- AI adoption, EHR systems, and connected digital health solutions have increased healthcare organizations' risk of data breaches.
- Cybersecurity threats and breaches are increasing in frequency and resulting in large financial losses.
- Frequent updates to Health Insurance Portability and Accountability Act (HIPAA) and other privacy laws require adaptability.
Our Advice
Critical Insight
- Healthcare organizations that do not increase investments for HIPAA compliance risk not only financial losses from fines but also reputational damage, which impacts revenue growth and future investment opportunities.
- Keeping up with evolving HIPAA regulations can be challenging. Developing an organizational cadence for compliance auditing, addressing risk factors, and partnering with a compliance solution will strengthen HIPAA compliance and reduce cybersecurity threats.
- Info-Tech’s “test once, attest many” approach and tools illustrate that if you comply with all NIST policy controls, you will be in compliance with HIPAA policy controls. Don’t duplicate efforts. Focus on optimizing and maturing.
Impact and Result
- Leverage Info-Tech’s insights on current healthcare cybersecurity threats and challenges impacting HIPAA compliance.
- Introduce Info-Tech’s framework to strengthen HIPAA compliance in your organization.
- Use Info-Tech’s top HIPAA policy templates to determine your policy gaps and develop new policies to improve compliance.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
10.0/10
Overall Impact
$5,893
Average $ Saved
44
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
Champaign Residential Services Inc
Guided Implementation
10/10
$1,360
1
Thank you for all of your help Sharon!
Randolph Brooks Federal Credit Union
Guided Implementation
10/10
$2,720
10
Great experience and advice from Sharon!
Randolph Brooks Federal Credit Union
Guided Implementation
10/10
$13,600
120
great experience overall with insights and tools to assist
Navigate the HIPAA Landscape
Understanding policies and best practices for privacy and security compliance in alignment with evolving regulations.
Analyst Perspective
Developing a culture attuned to HIPAA compliance in your organization will lower your cybersecurity risks.
In today's healthcare landscape, the convergence of AI adoption, EHR systems, and connected digital health solutions has revolutionized patient care. These advancements enable personalized medicine and efficient data management. However, this progress comes with a trade-off: an amplified risk of data breaches. Cybersecurity threats are increasing exponentially, impacting the financial stability of healthcare organizations.
As healthcare organizations increasingly embrace AI-driven tools for diagnostics and predictive analytics, they inadvertently expose themselves to new vulnerabilities. Ensuring secure handling of patient data becomes a critical concern. Balancing innovation with robust security protocols is essential. Navigating the complex and evolving HIPAA privacy and security policies remains nonnegotiable. The Office of Civil Rights is increasing penalties for HIPAA violations, significantly affecting healthcare organizations' financial health and reputation.
This research provides a roadmap to enhance HIPAA compliance through policy updates, frequent monitoring, audits, staff training, and regular risk assessments.

Sharon Auma-Ebanyat
Research Director, Healthcare
Industry Practice
Info-Tech Research Group
Executive Summary
| Your Challenge | Common Obstacles | Info-Tech's Approach |
|
Navigating an increasingly complex market. AI adoption, EHR systems, and connected digital health solutions have increased healthcare organization's risk of data breaches. Protecting your organization from cybersecurity threats and breaches, which are increasing in frequency and resulting in large financial losses. Keeping up with HIPAA compliance requirements: frequent updates to Health Insurance Portability and Accountability Act (HIPAA) and other privacy laws require adaptability. |
Limited budgets and competing priorities to deliver healthcare services and invest in robust cybersecurity resources and measures to prevent breaches and protect patient privacy. New and changing HIPAA regulation that can be a challenge to understand and align with existing policies and compliance. Educational awareness of scope and intersecting privacy laws are challenging for hospitals to navigate, leading to compliance gaps. |
Leverage Info-Tech's insights on current healthcare cybersecurity threats and challenges impacting HIPAA compliance. Introduce Info-Tech's framework to strengthen HIPAA compliance in your organization. Use Info-Tech's top HIPAA policy templates to determine your policy gaps and develop new policies to increase compliance. |
Info-Tech Insight
Keeping up with evolving HIPAA regulation can be challenging. However, developing an organizational cadence for compliance auditing, addressing risk factors, and partnering with a compliance solution will strengthen HIPAA compliance and reduce cybersecurity threats.
