- Through 2025, the chief information security officer will need to navigate emerging threats, skills shortages, and new regulations. The CEO and CIO will increasingly rely on the CISO to ensure that expected security outcomes are delivered during a time of extensive technology transformation.
Our Advice
Critical Insight
- Learn about emerging threats that will impact the business and social environment. These are shifts that change the way we interact with technology. The future-proofed CISO must learn about them and foresee the impact they will have. This report explores threats that will have a profound impact on the business and social environment in the next several years.
- Adopt emerging technology but beware the hype. Use scenario analyses for these technologies to help security teams separate fact from fiction and make informed decisions on how to leverage emerging security tech.
- Grow by delivering on outcomes. The future-proofed CISO needs to understand how to deliver on required security outcomes in a changing environment without an army of security analysts at their command.
Impact and Result
- Cybersecurity stewardship is an ever-evolving task, but you don't have to stand alone. Follow Info-Tech's learn-adopt-grow framework to confidently tackle this new challenge in security leadership.
2025 SECURITY TREND REPORT
Future-Proof the CISO
Analyst Perspective
“Artificial intelligence was going to transform IT in 1974. And in 1985. And again in 1997. And 2011.
We’ve been talking about quantum computing and forecasting the subsequent death of encryption since 1981.
The Internet of Things is over ten years old, and we’ve been predicting ransomware in our refrigerators every year since.
Security professionals love to prognosticate. However, without a structured approach for assessing the probabilities of potential scenarios, such soothsaying does little to help chief information security officers prepare for the future. Info-Tech’s 2025 Security Trend Report uses scenario analysis to present a likely outlook for cybersecurity in the year 2025 to future-proof the CISO.” (Kevin Peuhkurinen, Director, Research – Security, Info-Tech Research Group)
Introduction
New information technologies will introduce new threats. Responding to these threats will require new security skills. The scarcity of these skills will drive security leaders to embrace yet newer technologies in an attempt to fill the gap. Security failures will drive governments to introduce new regulations, further increasing the demands on already strained security teams.
To meet these challenges, the future-proofed CISO needs the best data available. The 2025 Security Trend Report synthesizes input from industry leaders and subjects it to structured scenario analysis using Info-Tech methodologies to present probable scenarios with practical recommendations.
Future-Proofing the CISO
Learn about emerging threats
Learn about new threats that will impact the business and social environment. These are shifts that change the way we interact with technology. The future-proofed CISO must learn about them and foresee the impact they will have. This report explores threats that will have a profound impact on the business and social environment in the next several years.
Adopt emerging technology, but beware the hype
This report highlights emerging technologies that can help future-proof the CISO. However, the hype around these technologies threatens to overpromise and underdeliver. We provide scenario analyses for these technologies to help security teams separate fact from fiction and make informed decisions on how to leverage emerging security tech.
Grow by delivering on outcomes
New threats and new technologies will require new security skills. Unfortunately, the security skills gap is already large and growing. The future-proofed CISO needs to understand how to deliver on required security outcomes in a changing environment without an army of security analysts at their command.
