- The rate of technological change is accelerating. Organizations continue to invest in technology to run the business, layering more systems to support remote work, enhance customer experience, and generate value.
- Meanwhile, security threats are growing. Disruptive cyberattacks are more prevalent, sophisticated, and impactful than ever, targeting organizations of all industries and sizes.
- Security leaders need to adopt a proactive approach to secure the organization now and prioritize funding to high-risk areas.
Our Advice
Critical Insight
- Technological change is increasing both the protect surface and the variety of tools available to secure it.
- Security frameworks are helpful, but they don’t describe how to gather business requirements, identify organizational risks, or set an appropriate target state for the program, or which controls to select to conduct an accurate gap analysis for the security program.
- Security leaders in smaller enterprises often have to accomplish more with fewer resources.
Impact and Result
Build a business-aligned, risk-aware, holistic security strategy:
- Gather business requirements to prioritize improvements.
- Assess risks, stakeholder expectations, and risk appetite to set meaningful targets.
- Do a comprehensive gap analysis to identify improvements.
- Build a flexible roadmap to set the program on the right footing.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
9.8/10
Overall Impact
$19,239
Average $ Saved
40
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
Triad Technologies, LLC
Guided Implementation
10/10
$2,720
20
Ahmad provided great insight into how I could use the InfoTech tools to help close gaps in my own security management processes. I appreciated his ... Read More
Campus USA Credit Union
Guided Implementation
10/10
$13,600
20
Having someone to bounce ideas off of and give feedback was the best experience. The worst experience was having to switch analysts midway through... Read More
Office of the Commissioner of Official Languages of Canada
Guided Implementation
9/10
$25,000
20
Eswatini Railway
Guided Implementation
10/10
$35,638
120
No worst parts. Working with Mr. Viktor Okorie was exceptional. He went above and beyond for us given that we had only 4 weeks to formulate our str... Read More
Ames Tile & Stone
Guided Implementation
10/10
N/A
20
INFO-TECH RESEARCH GROUP
Build an Information Security Strategy for Small Enterprises
Small enterprises need a security strategy just like any other sized enterprise.
EXECUTIVE BRIEF
Analyst Perspective
Organization size does not matter when it comes to cybersecurity threats and threat actors. Small, medium, or large, you need an information security strategy!
When threat actors attempt to exploit a known vulnerability for common services and applications, they do not select targets based on the size of the organization. They scan IP addresses and systematically move along a range, hoping to stumble upon an open port or unaddressed vulnerability. They have one goal in mind, and that is to gain access to your environment. Once they are in, then they go to work to create whatever form of havoc falls into their method of operating. They don’t avoid small businesses. They don’t care. Information is worth money, and they want to make money.
So, if threat actors don’t care about the size of your organization, should you approach these threats against your organization any differently than a larger organization?
No, you should not!
The specific tools may differ, external resources may be needed to complement a smaller IT security team, but you still need an approach or strategy, just like the larger organizations.
A strategy that includes assessing and aligning with the business requirements, identifying where security gaps exist, prioritizing initiatives, and building a security strategy roadmap should be your goal.