Global regulatory frameworks protect their citizens
United States
- Health Insurance Portability and Accountability Act: A US federal law that safeguards individuals' health information privacy and sets standards for the secure handling of medical data by healthcare providers and insurers.
- NIST SP 800-53: The National Institute of Standards and Technology (NIST) provides guidelines for securing federal information systems, including healthcare organizations.
Canada
- PIPEDA (Personal Information Protection and Electronic Documents Act): Although not specific to healthcare, PIPEDA applies to healthcare organizations nationwide. It outlines principles for protecting personal information, including health data.
- Some provinces have their own privacy laws similar to PIPEDA: These include Ontario, New Brunswick, Newfoundland and Labrador, Nova Scotia.
European Union
- GDPR (General Data Protection Regulation): GDPR applies to all EU member states and regulates the processing of personal data, including health data. It emphasizes consent, data minimization, and breach reporting.
- NIS Directive (Network and Information Systems Directive): NIS focuses on critical infrastructure, including healthcare systems. It requires organizations to implement security measures and report incidents.
United Kingdom (UK)
- Data Protection Act 2018: This UK law incorporates GDPR principles and provides additional guidance on data protection, including healthcare data.
- CQC (Care Quality Commission) Regulations: CQC oversees healthcare services and assesses their cybersecurity practices.
Australia
- The Privacy Act 1988: This Australian law governs the handling of personal information, including health information. Specifically for healthcare, it requires collection and use, consent, security and storage, access and correction, disclosure, anonymity, and complaints.
HIPAA provides protections that have evolved over time
What is the Health Insurance Portability and Accountability Act (HIPAA)?
HIPAA is an act that ensures critical protections such as security of protected health information (PHI), notification of breaches, and adherence to privacy rules.
HIPPA was enacted in 1996 and enables workers to carry forward healthcare insurance between jobs, prohibits discrimination against beneficiaries with preexisting health conditions, and guarantees coverage renewability in multi-employer health insurance plans. Over time, HIPAA addressed healthcare fraud, streamlined claims processing, and established national standards for safeguarding sensitive patient health information from unauthorized disclosure.
HIPAA provides broad coverage
Individuals, organizations, or agencies that transmits protected health information (PHI) electronically. The three main categories of covered entities are:
- Healthcare providers
- Health plans
- Healthcare clearinghouses
If a covered entity performs business with a business associate (for example, a vendor), a contract must be established with stipulations to protect privacy and security of protected health information.
HIPAA is strictly enforced
HIPAA as a federal law is enforced by the Health and Human Services (HHS) Office for Civil Rights (OCR). While the OCR has no uniform standard of enforcement, individual states have the authority to establish their own laws and regulations that offer additional protections for personal health information beyond what HIPAA provides. OCR fines can range from $100 to $1.5 million per calendar year.
The evolution of HIPAA Regulation
| August 1996 | HIPAA signed into law by President Bill Clinton. |
| April 2003 | Effective date of the HIPAA Privacy Rule. |
| April 2005 | Effective date of the HIPAA Security Rule. |
| March 2006 | Effective date of the HIPAA Enforcement Rule. |
| September 2009 | Effective date of HITECH and the Breach Notification Rule. |
| March 2013 | Effective date of the Final Omnibus Rule*. |
*All annual changes to HIPAA regulation since 2013 are done through the Omnibus Rule.
Integrated (OHCA) or affiliated healthcare organizations can function as a single covered entity
Organized Health Care Arrangement (OHCA)
OHCAs are particularly valuable when healthcare settings are clinically integrated but there is no common ownership or control among participating entities. In an OHCA, healthcare providers who typically treat a common set of patients can designate themselves as part of this arrangement.
