber-resilience with tabletops.
Challenge
By the 2020s, ransomware attacks had become more frequent, targeted, and destructive. Recognizing the growing threat, RRC Polytech leadership classified ransomware as a critical business risk. In February 2020, Saskatchewan Polytechnic was hit by a major cybersecurity attack that shut down the school’s entire information system, highlighting vulnerabilities in the education sector.
RRC Polytech leadership tasked Information Technology Solutions with creating a tabletop planning program to strengthen its incident response and enhance its overall cybersecurity posture.
Solution
Info-Tech collaborated with RRC Polytech to strengthen its ransomware defenses. The group conducted a ransomware resilience assessment, designed a tabletop scenario aligned to the latest industry threat intelligence, and facilitated tabletop planning sessions to practice the organization’s response.
The first session refined response and recovery procedures with the IT team, while the second session focused on crisis management, communications, and business continuity planning.
Results
The tabletop planning sessions identified specific actions needed to close security gaps, improved the technical teams' readiness to execute the ransomware runbook, and heightened leadership’s understanding of ransomware risks and mitigation strategies.
Since then, RRC Polytech has committed to an annual security review process to help the organization adapt to evolving threats.

 Develop and Implement a Security Incident Management Program
Develop and Implement a Security Incident Management Program
 Build Resilience Against Ransomware Attacks
Build Resilience Against Ransomware Attacks
 Build a Vendor Security Assessment Service
Build a Vendor Security Assessment Service
 Implement Risk-Based Vulnerability Management
Implement Risk-Based Vulnerability Management
 Improve Organizational Resilience With a Tabletop Program
Improve Organizational Resilience With a Tabletop Program
 Master Your Security Incident Response Communications Program
Master Your Security Incident Response Communications Program
 Design a Coordinated Vulnerability Disclosure Program
Design a Coordinated Vulnerability Disclosure Program