- New technology can hit like a meteor. Not only disruptive to IT, technology provides opportunities for organization-wide advantage.
- Your role is endangered. If you don’t prepare for the most disruptive technologies, you could be overshadowed. Don’t let the Chief Marketing Officer (CMO) set the technological innovation agenda
- Predicting the future isn’t easy. Most IT leaders fail to realize how quickly technology increases in capability. Even for the tech savvy, predicting which specific technologies will become disruptive is difficult.
- Communication is difficult when the sky is falling. Even forward-looking IT leaders struggle with convincing others to devote time and resources to monitoring technologies with a formal process.
Our Advice
Critical Insight
- Establish the core working group, select a leader, and select a group of visionaries to help brainstorm emerging technologies.
- Brainstorm about creating a better future, begin brainstorming an initial longlist.
- Train the group to think like futurists.
- Evaluate the shortlist.
- Define your PoC list and schedule.
- Finalize, present the plan to stakeholders and repeat.
Impact and Result
- Create a disruptive technology working group.
- Produce a longlist of disruptive technologies.
- Evaluate the longlist to produce a shortlist of disruptive technologies.
- Develop a plan for a proof-of-concept project for each shortlisted technology.
Analyst Perspective
The key is in anticipation.
“We all encounter unexpected changes and our responses are often determined by how we perceive and understand those changes. We react according to the unexpected occurrence. Business organizations are no different.
When a company faces a major technology disruption in its markets – one that could fundamentally change the business or impact its processes and technology – the way its management perceive and understand the disruption influences how they describe and plan for it. In other words, the way management sets the context of a disruption – the way they frame it – shapes the strategy they adopt. Technology leaders can vastly influence business strategy by adopting a proactive approach to understanding disruptive and innovative technologies by simply adopting a process to review and evaluate technology impacts to the company’s lines of business.”

Troy Cheeseman
Practice Lead, Infrastructure & Operations Research
Info-Tech Research Group
Executive Summary
Your Challenge
- New technology can hit like a meteor. Not only disruptive to IT, technology provides opportunities for organization-wide advantage.
- Your role is endangered. If you don’t prepare for the most disruptive technologies, you could be overshadowed. Don’t let the chief marketing officer (CMO) set the technological innovation agenda.
Common Obstacles
- Predicting the future isn’t easy. Most IT leaders fail to realize how quickly technology increases in capability. Even for the tech savvy, predicting which specific technologies will become disruptive is difficult.
- Communication is difficult when the sky is falling. Even forward-looking IT leaders struggle with convincing others to devote time and resources to monitoring technologies with a formal process.
Info-Tech’s Approach
- Identify, resolve, and evaluate. Use an annual process as described in this blueprint: a formal evaluation of new technology that turns analysis into action.
- Lead the analysis from IT. Establish a team to carry out the annual process as a cure for the causes of “airline magazine syndrome” and to prevent it from happening in the future.
- Train your team on the patterns of progress, track technology over time in a central database, and read Info-Tech’s analysis of upcoming technology.
- Create your KPIs. Establish your success indicators to create measurable value when presenting to your executive.
- Produce a comprehensive proof-of-concept plan that will allow your company to minimize risk and maximize reward when engaging with new technology.
Info-Tech Insight
Proactively monitoring, evaluating, and exploiting disruptive tech isn’t optional.
This will protect your role, IT’s role, and the future of the organization.
A diverse working group maximizes the insight brought to bear.
An IT background is not a prerequisite.
The best technology is only the best when it brings immediate value.
Good technology might not be ready; ready technology might not be good.
Review
We help IT leaders make the most of disruptive impacts.
This research is designed for:
Target Audience: CIO, CTO, Head of Infrastructure
This research will help you:
- Develop a process for anticipating, analyzing, and exploiting disruptive technology.
- Communicate the business case for investing in disruptive technology.
- Categorize emerging technologies to decide what to do with them.