Learn About Emerging Threats
Synthetic Media In Cybersecurity in a Post-Truth World, we describe the enormous emerging security, political, social, and technological challenges associated with synthetic video and audio. Deepfake and related technologies have already been used to augment social engineering attacks, and they threaten to do much more. |

Cloud Misconfigurations Cloud computing may prove to be the greatest disruptor of traditional information technology yet seen. However, the rush to the cloud could be the undoing of many companies. In Cloud First, Security Third?, we look at the significant challenges facing security teams as their businesses chase their place in the sky. |

5G-Enabled IoT 5G networking has the capability of actually improving cybersecurity. However, before we can take advantage of it, we need to face hard facts about IoT security as our cars, thermostats, and manufacturing robots move to the edge. When IoT Met 5G explores the road ahead for this important new technology. |
Adapt to Emerging Trends
New Regulations In the new business world, the only certainties are taxes and compliance obligations. Drowning in Regulations looks at how new cybersecurity and privacy laws and regulations will drive changes to all organizations and what that means to security teams. |

Security AI In Security Team 2.0, we look at the ever- growing chasm in cybersecurity skills. Faced with new threats, new technologies, and new compliance obligations, security leaders will need to make hard decisions. If you can’t hire people, can you replace them with robots? |
Cybersecurity in a Post-Truth World
When seeing isn’t believing
14,678 deepfake videos online as of September 2019 (source: DeepTrace, 2019) |
Is weaponized artificial intelligence our greatest cyber threat yet?In 2015, when an innovative criminal donned a latex mask of French defense minister Jean-Yves Le Drian and conned wealthy patriots out of €80 million, they were unknowingly foreshadowing a much larger problem to come. However, even when the first deepfake video appeared in 2017, the cybersecurity implications were not front of mind for most people. The first real implications came to be felt only in March 2019 when cybercriminals used synthetic voice audio to help steal $243,000 from a UK energy company. What does authentication mean in a post-truth world? |
Signals and DriversThe main driver for Cybersecurity in a Post-Truth World will be the effectiveness of social engineering attacks based on machine learning and artificial intelligence, including generative adversarial network techniques such as deepfake. Of course, the problem of synthetic media is far wider and deeper than just cybersecurity. This fact is reflected by the large sums of money being spent to fund deepfake detection tools. |
96% of all online deepfake videos are pornographic in nature 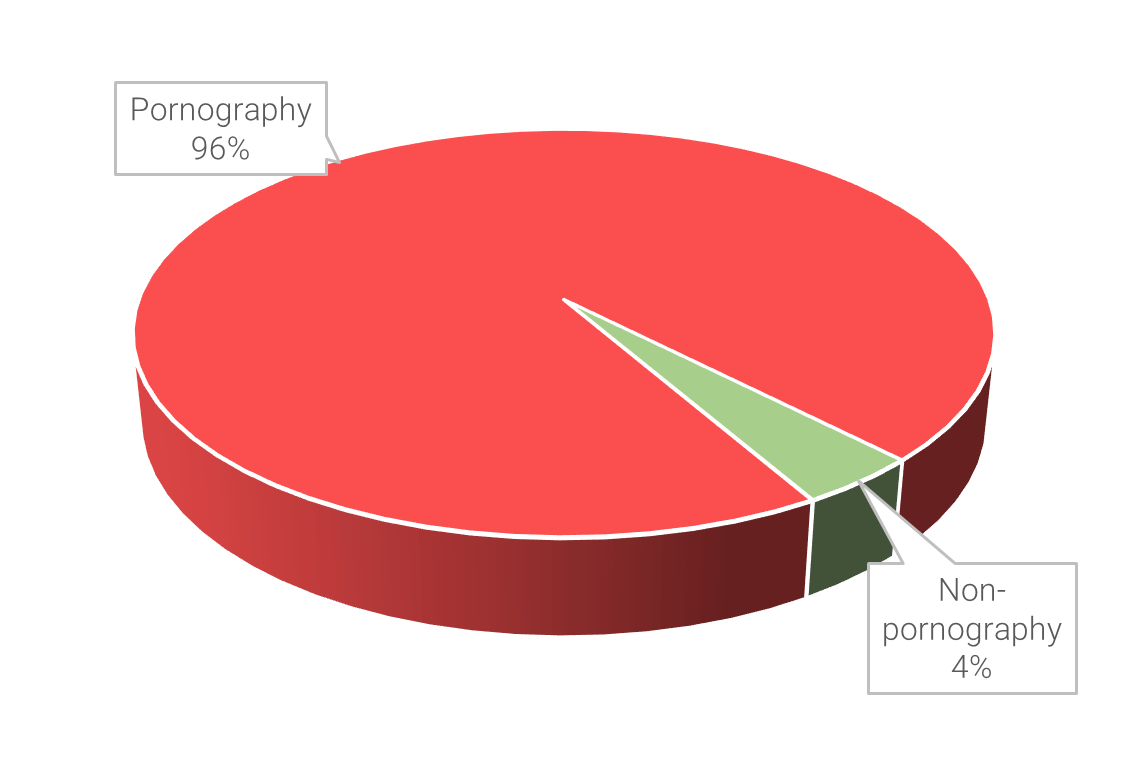 source: DeepTrace, 2019 $68,000,000 spent by DARPA on deepfake detection technology in 2018 (source: futurism, 2018) |
$243,000 amount stolen using synthetic voice audio in one 2019 incident (source: DeepTrace, 2019) $10,000,000 contributed by Facebook for the Deepfake Detection Challenge (source: Facebook, 2019) |
Critical Uncertainties
Innovation in AI-based social engineering attacks
Social engineering attacks are certain to remain a threat over the next five years. The introduction of machine learning and artificial intelligence will be a force multiplier for this threat, as we have already seen with the use of deepfake to augment traditional business compromise email attacks.
