AI-assisted coding, API-driven systems, and fast-moving delivery cycles have made applications the number one target for security threat actors – and traditional secure software development lifecycles (SSDLCs) are too rigid and siloed to keep pace. This comprehensive blueprint offers an intelligent, capabilities-driven SSDLC framework that will embed security in every stage of the lifecycle.
Generative AI coding and other emerging technologies have strained SSDLCs – but they also stand to make them more adaptive, with the aid of a mix of autonomous and manual practices. Security leaders must coordinate a strategy among security, application, and product leaders that aligns with organizational priorities, optimizes investment, and ensures security, development, and operations teams work together as one.
1. Security should be an enabler, not a roadblock.
Modern development moves fast – and, if it is to keep pace with emerging threats, so must security. Intelligent, adaptive capabilities aligned to organizational priorities can help eliminate bottlenecks and enable teams to deliver at scale. When embedded effectively, security becomes an accelerant, not a delay.
2. Let your gaps guide your investments.
Not all application security improvements are equal or useful to the organization. A structured capability assessment can reveal where maturity is lacking so you can focus resources on initiatives with the highest risk reduction and greatest organizational value.
3. Security is a shared responsibility.
Effective application security depends as much on people and expertise as it does on tools. Embedding secure practices early requires tight collaboration across security, development, and operations teams. This cross-functional coordination reduces risk, improves consistency, and accelerates delivery.
Use this step-by-step blueprint to enable an intelligent application security program
Our practical research offers valuable tools and templates to help you modernize your secure software development practices to face modern challenges and align them with organizational goals. Use this step-by-step framework to understand your current state, prioritize improvements, and build an application security program that is equipped to withstand today’s threats and tomorrow’s challenges.
- Prioritize iSSDLC capabilities by defining organizational opportunities supported and security threats mitigated, and establish key metrics and defined governance practices.
- Define your target state by assessing current application security maturity levels.
- Develop your strategic plan by listing your prioritized application security initiatives and developing and communicating your roadmap.
Develop a Strategic Plan for Intelligent Application Security
Plan for an intelligent SSDLC to build smarter, faster, and more resilient solutions.
Analyst perspective
Confidently deliver your solutions through intelligent secure software.
With the rise of emerging technologies and increased attacks on applications, traditional secure software development lifecycles (SSDLCs) are no longer sufficient to safeguard applications. Conventional approaches are often rigid, heavily manual, and misaligned with the pace of digital innovation, leading to inconsistent controls and security debt across the software supply chain.
The solution is to rethink application security through a capabilities-driven lens that aligns to real-world business priorities and emerging threat realities.
By conducting a structured capabilities assessment, organizations can identify maturity gaps, align security to key SDLC phases, and prioritize improvements based on the highest business value and risk mitigation. The introduction of an intelligent, risk-aligned maturity model — backed by metrics and executive-level insights — enables security leaders to evolve AppSec practices without hindering innovation.
Building a scalable and adaptive application security program through an intelligent approach positions security as a business enabler. It strengthens foundational practices, increases development velocity, and ensures resilience across modern development pipelines — empowering organizations to deliver securely, at scale.

Ahmad Jowhar
Research Analyst, Security & Privacy Practice
Info-Tech Research Group
Executive summary
Your Challenge
Emerging trends in application development pose new challenges for cybersecurity:
- Generative AI coding accelerates development, stressing manual security reviews.
- The need for new agentic AI applications creates a need for new security oversight.
- Attack surfaces are increasingly shifting to applications and APIs, creating new threats and evolving attack vectors.
Common Obstacles
- Conventional secure software development lifecycles fail to deliver on their promises. Rooted in waterfall bureaucracy, their inflexibility inevitably leads to decay.
- Lack of a prioritization process exacerbates the challenges of effectively addressing and mitigating application-based vulnerabilities.
- Integrating security, application, and operations teams remains a significant challenge for many organizations.
Info-Tech’s Approach
- Autonomous code development requires autonomous security capabilities, delivered as part of an intelligent secure software development lifecycle (iSSDLC).
- Leverage a best-of-breed capabilities assessment to evaluate the maturity of your application security practices.
- Develop a structured roadmap with defined roles and responsibilities for achieving your desired application security maturity state.
Info-Tech Insight
Shift security from a roadblock to a growth accelerant. Intelligent, adaptive security capabilities — aligned to enable top business opportunities and mitigate the most critical threats — unlock the full speed and value of modern application delivery.
Challenge
Poor application security practices expand an organization’s threat landscape.
- The rise of emerging technologies is driving the need to develop applications more efficiently and at greater scale, straining traditional development processes.
- As applications and APIs become fundamental to digital services, they represent a growing portion of the threat landscape, making them key targets for attackers.
- Traditional security practices struggle to keep up with modern application development and its associated threats, highlighting the need for more adaptive and application-focused security strategies.
- As the urgency to leverage emerging technologies increases, unresolved vulnerabilities and ad hoc security practices accumulate, creating a growing backlog that threatens long-term resilience for organizations.
80% 80% of top breaches were related to application attack surfaces. (Source: “2024 State of Application Security Report”, CrowdStrike, 2024)
92% 92% of organizations had a breach due to an application they developed. (Source: “The Future of Application Security 2024,” Checkmarx, 2024)
49% There was a 49% year-over-year increase in web application attacks from 2023 to 2024. (Source: “Application Security Report 2024,” Akamai, 2025)
Common obstacles
Organizations lack guidance to mature their application security program.