|
P.J. Ryan
|
Executive Summary
Your Challenge
- The rate of technological change is accelerating. Organizations continue to invest in technology to run the business, layering more systems to support remote work, enhance customer experience, and generate value.
- Meanwhile, security threats are growing. Disruptive cyberattacks are more prevalent, sophisticated, and impactful than ever, targeting organizations of all industries and sizes.
- Security leaders need to adopt a proactive approach to secure the organization now and prioritize funding to high-risk areas.
Common Obstacle
- Technological change is increasing both the protect surface and the variety of tools available to secure it.
- Security frameworks are helpful, but they don’t describe how to gather business requirements, identify organizational risks, or set an appropriate target state for the program, or which controls to select to conduct an accurate gap analysis for the security program.
- Security leaders in smaller enterprises often have to accomplish more with fewer resources.
Info-Tech’s Approach
Build a business-aligned, risk-aware, holistic security strategy:
- Gather business requirements to prioritize improvements.
- Assess risks, stakeholder expectations, and risk appetite to set meaningful targets.
- Conduct a comprehensive gap analysis to identify improvements.
- Build a flexible roadmap to set the program on the right footing.
Info-Tech Insight
Small enterprises are just as much at risk from cybersecurity threats as larger enterprises. Threats and threat actors do not pass you by just because you are smaller. They view you and your enterprise as an opportunity just like any other enterprise.
Your challenge
The stakes for information security programs have never been greater.
- The rate of technological change is accelerating. Organizations continue to invest in technology to run the business, layering more systems to support remote work, enhance customer experience, and generate value.
- Meanwhile, security threats are growing. Disruptive cyberattacks are more prevalent, sophisticated, and impactful than ever, targeting organizations of all industries and sizes.
- Information security incidents were ranked as the most important business risk worldwide for the second year in a row according to the Allianz Risk Barometer 2023.
- According to Cybersecurity Ventures, the cost of cybercrimes worldwide will grow by 15% year over year for the next five years, reaching US$10.5 trillion annually by 2025, up from US$3 trillion in 2015.
- Security leaders need to adopt a proactive approach to secure the organization now and prioritize funding to high-risk areas.
Your challenge
The average cost of security incidents is reaching an all-time high.
- 83% — Percent of organizations that have had more than one breach in 2022.
- US$4.45 million — Average cost of a data breach in 2023.
- US$5.13 million — Average cost of a ransomware attack, not including the cost of the ransom.
(Source: IBM, 2022, 2023.)
Your challenge
Common attacks persist, which suggests that most are still not getting security fundamentals right.
- 66% — Organizations hit by ransomware in 2021 and 2022. (Sophos, 2022, 2023.)
- 35% — Organizations who conducted phishing simulations in 2022. (Ponemon, 2023.)
- 84% — Organizations who experienced phishing attacks with direct financial loss in 2022. (Ponemon, 2023.)
Small enterprises are considered easy targets
Misconception
Small enterprises are less targeted in cyberattacks due to smaller or less valuable assets.
54% of small businesses think they’re too small for a cyberattack. (Source: Cisco Umbrella, 2021.)
Unfortunately, this misconception is often held by nontechnical leaders who set the strategic priorities for the organization, including IT.
Reality
Small enterprises are often the primary target, as they are perceived as lacking the capabilities and resources needed to prevent attacks, and successful attacks generally garner less attention and recourse from the appropriate authorities.
61% of small and midsize businesses were the target of a cyberattack in 2021. (Source: TitanHQ, 2023.)
43% of all cyberattacks target small businesses. (Source: Cisco Umbrella, 2021.)
To properly build an information security strategy, you need to involve and educate certain stakeholders to discuss the reality of the threats, their direct and specific impact on the business, and what the organization needs to protect itself from inevitable attack.
Cyberattacks and breaches hit small enterprises harder
Organizations need to expect and prepare for the inevitable security breach.
- 94.6% of breaches have a financial motive. (Source: Verizon, 2023.)
- 145% increase in malicious emails aimed at small businesses’ inboxes in 2022. (Source: Infosecurity Magazine, 2023.)
- 75% of small businesses could not continue operating if they were hit with ransomware. (Source: StrongDM, 2023.)
The full extent of damage from an attack can extend past the loss of data and finances. Reputational damage as a vulnerable entity can cost small enterprise organizations critical relationships that they depend on to survive.
Financial consequences of security incidents for small enterprises:
- $2.8 billion in damages from over 700,000 attacks against small businesses in 2020.
- 51% of small businesses that fall victim to ransomware pay the money.
- 95% of cybersecurity incidents at small businesses cost between $826 and $653,587. (Source: StrongDM, 2023.)
How well can your business handle a $653,587 hit right now?
Common obstacles
Reactive security strategies can’t keep up.