- Shared Privacy Practices: OHCAs allow entities to share a joint notice of privacy practices.
- Collaboration: Entities can collaborate on using and disclosing protected health information (PHI) for treatment, payment, and healthcare operations.
- Efficiency: OHCAs provide economies of scale in compliance efforts and enhance patient care coordination.
Affiliated Covered Entity (ACE)
ACE designation permits legally distinct entities to function as a single covered entity under HIPAA regulations. ACEs are employed when healthcare entities share common ownership or control. For instance, a healthcare system with multiple affiliated clinics can designate itself as an ACE.
- Unified Compliance: ACEs can develop and distribute a single notice of privacy practices.
- Unified Policies: They adhere to a unified set of policies and procedures.
- Single Privacy Official: ACEs appoint a single privacy official.
- Shared Training Programs: ACEs can implement shared training programs.
Hybrid covered entities require specific protocols
What is a hybrid entity?
A designation that allows a covered entity to separate its different functions and designates specific components as healthcare components, which are subject to HIPAA's Privacy Rule. Examples of hybrid entities include:
- Universities with medical centers.
- Integrated health systems.
- Healthcare research institutions.
Hybrid entities must follow strict requirements:
Must remain compliant with all privacy rules:
- Organizations must protect PHI from unauthorized access, use, or disclosure.
- PHI should remain confidential, and access should be restricted to authorized personnel.
- PHI can only be shared as permitted by law or with patient consent.
- Patients have rights over their health information, including access, amendment, and accounting of disclosures.
Must comply with security standards and rules:
- Implement administrative, physical, and technical measures to secure electronic PHI.
- Regularly assess vulnerabilities and address risks to ePHI.
- Policies, procedures, and training to protect ePHI.
- Secure facilities, access controls, and device security.
- Encryption, access controls, and audit logs.
Must follow all HIPAA documentation and policies:
- Hybrid entities (organizations with both covered and non-covered functions) must document their compliance efforts.
- Privacy policies should outline how PHI is handled and protected.
Requirements for training hybrid entity employees
| Customized Training Programs | Develop and offer specialized training programs that cater to the unique educational needs of each workforce segment. |
| Role-Based Access Controls | Implement access controls based on roles to restrict sensitive health information access. |
| Continuous Education and Communication | Conduct regular educational sessions and maintain open communication to address compliance requirements. |
| Segregation of Systems and Information | Physically or digitally separate systems handling sensitive health information from nonsensitive ones. |
| Appoint Compliance Officers | Designate compliance officers or teams responsible for monitoring, enforcing, and guiding compliance efforts within each segment of the hybrid entity. |
| Sustained Oversight | Establish consistent oversight and reporting mechanisms to uphold compliance standards across the organization. |
HIPAA Title II addresses the most serious risks

Sections of HIPAA Regulation
The HIPAA Act is structured into five distinct parts (or titles).
Title II, which encompasses security, breach, and privacy rules, addresses the highest cybersecurity risks.
- Title I: Ensures health insurance coverage for workers and their families even when they change jobs or experience job loss. It also restricts new health plans from denying coverage based on preexisting conditions.
- Title II: Addresses healthcare fraud and abuse, introduces medical liability reform, and emphasizes administrative simplification. This includes establishing national standards for electronic healthcare transactions, security, breach, and privacy rules and creating identifiers for providers, employers, and health insurance plans.
- Title III: Provides guidelines for pretax medical spending accounts. It introduces changes to health insurance law and deductions related to medical insurance.
- Title IV: Offers guidelines for group health plans, including modifications to health coverage provisions.
- Title V: Governs company-owned life insurance policies. It also addresses the treatment of individuals without United States citizenship and repeals the financial institution rule related to interest allocation.