- Develop a plan for taking action to exploit the technology that will most affect your organization.
Problem statement:
As a CIO, there is a need to move beyond day-to-day technology management with an ever-increasing need to forecast technology impacts. Not just from a technical perspective but to map out the technical understandings aligned to potential business impacts and improvements. Technology transformation and innovation is moving more quickly than ever before and as an innovation champion, the CIO or CTO should have foresight in specific technologies with the understanding of how the company could be disrupted in the near future. Foresight + Current Technology + Business Understanding = Understanding the Business Disruption. This should be a repeatable process, not an exception or reactionary response.
Insight Summary
Establish the core working group, select a leader, and select a group of visionaries to help brainstorm emerging technologies.
The right team matters. A core working group will keep focus through the process and a leader will keep everyone accountable. Visionaries are out-of-the-box thinkers and once they understand how to think like a "futurists," they will drive the longlist and shortlist actions.
Train the group to think like futurists
To keep up with exponential technology growth you need to take a multi-threaded approach.
Brainstorm about creating a better future; begin brainstorming an initial longlist
Establish the longlist. The longlist helps create a holistic view of most technologies that could impact the business. Assigning values and quadrant scoring will shortlist the options and focus your PoC option.
Converge everyone’s longlists
Long to short...that's the short of it. Using SWOT, value readiness, and quadrant mapping review sessions will focus the longlist, creating a shortlist of potential POC candidates to review and consider.
Evaluate the shortlist
There is no such thing as a risk-free endeavor. Use a systematic process to ensure that the risks your organization takes have the potential to produce significant rewards.
Define your PoC list and schedule
Don’t be afraid to fail! Inevitably, some proof-of-concept projects will not benefit the organization. The projects that are successful will more than cover the costs of the failed projects. Roll out small scale and minimize losses.
Finalize, present the plan to stakeholders, and repeat!
Don't forget the C-suite. Effectively communicate and present the working group’s finding with a well-defined and succinct presentation. Start the process again!

- Identify
- Establish the core working group and select a leader; select a group of visionaries
- Train the group to think like futurists
- Hold your initial meeting
- Resolve
- Create and winnow a longlist
- Assess and create the shortlist
- Evaluate
- Create process maps
- Develop proof of concept charter
The Key Is in Anticipation!
Use Info-Tech’s approach for analyzing disruptive technology in your own disruptive tech working group
| Phase 1: Identify | Phase 2: Resolve | Phase 3: Evaluate | |
|
Phase Steps |
|
|
|
|
Phase Outcomes |
|
|
|
Four key challenges make it essential for you to become a champion for exploiting disruptive technology
- New technology can hit like a meteor. It doesn’t only disrupt IT; technology provides opportunities for organization-wide advantage.
- Your role is endangered. If you don’t prepare for the most disruptive technologies, you could be overshadowed. Don’t let the CMO rule technological innovation.
- Predicting the future isn’t easy. Most IT leaders fail to realize how quickly technology increases in capability. Even for the tech savvy, predicting which specific technologies will become disruptive is difficult.
- Communication is difficult when the sky is falling. Even forward-looking IT leaders struggle with convincing others to devote time and resources to monitoring emerging technologies with a formal process.
“Look, you have never had this amount of opportunity for innovation. Don’t forget to capitalize on it. If you do not capitalize on it, you will go the way of the dinosaur.”
– Dave Evans, Co-Founder and CTO, Stringify
Technology can hit like a meteor
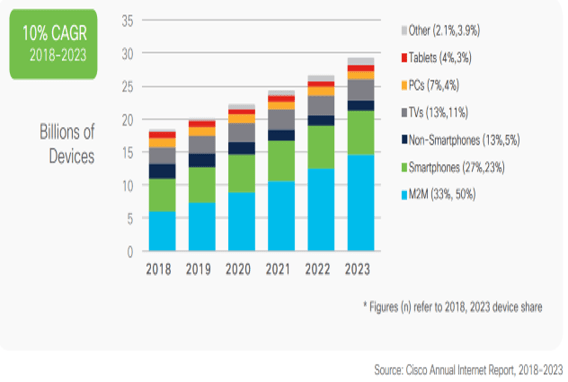
“ By 2025:
- 38.6 billion smart devices will be collecting, analyzing, and sharing data.