Limited Resources:
All is not lost.
You may not have a team of 20 to focus on your cybersecurity program, but that doesn’t mean you can’t still have a first-class security program.
Several options exist that could assist you with any resource challenges related to your security strategy implementation.
Third-party security service providers
- Varying in size and type of offerings, these can be a great source of support or staff augmentation.
Info-Tech’s Cybersecurity Workforce Development Program
- Train your internal team to close your cybersecurity skill gaps and build cyber resiliency.
Info-Tech’s Technical Counselor membership
- Personalized and confidential one-on-one support from a seasoned IT executive to enhance your technical expertise, achieve your goals, and prepare for the next chapter of your career.
Excuses will not protect your organization, and clearly the threat is not going away.
“Cybercriminals will continue to evolve new TTPs, including targeting more small- and medium-sized organizations, in order to avoid attention-grabbing higher profile attacks.” (Canadian Centre for Cyber Security, 2023)
Third-party security service providers
Short-term or long-term, one initiative or a full project: Help is out there.
Many consulting organizations employ staff with security backgrounds.
These organizations offer many options. Some can provide strategy or roadmap guidance while others may provide some “security as a service” options such as:
- Event log monitoring.
- Resolving alerts triggered by antivirus or anti-malware systems.
- Security tool implementation.
- Security assessments.
- Security related purchase assistance/guidance.
“If you have one person responsible for watching the logs and events, what happens during the after-hours or when that person goes on vacation? With an outsourced monitoring service, you get access to a team of experts watching your logs and alerts, and taking action, 24 hours a day, 365 days a year.” (Kevin Critch, Regional Sales Director, Ignite Technology)
Info-Tech’s cybersecurity workforce development
Upskill your IT team by going beyond certifying knowledge to assuring competence.
Close competency gaps with Info-Tech’s Cybersecurity Workforce Development Training.
Resources to close competency gaps:
Info-Tech’s cybersecurity workforce training develops critical cybersecurity skills missing within your team and organization. The leadership track provides the same deep coverage of technical knowledge as the analyst track but adds hands-on support and has a focus on strategic business alignment, program management, and governance.
The program builds critical skills through:
- Standardized curriculum with flexible projects tailored to business needs.
- Realistic cyber-range scenarios.
- Ready-to-deploy security deliverables.
- Real assurance of skill development.
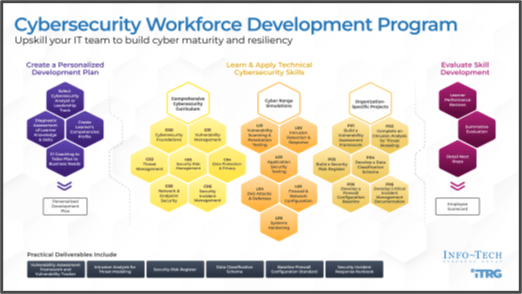
Learn more on the Cybersecurity Workforce Development webpage
TECHNICAL COUNSELOR MEMBERSHIP
The Technical Counselor is designed to help IT leaders deliver value, achieve goals, and improve and grow the contributions of IT with a focus on technical excellence. It also includes all People & Leadership content required to manage a team and develop as a leader.
Service Delivery
Dedicated Technical Counselor
Members receive personalized and confidential one-on-one support from a seasoned IT executive to enhance their technical expertise, achieve their goals, and prepare for the next chapter of their career.
Also Includes:
- 2 Onsite/Virtual Counselor Visits
- Custom Key Initiative Plan
- Designated Account Manager
Technical Domains:
- Applications
- Infrastructure & Operations
- Security
- Data & Analytics
- Enterprise Architecture
- Privacy
- PMO
- Vendor Management
- Service Management
Research Content
Project Blueprints
Over 450 step-by-step project methodologies to help members execute technology projects and improve core IT processes.
Tools & Templates Library
Over 1,000 ready-to-deploy tools and templates to save members time creating critical IT documents and project deliverables.
Software Selection Content
SoftwareReviews vendor evaluations and rankings reports that aggregate feedback from real IT professionals and business leaders.
People & Leadership Research
Strategies on how to lead teams effectively and resources proven to help you become a better manager.
Also Includes:
- IT Process Research