- Current application security guidelines often fail to offer a clear, phased approach for evaluating and maturing secure coding practices across the development lifecycle.
- Without a risk-based prioritization model that encompasses business opportunities and security threats, teams struggle to focus on vulnerabilities that pose the greatest threat, leading to inefficient mitigation efforts.
- Security, development, and delivery teams frequently operate in silos, making it difficult to embed secure coding practices consistently across workflows.
- Organizations may adopt security tools without aligning them to existing pipelines or developer workflows, resulting in poor adoption and inconsistent coverage.
30% Only 30% of organizations have a mature DevSecOps program. (Source: “DevSecOps Evolution,” Checkmarx, 2025)
54% Only 54% of major code changes go through full security reviews. (Source: “2024 State of Application Security Report”, CrowdStrike, 2024)
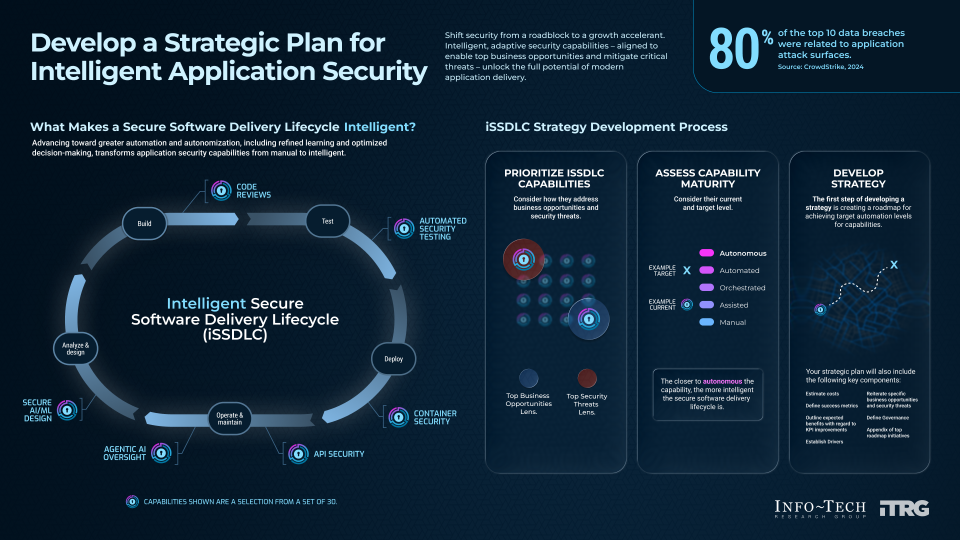
Info-Tech’s methodology for modernizing your application security services
1. Prioritize iSSDLC capabilities. | 2. Assess maturity. | 3. Develop a strategic plan. | |
Phase Steps |
|
|
|
Phase Outcomes |
|
|
|
Insight summary
Remove the security roadblocks.
Shift security from a roadblock to a growth accelerant. Intelligent, adaptive security capabilities — aligned to enable top business opportunities and mitigate the most critical threats — unlock the full speed and value of modern application delivery.
Cross-functional collaboration drives security success.
Effective application security demands more than tools — it requires a shared ownership that aligns security, development, and operations teams to ensure secure practices are embedded early, which will enable faster delivery and reduce risks.
High-impact investments derive from capability gaps.
Assessment of your security capabilities exposes gaps in critical areas such as CI/CD security and software supply chain integrity, which enables organizations to prioritize efforts.
Secure development is not only a technical function.
Security must be integrated into an SDLC from architecture to operations. It must contain a structured process that supports governance, accountability, and culture.
Balance automation with expertise.
Although automation accelerates scale, other capabilities thrive on human expertise and context, which promotes a balanced approach to combine intelligence tooling with strategic human oversight.
Empower developers to build securely from the start.
Security shouldn’t slow down development but rather streamline it with clear guidelines and embedded controls.