Title II addresses privacy, security, and breaches
1 Privacy Rule
(45 CFR § 164.530)
The Privacy Rule sets forth standards to safeguard an individual's medical records and other protected health information (PHI):
- It addresses the use and disclosure of PHI and outlines individuals' rights to comprehend, access, and control how their medical data is utilized.
- The Privacy Rule aims to strike a balance with PHI protection and access, ensuring proper protection of an individual's health information while allowing access to necessary data for high-quality healthcare and public safety.
2 Security Rule
(45 CFR § 164.308)
The Security Rule covers a subset of information protected by the Privacy Rule:
- The Security Rule focuses on data created, received, maintained, or transmitted in electronic form. It complements the Privacy Rule, encompassing all individually identifiable health information.
- The Security Rule dictates best practices safeguarding all forms of PHI within your organization. The Security Rule doesn't explicitly apply to PHI transmitted orally or in writing.
3 Breach Notification Rule
(45 CFR § 164.404)
The Breach Notification Rule requires organizations to inform affected individuals of any breach of their PHI. This outlines procedures for addressing unauthorized use or disclosure of protected health information:
- If a breach of unsecured PHI impacts 500 or more individuals, a covered entity must notify the Secretary of Health and Human Services (HHS) within 60 calendar days from the discovery of the breach.
- For breaches affecting fewer than 500 individuals, the covered entity must report to the secretary within 60 days of the end of the calendar year in which the breach was discovered but may report earlier.
Note: Not legal advice.
Breaches are leading to significant financial loss
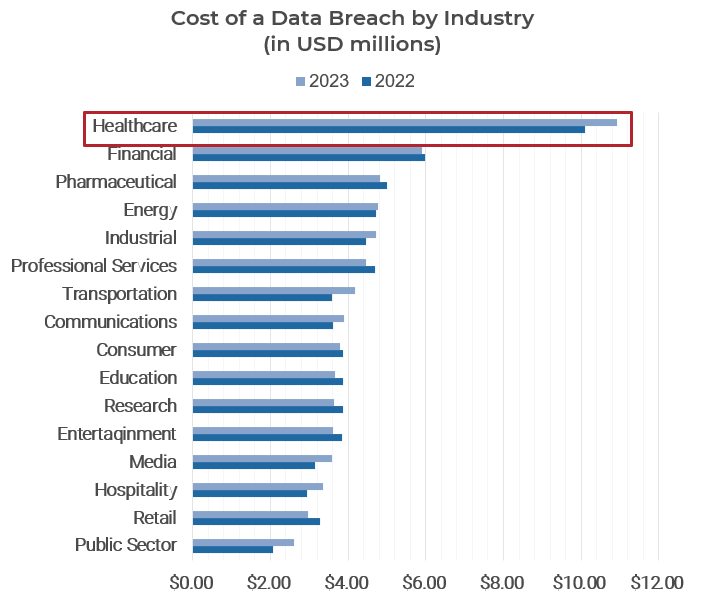
Source: IBM, 2023.

* A data breach lifecycle refers to the time frame between when a breach is detected and when it is contained and resolved.
Info-Tech Insight
In addition to the penalties and costs of data breaches, there are hidden noncompliance costs such an increased insurance premiums, loss of business opportunities, and reputation management, which have long-term implications.
Key challenges are impacting HIPAA compliance
- Staffing Limitations: Most hospitals have low staffing levels for their HIPAA privacy office.
- Lack of a Risk Assessment Process: Identifying risks through a risk analysis is essential, but equally important is taking prompt action to address those risks. Healthcare organizations are challenged with prioritizing and remediating security vulnerabilities related to electronic protected health information.
- Growing Health Data: The exponential growth of health data, including electronic health records, adds complexity. Hospitals must safeguard this sensitive information while complying with HIPAA.
- Sophisticated Threats: Cybersecurity threats are becoming more advanced. Hospitals need robust security measures to protect patient data from breaches and unauthorized access.