Sample Template

Sample Data Quadrant Report
Advisory Services
Unlimited Analyst Calls
Unlimited phone access to our team of subject matter experts to guide you through your most challenging technology projects. An analyst from the team who wrote the research works with the member at key project milestones to advise, coach, and offer insight.
Industry Research & Advisory
In-depth, industry-specific research content and advisory service that includes benchmarking reports, trends analysis, technology evaluations, and reference architectures. This feature can be added to the membership as a substitution for onsite visits.
IT Vendor Price Benchmarking & Negotiation Assistance
Access to our IT pricing experts and exclusive negotiation intelligence to achieve best-in-circumstance deals on $1 million plus contract value covering 40 plus major IT vendors. IT Vendor Negotiation Assistance for up to three contracts included with membership.
Also Includes:
- Concierge Services
- Software Selection as a Service
- Contract Review Service
- Info-Tech LIVE Ticket
Digital Experiences
IT Diagnostic Programs
Over 20 prebuilt survey programs to ask business and IT stakeholders insightful questions and convert their responses into reports that help IT departments make critical decisions.
Also Includes:
- Info-Tech Academy Training Platform
- IT Metrics Dashboard
- Leadership Development Program
- 360-Degree Feedback Tool

Sample Diagnostic Report

Sample Video Content
Info-Tech’s approach
Build a proactive security strategy.

Use a best-of breed model based on leading frameworks


Info-Tech’s methodology for building an information security strategy for small enterprise
1. Assess Business Requirements |
2. Conduct a Gap Analysis |
3. Build a Roadmap of Prioritized Initiatives |
4. Execute & Maintain a Strategy |
|
Phase Steps |
1.1 Define goals & scope 1.2 Assess risks 1.3 Determine pressures 1.4 Determine risk appetite 1.5 Establish target state |
2.1 Review security framework 2.2 Assess your current state 2.3 Identify gap closure actions |
3.1 Define tasks & initiatives 3.2 Perform cost-benefit analysis 3.3 Prioritize initiatives 3.4 Build roadmap |
4.1 Build communication deck 4.2 Execute on your roadmap |
Phase Outcomes |
|
|
|
|
Tools |
Information Security Requirements Gathering Tool; Information Security Pressure Analysis Tool | Information Security Program Gap Analysis Tool | Information Security Program Gap Analysis Tool | Information Security Strategy Communication Deck |
Insight summary
Small enterprises are just as much at risk from cybersecurity threats as larger enterprises.
Threats and threat actors do not pass you by just because you are smaller. They view you and your enterprise as an opportunity just like any other enterprise.
Your security strategy is a business strategy first.
A well-defined information security strategy is holistic, risk aware, and business-aligned.
Assess business requirements
Protecting the organization means taking on enough risk to enable the organization to meet its objectives.
Seek agreement on the program target state
Higher target states require more investment. Ensure stakeholders agree on the maturity of the program you need from the start to ensure continued support.
Prioritize initiatives and roadmap
Express the benefit of security initiatives in terms of their impact on what matters – the key strategic goals that drive decision making at your organization.
Execute and maintain strategy
Reinforce the concept that a security strategy is an effort to enable the organization to achieve its core mission within its risk appetite.
Blueprint deliverables
Key deliverable:
Information Security Strategy Communication Deck
Present your findings in a prepopulated document that can summarizes all key findings of the blueprint.

Each step of this blueprint is accompanied by supporting deliverables to help you accomplish your goals:
Information Security Requirements Gathering Tool
Define the business, customer, and compliance alignment for your security program.
Information Security Program Gap Analysis Tool
Use our best-of-breed security framework to perform a gap analysis between your current and target states.
Information Security Pressure Analysis Tool
Determine your organization’s security pressures and ability to tolerate risk.