- The web hosting services market is to reach $77.8 billion in 2025.
- 70% of all tech spending is expected to go for cloud solutions.
- There are 1.35 million tech startups.
- Global AI market is expected to reach $89.8 billion.”
– Nick Gabov
IT Disruption
Technology disrupts IT by:
- Affecting the infrastructure and applications that IT needs to use internally.
- Affecting the technology of end users that IT needs to support and deploy, especially for technologies with a consumer focus.
- Allowing IT to run more efficiently and to increase the efficiency of other business units.
- Example: The rise of the smartphone required many organizations to rethink endpoint devices.
Business Disruption
Technology disrupts the business by:
- Affecting the viability of the business.
- Affecting the business’ standing in relation to competitors that better deal with disruptive technology.
- Affecting efficiency and business strategy. IT should have a role in technology-related business decisions.
- Example: BlackBerry failed to anticipate the rise of the apps ecosystem. The company struggled as it was unable to react with competitive products.
Senior IT leaders are expected to predict disruptions to IT and the business, while tending to today’s needs
You are expected to be both a firefighter and a forecaster
- Anticipating upcoming disruptions is part of your job, and you will be blamed if you fail to anticipate future business disruptions because you are focusing on the present.
- However, keeping IT running smoothly is also part of your job, and you will be blamed if today’s IT environment breaks down because you are focusing on the future.
You’re caught between the present and the future
- You don’t have a process that anticipates future disruptions but runs alongside and integrates with operations in the present.
- You can’t do it alone. Tending to both the present and the future will require a team that can help you keep the process running.
Info-Tech Insight
Be prepared when disruptions start coming down, even though it isn’t easy. Use this research to reduce the effort to a simple process that can be performed alongside everyday firefighting.
Make disruptive tech analysis and exploitation part of your innovation agenda

Organizations without high satisfaction with IT innovation leadership are only 20% likely to be highly satisfied with IT
“You rarely see a real-world correlation of .86!”
– Mike Battista, Staff Scientist, Cambridge Brain Sciences, PhD in Measurement
There is a clear relationship between satisfaction with IT and the IT department’s innovation leadership.
Prevent “airline magazine syndrome” by proactively analyzing disruptive technologies
“The last thing the CIO needs is an executive saying ‘I don’t what it is or what it does…but I want two of them!”
– Tim Lalonde
Airline magazine syndrome happens to IT leaders caught between the business and IT. It usually occurs in this manner:
- While on a flight, a senior executive reads about an emerging technology that has exciting implications for the business in an airline magazine.
- The executive returns and approaches IT, demanding that action be taken to address the disruptive technology – and that it should have been (ideally) completed already.
Without a Disruptive Technology Exploitation Plan:
“I don’t know”
With a Disruptive Technology Exploitation Plan:
“Here in IT, we have already considered that technology and decided it was overhyped. Let me show you our analysis and invite you to join our working group.”
OR
“We have already considered that technology and have started testing it. Let me show you our testing lab and invite you to join our working group.”
Info-Tech Insight
Airline magazine syndrome is a symptom of a wider problem: poor CEO-CIO alignment. Solve this problem with improved communication and documentation. Info-Tech’s disruptive tech iterative process will make airline magazine syndrome a thing of the past!
IT leaders who do not keep up with disruptive technology will find their roles diminished
“Today’s CIO dominion is in a decaying orbit with CIOs in existential threat mode.”
– Ken Magee
Protect your role within IT
- IT is threatened by disruptive technology:
- Trends like cloud services, increased automation, and consumerization reduce the need for IT to be involved in every aspect of deploying and using technology.