However, the real danger is that AI will become a true disruptor, allowing innovative criminals to invent entirely new social engineering attacks for which we have no defenses.
Effectiveness of detection and prevention controls
Governments and industries are profoundly concerned with the implications of deepfake and related technologies for good reasons that include but go far beyond cybersecurity. They are investing significant sums of money to fund detection tools. Fortunately, any progress that is made on this problem should benefit cybersecurity.
Nevertheless, detection is a huge challenge and there is plenty of uncertainty about how effective these tools will prove. Deepfake algorithms will almost definitely continue to improve, and it will become harder and harder to determine with absolute confidence whether any particular video or audio is real or fake.
“How are we going to believe anything anymore that we see? To me that’s a real threat to our democracy.” (Hany Farid, Professor, University of California, Berkeley, source: the wall street journal, 2018)
Scenario: Strong innovation by criminals in their use of deepfake-enabled social engineering attacks combined with a lack of effective security controls will pose a colossal challenge for all organizations. Response: Combating this threat without effective technology controls will require most organizations to implement much stronger manual process controls for critical transactions. |
Innovation in AI Attacks: High |
Scenario: Criminals continually innovate in their use of synthetic media in social engineering attacks. However, detection and prevention controls prove highly effective in combating these attacks. Response: Organizations that understand the threat and implement effective controls early should largely mitigate the risk. Those that don’t may find themselves facing an existential threat. |
||
| Effectiveness of Controls: Low |
Scenario Analysis |
Effectiveness of Controls:
High |
||
Scenario: Lack of innovative AI-based attacks coupled with poor detection controls will be a status quo scenario. Synthetic media will be primarily used for pornographic purposes but may occasionally pose a cybersecurity threat as well. Response: For cybersecurity teams already struggling with social engineering attacks, deepfake technology will become another headache. Security awareness programs will need to become a focus. |
Innovation in AI Attacks: Low |
Scenario: The use of synthetic media in social engineering attacks remains fairly static, likely due to limitations of the technology. Highly effective detection controls significantly mitigate the risk to most organizations. Response: Deepfake technology use remains largely restricted to pornography. While still a huge public policy and privacy challenge, the cybersecurity risk fades. |
||
Probable Scenario
“The weaponization of deepfakes and synthetic media is influencing the cybersecurity landscape, enhancing traditional cyber threats and enabling entirely new attack vectors.” (Giorgio Patrini, Founder, CEO, and Chief Scientist, DeepTrace, source: DeepTrace, 2019)
The most probable 2025 scenario for Cybersecurity in a Post-Truth World is that improvements in real-time deepfake and related technologies will significantly outpace detection efforts.
Vast sums have already been spent by governments and industry to develop detection technologies, and this investment will very likely increase considerably. However, the technical problem of deepfake improvement is currently smaller than that of detection; small improvements in synthetic media will require exponentially larger improvements in detection to counter.
Even when or if effective detection controls are developed, there will be huge challenges with deployment. Potential victims can be exposed to synthetic media through many different vectors, and ensuring that detection controls protect all vectors will be a significant undertaking.
Over the longer term, raised awareness of the threat among the general populace may prove to be the most effective defense. However, this is unlikely to occur before 2025.
Recommendations and Resources
Recommendations:
- Organizations of all sizes should assess their exposure to AI-enabled social engineering attacks.
- Variations on existing social engineering attacks, especially business compromise emails and ransomware delivery, should be expected to emerge first.
- Synthetic voice attacks against call centers, even those that use voice biometrics for authentication, are very likely by 2025.
- Other critical business transaction points should be assessed for their vulnerability to deepfake technologies.