Blueprint deliverables
Key deliverables:
iSSDLC Strategy Deck
Communication deck to present your iSSDLC strategy to key stakeholders to obtain buy-in and support for your application security improvement plan
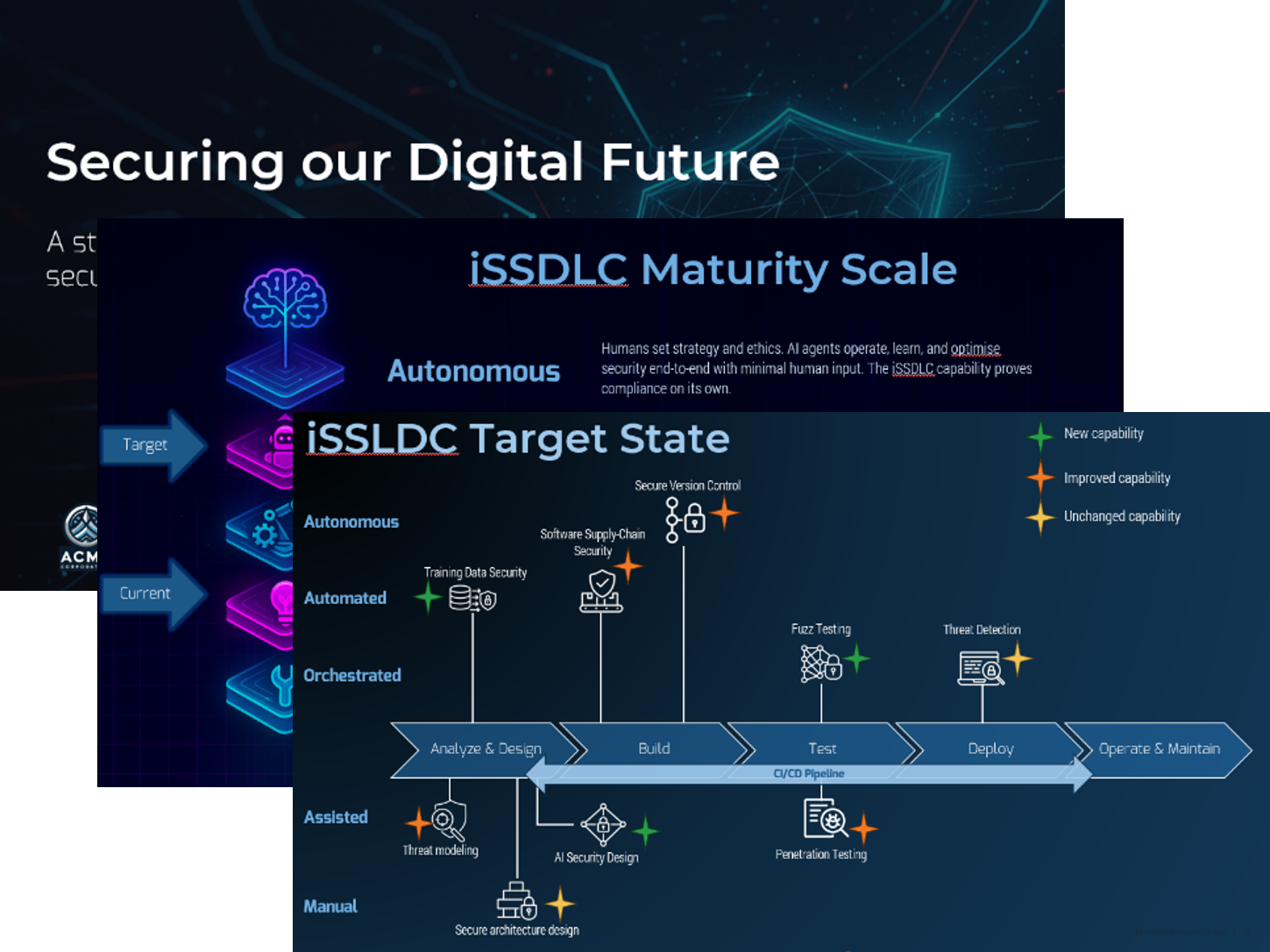
Each step of this blueprint is accompanied by supporting deliverables to help you accomplish your goals:
iSSDLC Capabilities Assessment Tool
Assessment tool to develop your application security improvement plan
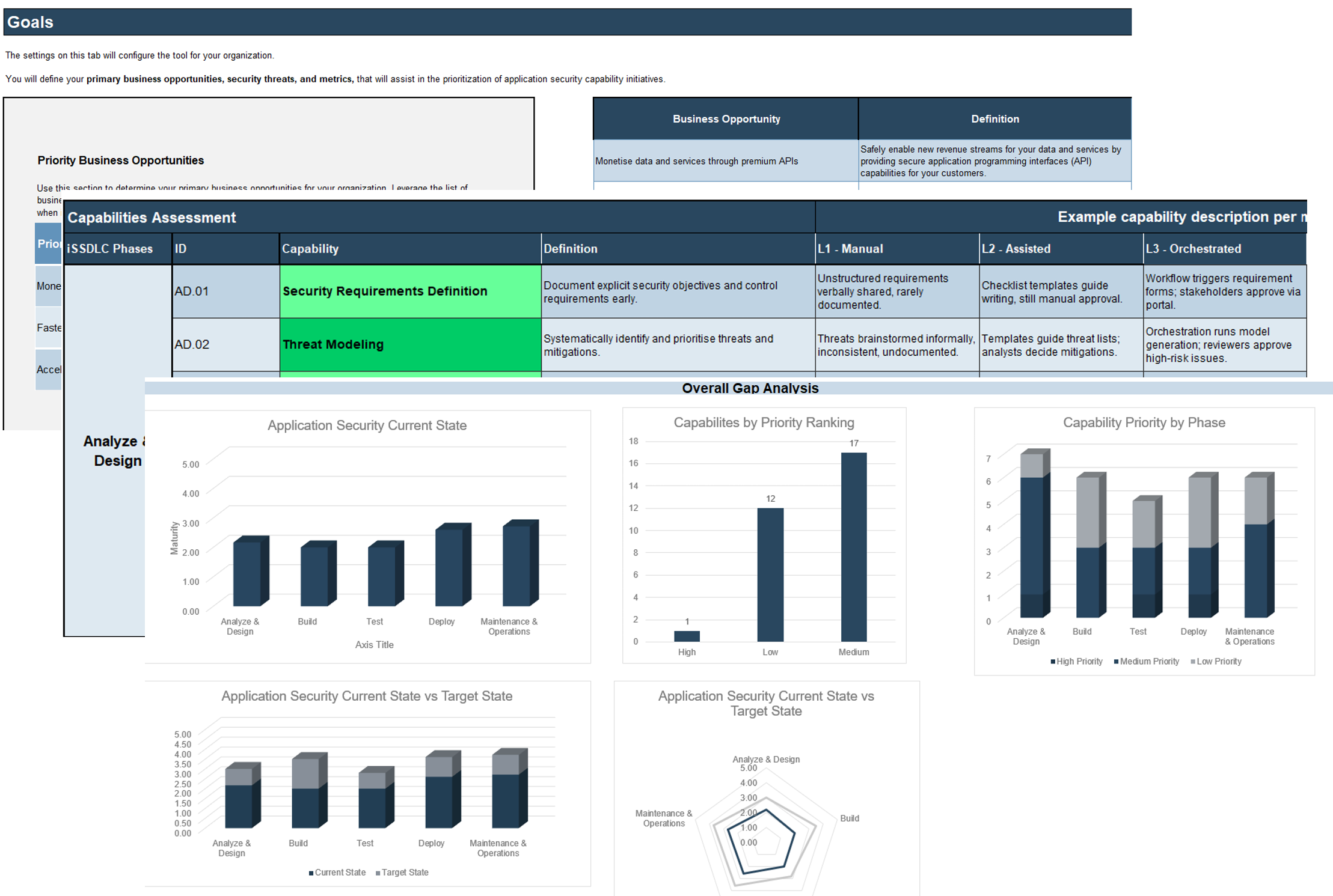
Blueprint benefits
IT Benefits
- Enhanced adoption of DevSecOps, which provides smoother integration of security into development workflows through a maturity-guided improvement plan.