- In the long term, machines will replace even intellectually demanding IT jobs, such as infrastructure admin and high-level planning.
- Protect your role in IT by:
- Anticipating new technology that will disrupt the IT department and your place within it.
- Defining new IT roles and responsibilities that accurately reflect the reality of technology today.
- Having a process for the above that does not diminish your ability to keep up with everyday operations that remain a priority today.
Protect your role against other departments
- Your role in the business is threatened by disruptive technology:
- The trends that make IT less involved with technology allow other executives – such as the CMO – to make IT investments.
- As the CMO gains the power and data necessary to embrace new trends, the CIO and IT managers have less pull.
- Protect your role in the business by:
- Being the individual to consult about new technology. It isn’t just a power play; IT leaders should be the ones who know technology thoroughly.
- Becoming an indispensable part of the entire business’ innovation strategy through proposing and executing a process for exploiting disruptive technology.
IT leaders who do keep up have an opportunity to solidify their roles as experts and aggregators
“The IT department plays a critical role in [innovation]. What they can do is identify a technology that potentially might introduce improvements to the organization, whether it be through efficiency, or through additional services to constituents.”
– Michael Maguire, Management Consultant
The contemporary CIO is a conductor, ensuring that IT works in harmony with the rest of the business.
The new CIO is a conductor, not a musician. The CIO is taking on the role of a business engineer, working with other executives to enable business innovation.
The new CIO is an expert and an aggregator. Conductor CIOs increasingly need to keep up on the latest technologies. They will rely on experts in each area and provide strategic synthesis to decide if, and how, developments are relevant in order to tune their IT infrastructure.
The pace of technological advances makes progress difficult to predict
“An analysis of the history of technology shows that technological change is exponential, contrary to the common-sense ‘intuitive linear’ view. So we won’t experience 100 years of progress in the 21st century – it will be more like 20,000 years of progress (at today’s rate).”
– Ray Kurzweil
Technology advances exponentially. Rather than improving by the same amount of capability each year, it multiplies in capability each year.
Think like a futurist to anticipate technology before it goes mainstream.
Exponential growth happens much faster than linear growth, especially when it hits the knee of the curve. Even those who acknowledge exponential growth underestimate how capabilities can improve.
To predict new advances, turn innovation into a process
“We spend 70 percent of our time on core search and ads. We spend 20 percent on adjacent businesses, ones related to the core businesses in some interesting way. Examples of that would be Google News, Google Earth, and Google Local. And then 10 percent of our time should be on things that are truly new.”
– Eric Schmidt, Google
- Don’t get caught in the trap of refining your core processes to the exclusion of innovation. You should always be looking for new processes to improve, new technology to pilot, and where possible, new businesses to get into.
- Devote about 10% of your time and resources to exploring new technology: the potential rewards are huge.
You and your team need to analyze technology every year to predict where it’s going.
|
|
Protect IT and the business from disruption by implementing a simple, repeatable disruptive technology exploitation process
“One of the most consistent patterns in business is the failure of leading companies to stay at the top of their industries when technologies or markets change […] Managers must beware of ignoring new technologies that can’t initially meet the needs of their mainstream customers.”
– Joseph L. Bower and Clayton M. Christensen
|
Challenge |
Solution |
|---|---|
|
New technology can hit like a meteor, but it doesn’t have to leave a crater: |
Use the annual process described in this blueprint to create a formal evaluation of new technology that turns analysis into action. |
|
Predicting the future isn’t easy, but it can be done: |
Lead the analysis from the office of the CIO. Establish a team to carry out the annual process as a cure for airline magazine syndrome. |
|
Your role is endangered, but you can survive: |
Train your team on the patterns of progress, track technology over time in a central database, and read Info-Tech’s analysis of upcoming technology. |
|
Communication is difficult when the sky is falling, so have a simple way to get the message across: |
Track metrics that communicate your progress, and summarize the results in a single, easy-to-read exploitation plan. |
Info-Tech Insight
Use Info-Tech’s tools and templates, along with this storyboard, to walk you through creating and executing an exploitation process in six steps.