- Additional authentication procedures should be considered to mitigate identified vulnerabilities. These should be augmented with the inclusion of deepfake awareness in most security training programs.
Info-Tech Research Group Resources:
Cloud First, Security Third?
Around every silver lining, there's a dark cloud

990,000,000 records exposed due to misconfigured cloud security in 2018 alone (source: IBM Security, 2019) |
Can cloud security tools save us from ourselves?In the early days of cloud computing, security teams were primarily worried about Software as a Service (SaaS) and whether vendors could be trusted to properly protect data. These concerns soon faded as organizations came to realize that, in most cases, their on-premises cybersecurity was actually inferior to what SaaS providers offered. However, as cloud adoption has moved from SaaS to Infrastructure as a Service (IaaS) and Platform as a Service (PaaS), new security concerns are emerging. Unlike SaaS, using IaaS and PaaS requires that organizations properly configure the security of their cloud systems. Failure to do so is fast becoming a significant risk, but will we pause long enough in our rush to the cloud to learn how to secure it? |
Signals and DriversThe main driver for Cloud First, Security Third will be the increasing number of companies adopting a “cloud-first” or “cloud-only” strategy. Even without a cloud-first strategy, many organizations will continue to move workload to the cloud, increasing their exposure. The complexity of properly securing cloud instances is expected to increase, while the availability of appropriately skilled resources to do the work will remain scarce. However, the Capital One breach in 2019 reminds us of the potentially huge costs of making a mistake with cloud security. | $150 million estimated direct costs in 2019 from Capital One cloud misconfiguration data breach (source: fortune, 2019) 39% of companies have adopted a cloud-first strategy as of 2019 (source: Flexera, 2019) | $12.6 billion estimated global spend on cloud security tools by 2023 (source: dark reading, 2019) |
Critical Uncertainties
Availability of effective cloud security tools
The market for cloud security tools is booming but still very immature. Most cloud vendors offer many security features, but they tend to be very complex and require highly skilled technical professionals to fully utilize. Feature sets and configuration options vary significantly among vendors, making life even more difficult for security teams at organizations with multi-cloud strategies.
There is significant uncertainty whether truly comprehensive security tools that can automate best-practice security configurations across multiple cloud providers will emerge over the next few years.
Public cloud adoption
It is certain that organizations will continue their migration toward cloud computing. While all signs point toward expanding use of public cloud environments, it is possible that this trend will slow. In this case, investment may shift toward private cloud.
Another key uncertainty will be whether organizations continue to prefer multi-cloud strategies or move toward single clouds. This may affect whether organizations look to the cloud vendor for security tools or select pure-play security vendors instead.
“We [Capital One] don't start using a service just because it's announced and it's cool. We start using it when we are sure we can meet security and other commitments we have internally.” (Bernard Golden, VP, Cloud Strategy, Capital One, December 2018, source: fortune, 2019)
Scenario: Continued cloud-first adoption combined with a dearth of security tools will leave millions of records exposed. Response: Organizations moving toward cloud first will need to seriously consider whether they have the in-house expertise required to properly secure their cloud assets. Lack of tools may drive more organizations toward private cloud. | Cloud Adoption: High | Scenario: Companies continue to adopt cloud-first and cloud-only strategies. Fortunately, comprehensive security tools become widely available to help organizations manage their cloud risks. Response: While organizations will be free to pursue public/private cloud and single-/multi-cloud strategies, security tools will need to factor into overall cloud cost optimization plans. | ||
| Availability of Cloud Security Tools: Low | Scenario Analysis | Availability of Cloud Security Tools: | ||
Scenario: Lack of effective cloud security tools may lead to slower cloud adoption for some organizations. Response: Developing a cloud security strategy and architecture in the absence of effective tools may be a competitive advantage, allowing more organizations to securely embrace new cloud strategies. | Cloud Adoption: Low | Scenario: Slowed cloud adoption combined with the availability of effective cloud security tools will drive down the costs of those tools. Response: With plenty of options to choose from, organizations will want to strategize whether to adopt a comprehensive set of security tools from their cloud vendor or select a pure-play security vendor. | ||
Probable Scenario
“And then I hack into their ec2 instances, assume-role their IAM instance profiles, take over the account and corrupt SSM, deploying my backdoor, mirror their s3 buckets, and convert any snapshots I want to volumes and mirror the volumes I want via storage gateway” (June 16, 2019, post by “erratic,” the Twitter handle of Paige Thompson, accused in the Capital One data breach)
The most probable 2025 scenario for Cloud First, Security Third is that organizations will continue to migrate data to the cloud faster than they can secure it. Programs such as FedRAMP in the US have helped ensure that cloud infrastructure itself is secure, but in IaaS and PaaS models, customers are still responsible for the security of their applications and middleware.