- Failure to Audit and Regularly Verify HIPAA Compliance: Keeping staff informed about HIPAA requirements and best practices is challenging. Regular training sessions are necessary to ensure that employees understand their responsibilities and follow compliance guidelines.
- Employee Training and Awareness: Lack of awareness about HIPAA's scope, obligations, and enforcement can lead to gaps in compliance. Hospitals must educate staff and stay informed.
- Changing HIPAA Regulation and Intersecting Privacy Laws: HIPAA regulations evolve over time. Keeping up with these changes and ensuring compliance can be demanding for hospitals. HIPAA also intersects with other privacy laws. Navigating these intersections requires hospitals to carefully manage compliance efforts.
Staffing, audits, training, and assessments are risks

Staffing and budgets are the biggest challenges

Compliance costs are high, but penalties are higher
| Compliance category | Small organizations and business associates | Medium to large organizations |
| Risk analysis and risk management plan | $2K | $20K |
| Gap analysis and remediation | $1K-$10k | $10K (depends on security program in place) |
| Staff training | $30-$50 per user | $5K+ |
| Policy development | $1-2K | $5K |
| HIPAA compliance readiness assessment | Varies | $15K |
| Onsite HIPAA compliance audit | Varies | $40K+ |
| Total | ~$12K+ | $85K+ |
Noncompliance costs between $100 to $50,000 per violation or per record and can increase to $1.5 million with criminal charges.
The four main penalty tiers of fines include:
Tier 1: Unaware of HIPAA violation � A penalty of $100 to $50,000 and a maximum of $25,000 per calendar year.
Tier 2: Reasonable cause for awareness of HIPAA violation � A penalty of $1,000 to $50,000 per incident; up to $100,000 per calendar year.
Tier 3: Willful neglect with correction within 30 days of discovery � A penalty of $10,000 to $250,000 per calendar year.
Tier 4: Willful neglect with no effort to correct violation in 30 days of discovery � A penalty of $50,000 to $1.5 million per calendar year.
Info-Tech Insight
Healthcare organizations that do not increase investments for HIPAA compliance not only risk financial losses from fines but also reputation damage, which impacts revenue growth and future investment opportunities.
HIPAA regulations continue to evolve
PRIVACY RULE CHANGES in 2023
| HIPAA Requirement | Description | Implications |
| Shortened Response Time | When you request your protected health information (PHI), healthcare providers response time will be shortened from 30 days to 15 days. | Healthcare organizations will need to develop mechanisms and solutions to process patient records in 15 days and update their medical record retrieval process. |
| EHR Sharing | You can ask providers to share your electronic health records (EHR) with other healthcare professionals and insurers. | Healthcare providers will be allowed to disclose PHI to other third parties based on individual care or case management. |
| Notice of Privacy Practices | The requirement for written confirmation of a notice of privacy practices will be removed. | Covered entities will need to update their notices to include process of accessing data, filing a HIPAA complaint, and obtaining a copy of the notice. |
| COVID-19 Flexibilities | The temporary HIPAA enforcement flexibilities due to the pandemic will end. | Healthcare organizations must evaluate and transition to HIPAA-compliant telehealth solutions. |
| Substance Use Disorder (SUD) Records | Patients have more control over how their SUD records are used and disclosed. | Providers will have to get consent to have patient records shared with other providers. |
HIPAA regulations changed again in 2024
PRIVACY RULE CHANGES in 2024
| HIPAA Requirement | Description | Implications |
| Part 2 Alignment | Efforts will continue to align the Confidentiality of Substance Use Disorder Patient Records (Part 2) regulations more closely with HIPAA. This ensures equal protections for all healthcare data, including SUD records, while maintaining patient safety and informed treatment decisions. | Healthcare providers will need to get patient consent to obtain substance abuse records from participating providers. Failure to comply is a criminal offense. |
SECURITY RULE CHANGES in 2024
| HIPAA Requirement | Description | Implications |
| Cybersecurity Standards | New proposed Security Rule standards will be announced to enhance data protection and safeguard electronic health information. | The cybersecurity framework will help healthcare organization adopt best practices and there will be penalties for noncompliance. |