Create measurable value by using Info-Tech’s process for evaluating the disruptive potential of technology

|
No business process is perfect.
|
Info-Tech Insight
Inevitably, some proof of concept projects will not benefit the organization. The projects that are successful will more than cover the costs of the failed projects. Roll out small scale and minimize losses.
Establish your key performance indicators (KPIs)
Key performance indicators allow for rigorous analysis, which generates insight into utilization by platform and consumption by business activity.
- Brainstorm metrics that indicate when process improvement is actually taking place.
- Have members of the group pitch KPIs; the facilitator should record each suggestion on a whiteboard.
- Make sure to have everyone justify the inclusion of each metric: how does it relate to the improvement that the proof of concept project is intended to drive? How does it relate to the overall goals of the business?
- Include a list of KPIs, along with a description and a target (ensuring that it aligns with SMART metrics).
| Key Performance Indicator | Description | Target | Result |
|---|---|---|---|
|
Number of Longlist technologies |
Establish a range of Longlist technologies to evaluate | 10-15 | |
| Number of Shortlist technologies | Establish a range of Shortlist technologies to evaluate | 5-10 | |
| number of "look to the past" likes/dislikes | Minimum number of testing characteristics | 6 | |
| Number of POCs | Total number of POCs Approved | 3-5 |
Communicate your plan with the Disruptive Technology Exploitation Plan Template
Use the Disruptive Technology Exploitation Plan Template to summarize everything that the group does. Update the report continuously and use it to show others what is happening in the world of disruptive technology.
| Section | Title | Description |
|---|---|---|
| 1 | Rationale and Summary of Exploitation Plan | A summary of the current efforts that exist for exploring disruptive technology. A summary of the process for exploiting disruptive technology, the resources required, the team members, meeting schedules, and executive approval. |
| 2 | Longlist of Potentially Disruptive Technologies | A summary of the longlist of identified disruptive technologies that could affect the organization, shortened to six or less that have the largest potential impact based on Info-Tech’s Disruptive Technology Shortlisting Tool. |
| 3 | Analysis of Shortlist | Individually analyze each technology placed on the shortlist using Info-Tech’s Disruptive Technology Value-Readiness and SWOT Analysis Tool. |
| 4 | Proof of Concept Plan | Use the results from Section 3 to establish a plan for moving forward with the technologies on the shortlist. Determine the tasks required to implement the technologies and decide who will complete them and when. |
| 5 | Hand-off | Pass the project along to identified stakeholders with significant interest in its success. Continue to track metrics and prepare to repeat the disruptive technology exploitation process annually. |

 Exploit Disruptive Infrastructure Technology
Exploit Disruptive Infrastructure Technology
 2020 Infrastructure Priorities Report
2020 Infrastructure Priorities Report
 Infrastructure & Operations Priorities 2022
Infrastructure & Operations Priorities 2022
 Create and Implement an IoT Strategy
Create and Implement an IoT Strategy
 Infrastructure and Operations Priorities 2023
Infrastructure and Operations Priorities 2023
 Infrastructure & Operations Priorities 2024
Infrastructure & Operations Priorities 2024
 Infrastructure & Operations Priorities 2025
Infrastructure & Operations Priorities 2025
 Building Info-Tech’s Chatbot
Building Info-Tech’s Chatbot
 Assessing the AI Ecosystem
Assessing the AI Ecosystem
 Building the Road to Governing Digital Intelligence
Building the Road to Governing Digital Intelligence
 Bring AI Out of the Shadows
Bring AI Out of the Shadows
 The AI Vendor Landscape in IT
The AI Vendor Landscape in IT
 An Operational Framework for Rolling Out AI
An Operational Framework for Rolling Out AI
 Infrastructure and Operations Priorities 2026
Infrastructure and Operations Priorities 2026