- Improved visibility of an organization's security risks and gaps across the SDLC, which promotes proactive threat mitigation and enables targeted remediation efforts.
- Accelerated adoption of application security tools and strengthened organizational readiness for AI-driven development initiatives.
Business Benefits
- Reduced cost and downtime in application security incidents through the strengthening of foundational controls, which minimizes breach likelihood.
- Improved time to market of solutions through the embedding of scalable and automated security practices that are aligned to business-critical capabilities.
- Increased stakeholder confidence and regulatory readiness through the demonstration of a proactive and measurable approach to secure applications.
Info-Tech offers various levels of support to best suit your needs
DIY Toolkit | Guided Implementation | Workshop | Consulting |
| “Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful.” | “Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track.” | “We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place.” | “Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project.” |
Diagnostics and consistent frameworks are used throughout all four options. | |||
Guided Implementation
A Guided Implementation (GI) is a series of calls with an Info-Tech analyst to help implement our best practices in your organization.
A typical GI is 6 to 12 calls over the course of 4 to 6 months.
What does a typical GI on this topic look like?
Phase 1 | Phase 2 | Phase 3 |
| Call #1: Identify requirements and goals. Call #2: Review pain points and policies and establish metrics. | Call #3: Conduct capabilities assessment to determine current state. Call #4: Finalize capabilities assessment to determine target state. | Call #5: Develop and prioritize initiatives. Call #6: Finalize roadmap, develop metrics, and complete strategy deck. |
Workshop overview
Contact your account representative for more information.
workshops@infotech.com 1-888-670-8889
Day 1 | Day 2 | Day 3 | Day 4 | Day 5 | ||
Prioritize iSSDLC capabilities. | Assess application security maturity. | Develop initiatives. | Finalize strategy. | Complete next steps and wrap-up (offsite). | ||
Activities |
|
|
|
|
| |
Deliverables |
|
|
|
|
|
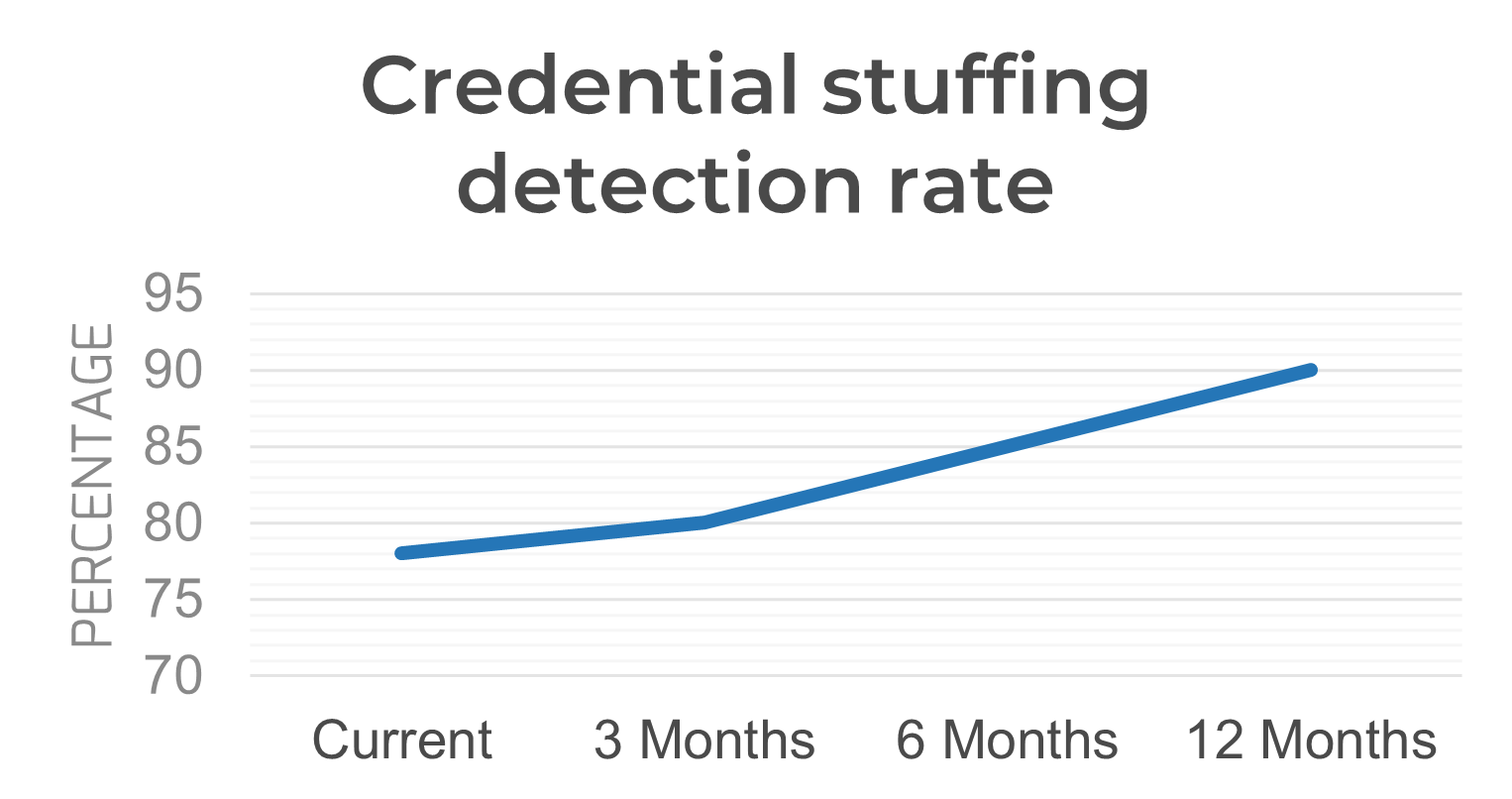
Measure the value of this blueprint
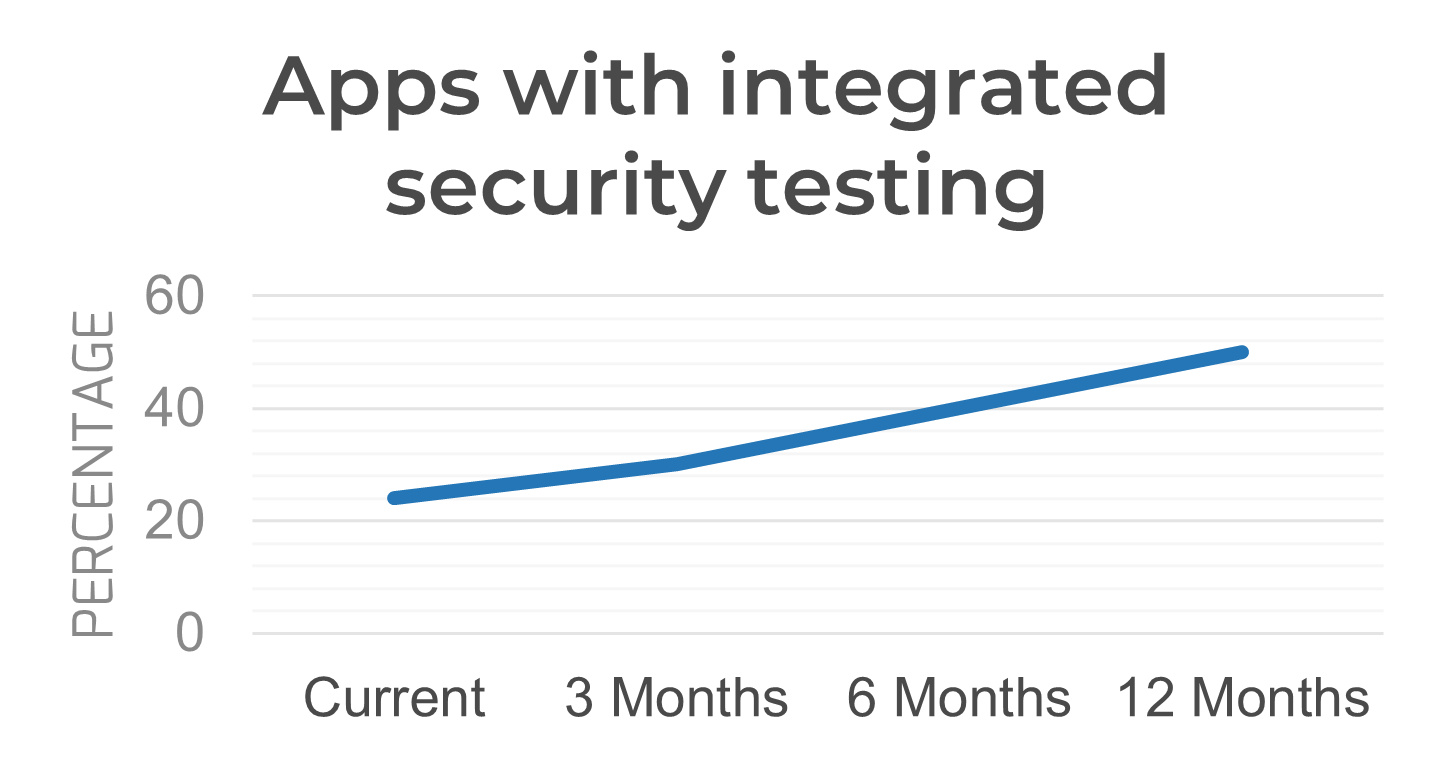
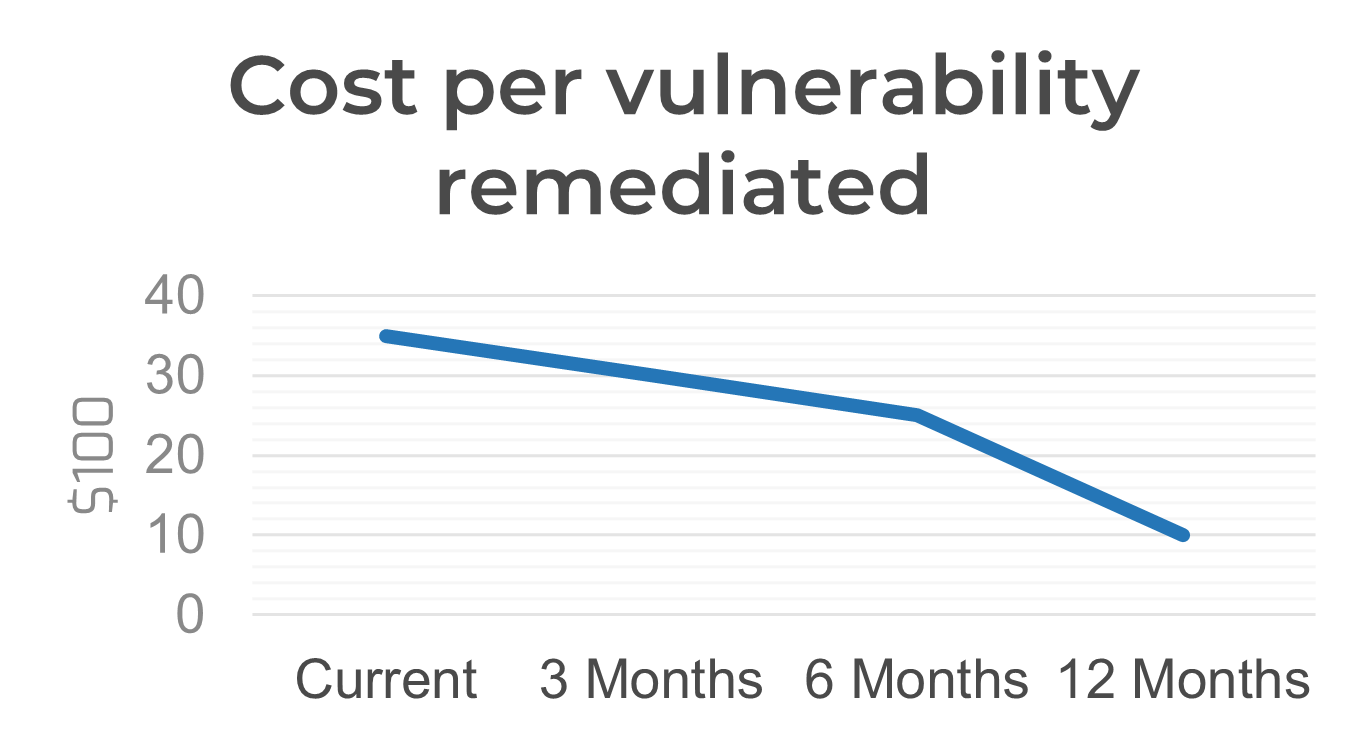
The value of this research can be measured by considering key application security metrics, as identified in step 1.3. These metrics should improve after implementation of the research, with examples shown to the right. Potential metrics can include:
Security metrics
- Mean time to remediate (MTTR) critical vulnerabilities
- Percentage of third-party components without known vulnerabilities
- Credential stuffing detection rate
- Security coverage in CI/CD pipeline
- Time to patch zero-day vulnerabilities
- Percentage of APIs with business logic testing
- Data exposure events from AI workloads
- Quantum resilience readiness
- Insider threat detections
Case study
INDUSTRY: Banking | SOURCE: “Case Study: How Escape enhanced Shine's application security”, Escape, 2024
Reducing risk, improving visibility, and empowering developers with a modernized secure coding practice.
Challenge
Shine, an online banking subsidiary of one of the leading financial services groups in Europe, Société Générale, faced challenges handling escalating application security threats. This included a lack of visibility in identifying all exposed APIs, limited ability in assessing the associated security risks of APIs, inefficient remediation process within the SDLC, and the challenge of meeting stringent security standards. This left Shine’s application security in a reactive state that lacked a unified, proactive security practice within the SDLC.
Solution
To address the various challenges, Shine implemented an AI-driven secure SDLC platform that will integrate into their development pipeline. A modern DAST solution was implemented, which included such innovative features as:
- Automated API discovery
- Continuous vulnerability scanning
- CI/CD integration
- Developer-friendly remediation
- GraphQL security support
These capabilities will become the pillar of modernizing Shine’s DevSecOps practice.
Results
Shine’s application security modernization efforts through advanced secure SDLC resulted in improvements to their security, risk mitigation, and development efficiency. Achieving full visibility into their API and attack surface controls helped prioritize initiatives to protect their assets. Continuous scanning and AI-driven analysis enable Shine’s security team to quickly assess and address emerging vulnerabilities and threats. Overall, Shine’s embrace of automation and collaboration transformed its application security while supporting innovation across the organization.
Develop a strategic plan for intelligent application security.