| Increased Penalties | The United States Department of Health and Human Services (HHS) will seek new laws to increase civil money penalties for HIPAA violations and improve enforcement. | Disbarment from Medicare and Medicaid programs, increase in HIPAA violation fines, and in some cases civil or criminal enforcement. |
Review HHS HIPAA Part 2 fact sheet
Review Federal Register on Substance Use Disorder Patient Record Regulation
Adopting best practices lowers risk, overcomes challenges, and improves compliance with Title II
| Categories | Descriptions |
| Privacy Policies |
|
| Security Policies |
|
| Breach Notification Policies: |
|
| Business Associate Agreements: |
|
| Training and Awareness: |
|
| Incident Response Policies: |
|
| Data Retention and Destruction: |
|
| Access Control Policies: |
|
| Risk Assessment and Management: |
|
| Mobile Device Policies: |
|
Info-Tech's "test once, attest many" approach to HIPAA (and other compliance obligations)

Download Build a Security Compliance Program
1.1 Map compliance requirements to control framework
- Compliance obligations which have an approved conformance level of 2 or greater need to be mapped into your security control framework using the steps illustrated on the following slides.
- Compliance obligations with an approved conformance level of 1 ("no effort") may be mapped into the control framework if desired.
- Info-Tech provides several pre-mapped compliance obligations. Start by reviewing the pre-mapped compliance obligations on tab 8 of the Security Compliance Management Tool. Then go to tab 3 and on line 3 click the drop-down in the cell for compliance obligations and select HIPAA and then attest your conformance level.
- Complete tabs 4, 5, and 6 with your security team to determine your level of compliance.
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Info-Tech Insight
NIST policy controls are comprehensive and overlap with HIPAA policy controls. The subsequent steps will help you optimize and mature your overall security and privacy approach to address the gaps in your HIPPA policies to meet compliance.
Download the Security Compliance Management Tool
1.1.1 Add new compliance obligations if required
- The table at the top of tab 8, "Control DB," contains a list of all compliance obligations known to the tool. For each of the compliance obligations that you need to manage, refer to the table to see if they already exist.
- If you need to add a new compliance obligation, add in the name (and version number if known) along with a short identifier to the table.
Info-Tech will periodically update the Security Compliance Management Tool with new or revised mappings. Check our website for the latest version before mapping any new obligations. Current mappings include:
- HIPAA
- NIST Cybersecurity Framework
- NIST SP 800-171
- NIST SP 800-53
- Cybersecurity Maturity Model Certification (CMMC)
- SOC 2 Security
- ISO 27001/27002
- CIS Top 20 Critical Controls
- PCI Data Security Standard
1.1.2 Map new compliance obligations if required
- Once you have added the compliance obligation name and ID to the table, you will need to add a mapping into the database. Start by adding the new ID to the header row of a new column in the database table.
- In the obligations tab, go to the compliance obligation number 4 and open the drop-down and select HIPAA; this will generate all the applicable HIPAA policies in the control framework tab.
- Read the language of each of the Info-Tech controls in the control column and determine if there is a matching requirement in your compliance obligation. For each matching requirement, add a reference identifier and the source text for the requirement in the corresponding row of your new column.
- Most requirements from any cybersecurity or data protection obligation should be able to be mapped to one or more Info-Tech controls. However, you may occasionally find a requirement that does not easily map to one of the Info-Tech controls. In this situation, you can add a new control to the bottom of the framework database under the "Additional Controls" section.
Info-Tech Insight
Info-Tech's "test once, attest many" approach and tools illustrate that if you comply with all NIST policy controls, you will be in compliance with HIPAA policy controls. NIST policy controls are comprehensive and overlap with HIPAA policy controls from a quality and efficiency perspective. Don't duplicate efforts. Focus on optimizing and maturing.