Properly securing cloud data requires highly specialized security skills. As we will see in Security Team 2.0, the enormous security skills gap is only likely to get wider. In the absence of cloud security specialists, most organizations will need to look toward cloud security tools to support their cloud strategies. Organizations that rush ahead into the cloud without either the right security skills or tools may quickly find their expected cost optimizations to vanish into data breach expenses.
A shift away from public cloud toward private cloud may partially alleviate the security risks, but there is no indication that this will happen to any great extent. Additionally, there is no guarantee that private cloud will prove more secure than public cloud over the long term.
Recommendations and Resources
Recommendations:
- Organizations need to develop a structured cloud security architecture that aligns with their overall cloud strategy.
- As part of their architecture development, organizations should consider the skills required to implement necessary controls. Plans for addressing identified gaps against current skill sets should be determined and consider training, outsourcing, or tooling.
- Costs to properly secure cloud systems should be incorporated into overall cloud cost optimization plans.


 Design and Implement a Business-Aligned Security Program
Design and Implement a Business-Aligned Security Program
 Build an Information Security Strategy
Build an Information Security Strategy
 Secure Operations in High-Risk Jurisdictions
Secure Operations in High-Risk Jurisdictions
 Develop a Security Awareness and Training Program That Empowers End Users
Develop a Security Awareness and Training Program That Empowers End Users
 Build, Optimize, and Present a Risk-Based Security Budget
Build, Optimize, and Present a Risk-Based Security Budget
 Hire or Develop a World-Class CISO
Hire or Develop a World-Class CISO
 Fast Track Your GDPR Compliance Efforts
Fast Track Your GDPR Compliance Efforts
 Build a Cloud Security Strategy
Build a Cloud Security Strategy
 Identify the Components of Your Cloud Security Architecture
Identify the Components of Your Cloud Security Architecture
 Security Priorities 2022
Security Priorities 2022
 2020 Security Priorities Report
2020 Security Priorities Report
 Manage Third-Party Service Security Outsourcing
Manage Third-Party Service Security Outsourcing
 Select a Security Outsourcing Partner
Select a Security Outsourcing Partner
 Improve Security Governance With a Security Steering Committee
Improve Security Governance With a Security Steering Committee
 The First 100 Days as CISO
The First 100 Days as CISO
 Determine Your Zero Trust Readiness
Determine Your Zero Trust Readiness
 Cost-Optimize Your Security Budget
Cost-Optimize Your Security Budget
 Threat Preparedness Using MITRE ATT&CK®
Threat Preparedness Using MITRE ATT&CK®
 Build a Zero Trust Roadmap
Build a Zero Trust Roadmap
 Security Priorities 2023
Security Priorities 2023
 Security Priorities 2024
Security Priorities 2024
 Grow Your Own Cybersecurity Team
Grow Your Own Cybersecurity Team
 Security Priorities 2025
Security Priorities 2025
 Create a Zero Trust Implementation Plan
Create a Zero Trust Implementation Plan
 Build Adaptive Security Services
Build Adaptive Security Services
 Run IT By the Numbers
Run IT By the Numbers
 Transform IT, Transform Everything
Transform IT, Transform Everything
 The Race to Develop Talent
The Race to Develop Talent
 Assessing the AI Ecosystem
Assessing the AI Ecosystem
 Bring AI Out of the Shadows
Bring AI Out of the Shadows
 IT Spend and Staffing Benchmarking
IT Spend and Staffing Benchmarking
 The Security Playbook
The Security Playbook
 Security Priorities 2026
Security Priorities 2026