Phase 1
Prioritize iSSDLC Capabilities
Phase 1 | Phase 2 | Phase 3 |
1.1 Identify business and security requirements. 1.2 Identify goals. 1.3 Establish metrics. 1.4 Assign roles and responsibilities. | 2.1 Assess current application security state. 2.2 Determine target state. | 3.1 Develop and prioritize initiatives. 3.2 Develop roadmap. 3.3 Develop strategy deck. |
This phase will walk you through the following activities:
- 1.1 Identify business and security requirements.
- 1.2 Identify goals.
- 1.3 Establish metrics.
- 1.4 Assign roles and responsibilities.
Outcome:
- Defined security requirements
- Defined priority business opportunity and security threats
- Established metrics
- Established governance
This phase involves the following participants:
- Information security
- Application/delivery managers
- Business
1.1 Define requirements for application security
30 minutes
Input: Brainstorm stakeholders, Regulations, Customer contracts
Output: Identified requirements
Materials: Whiteboard, Capabilities Assessment Tool
Participants: Information security, Business, Privacy, Compliance
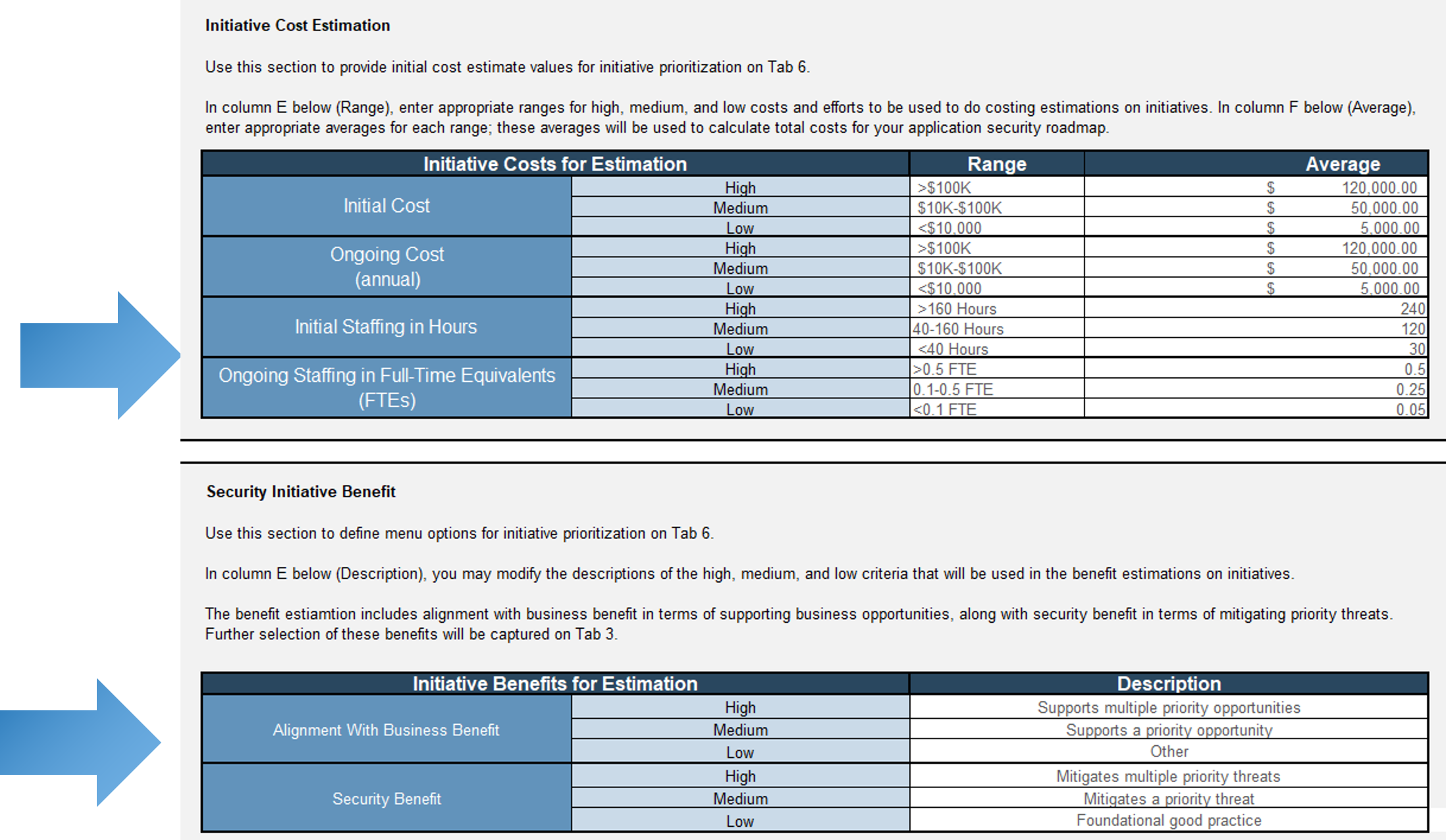
Gather the required participants and use the Capabilities Assessment Tool to configure the tool within the following categories:
- Initiative cost estimation: estimated ranges for initial and ongoing cost and staffing hours.
- Security initiative benefit: categorization of alignment to business and security benefits.
- FTE equivalent and roadmap start year: full-time equivalent hours defined by your organization, along with the estimated start year for your iSSDLC roadmap.
The following slides provide more information on this step.
Download the Capabilities Assessment Tool
Define requirements
- In Tab 2 of the iSSDLC Capabilities Assessment Tool, configure the tool for your organization by estimating the initial and ongoing cost, the staffing hours, the security benefits of the initiative, and the estimated year to commence the roadmap.
- In cells E9:E20, define the ranges for your initial and ongoing cost and staffing hours.
- In cells F26:F28, define your ranges for alignment with business benefit in terms of supporting business opportunities.
- In cells F29:F31, define the ranges for the security benefits of your roadmap in terms of mitigating priority threats.
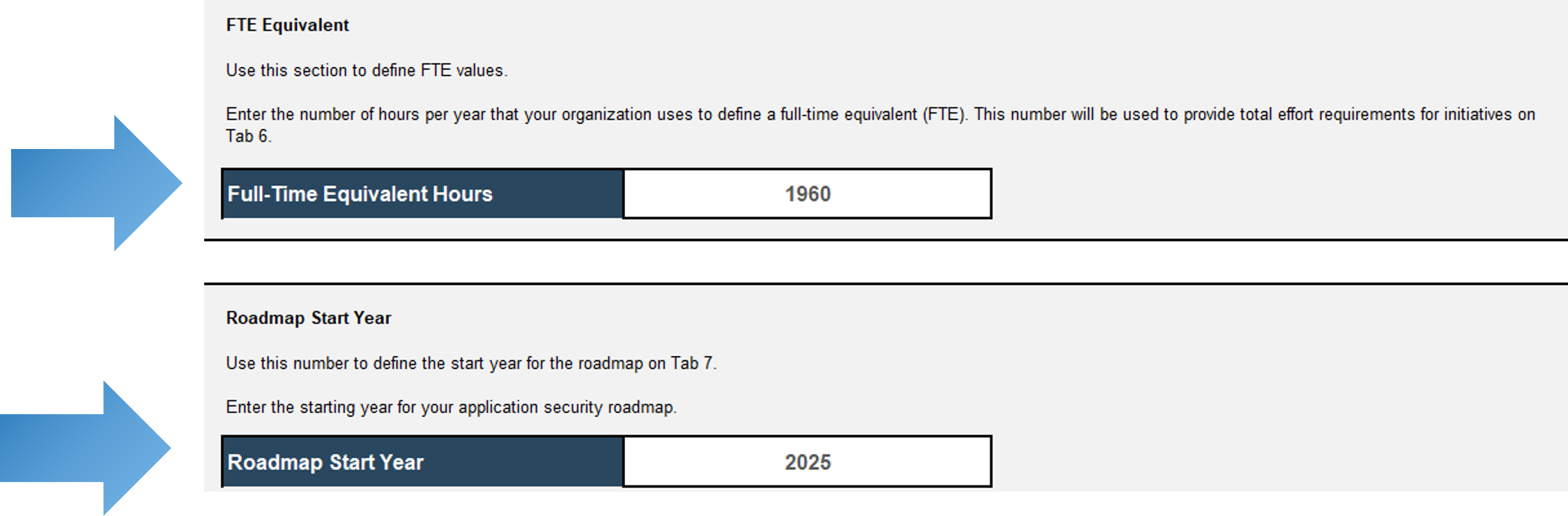
- In cell D36, enter the number of hours per year used to define a full-time equivalent (FTE).
- In cell D42, enter the starting year for your application security roadmap.
1.2 Define goals for the iSSDLC
60 minutes
Input: Brainstorm stakeholders, Regulations, Customer contracts
Output: Identified requirements
Materials: Whiteboard, iSSDLC Capabilities Assessment Tool
Participants: Information security, Business, Privacy, Compliance
Gather the required participants and leverage the iSSDLC Capabilities Assessment Tool to capture the following application security goals.
- Business opportunities: Develop strategic enterprise goals that can be supported by improvements to the organization’s application security program.
- Security threats: List highest priority security threats that can be mitigated through improvements to the organization’s application security program.
- Application security metrics: KPIs measure the effectiveness of initiatives and alignment with business opportunities and security threats.
The following slides provide more information on this step.
Download the iSSDLC Capabilities Assessment Tool
1.2.1 Identify business opportunities
- Improving an organization’s application security program should focus not only on the technical components but also on the business impact and its alignment to the enterprise goals.
- Identifying business opportunities that could be supported through an application security strategy will demonstrate strategic alignment and ROI to executives.
- Business opportunities help influence prioritization of security capabilities.
- Application security capabilities can support multiple business opportunities, which shows greater alignment with the business.
Info-Tech Insight
Business-aligned security enables speed without foregoing trust. By focusing on what drives business goals, organizations can innovate securely and confidently.

 Build a Cloud Security Strategy
Build a Cloud Security Strategy
 Identify the Components of Your Cloud Security Architecture
Identify the Components of Your Cloud Security Architecture
 Identify Opportunities to Mature the Security Architecture
Identify Opportunities to Mature the Security Architecture
 Embed Security Into the DevOps Pipeline
Embed Security Into the DevOps Pipeline
 Secure Your Hybrid Workforce
Secure Your Hybrid Workforce
 Ensure Cloud Security in IaaS, PaaS, and SaaS Environments
Ensure Cloud Security in IaaS, PaaS, and SaaS Environments
 Improve Email Security
Improve Email Security
 Secure Your Perimeterless Network
Secure Your Perimeterless Network
 Develop a Strategic Plan for Intelligent Application Security
Develop a Strategic Plan for Intelligent Application Security