As organizations increasingly rely on third-party vendors to support critical objectives, they also open themselves up to more security risks and points of entry for malicious actors. An effective and efficient security assessment process is essential to managing this risk. Our framework helps security leaders streamline their vendor assessment process and create right-sized vendor security plans for your organization’s needs.
Vendor security risk management is a growing concern for many organizations, and regulatory expectations in this area are also growing. However, traditional approaches to vendor security assessments are seen by business partners and vendors as too onerous and are unsustainable for information security departments. A right-sized vendor security assessment service will efficiently manage risk, meet requirements, and leave more time to address critical threats.
1. Right-size the process with a risk-based approach
Putting risk at the core of your assessment process is the best way to meet your vendor due diligence goals. Security assessments are time-consuming for both you and your vendors – maximize the returns by scaling your assessments to the associated risk and access provided. Not all vendors are the same, so taking a one-size-fits-all approach is a fast way to lose time, resources, and vendors.
2. Include all key players from the get-go
An effective and efficient assessment process can only be achieved when all key players are participating. Identifying business requirements, customer expectations, and compliance obligations will require input from many areas of your organization. Take the time to include all key players from the beginning and leverage existing processes to aid your requirement discovery.
3. Design an end-to-end process
A one-and-done process for vendor security can introduce risks that grow in the shadows without proper visibility. Though your initial contract with a vendor may involve minimal risk, new work and additional risk may be added as your relationship with the vendor develops. Effective vendor security risk management is an end-to-end process that must involve periodic reassessments.
Use our comprehensive framework to establish a risk-based vendor security assessment program
Use this step-by-step framework, featuring a robust set of tools and templates, to establish, evaluate, and maintain your right-sized vendor security assessment program. Our framework incorporates your existing security policies and provides customizable questionnaire templates aligned with risk tolerance and service level to assess vendors.
- Scale your assessment to the level of risk given to each vendor and the scope of their service.
- Leverage AI to augment your assessment process and accelerate audit report reviews.
- Monitor the process to avoid outdated security assessments and changing regulatory requirements.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
8.8/10
Overall Impact
$24,855
Average $ Saved
9
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
Heritage Petroleum Co Ltd
Guided Implementation
8/10
$64,600
20
The best part of the experience included Mike's availability, clear, concise communication and streamlined approach to providing the solution.
FlexiVan Leasing, Inc
Guided Implementation
10/10
$13,600
4
Norseman Inc
Guided Implementation
10/10
N/A
1
No bad parts. Jon was able to explain the process with simplicity and therefore make it easy for me to complete it.
Leeds Beckett University
Guided Implementation
10/10
$92,499
20
Jon has the right blend of expertise, patience and interpersonal skills to help land the insights from Infotech, we'll be coming back: nothing bad ... Read More
Jefferson Center for Mental Health
Guided Implementation
10/10
N/A
5
Petar was amazingly helpful, knowledgeable, and efficient in the use of our time together. I feel supported in next steps.
City of Santa Fe
Guided Implementation
10/10
N/A
N/A
I am most grateful for Jon Nelson's help as an InfoTech Analyst with guiding me and my team towards a working Cyber Security Strategic Plan and man... Read More
Pittsburgh Water
Guided Implementation
10/10
N/A
20
Jon is very knowledgeable about Info-Tech tools and is able to provide helpful answers to all of our questions. For example, on the recent call he... Read More
US Senate
Guided Implementation
3/10
N/A
5
Petar was very knowledgeable SME. He shared valuable information, materials and gave solid advice for our initiative. Petar also provided us the op... Read More
The University of North Carolina System Office
Guided Implementation
7/10
$2,584
4
Access to ready templates. Worst part is the manual manner in which I will have to use the templates.
Nippon Sanso Holdings Corporation
Guided Implementation
8/10
$6,359
4
Cidel Bank & Trust
Guided Implementation
10/10
$13,700
5
no worse parts. Everything was well presented with Jon providing valuable insight on the importance of monitoring and managing vendor risk and h... Read More
Westoba Credit Union Limited
Guided Implementation
10/10
$5,000
10
It's really valuable to have this work ready to be used instead of building it myself.
Driv Incorporated
Guided Implementation
8/10
$50,000
20
Build a Vendor Security Assessment Service
Use a risk-based approach to right-size your vendor security assessments.
Analyst Perspective
Streamlining vendor assessment efforts through risks.
With the increase in third-party attacks and their adverse impacts, many organizations are struggling with managing vendor security risks through traditional approaches. Too much due diligence discourages vendors from bidding for your business, exasperates internal clients, and strains resources of security teams. These challenges are further exacerbated by increased expectations from regulators to strengthen vendor security risk management.
The solution is to rethink supply chain security and take a risk-based approach that will satisfy all stakeholders.
Streamlining the vendor security assessment process through a risk-based approach will improve efficiency by identifying and treating risks based on the service risks and organization's risk tolerance levels, respectively. Furthermore, a process that fosters continuous improvement in the vendor security risk management program will enable monitoring and improvement based on appropriate and relevant metrics, which will help identify further enhancements to the assessment.
Building an effective vendor security assessment service will contribute to the advancement of an organization's security risk management, which will integrate with the enterprise risk management program to drive innovation and provide visibility, which will in turn help to inform good decision-making across the organization.

Ahmad Jowhar
Research Analyst, Security & Privacy
Info-Tech Research Group
Executive summary
Your Challenge
- Vendor security risk management is a growing concern for many organizations. We often trust our suppliers and business partners with our most sensitive data and processes.
- More and more regulations require vendor security risk management, and regulator expectations in this area are growing.
- Increased reliance on vendors makes it more difficult for organizations to manage and treat third-party risks.
Common Obstacles
- Too many security leaders start with a one-size-fits-all approach to vendor security assessments and end their engagement as soon as a vendor is selected.
- Security assessments that are too onerous will lead to vendors refusing to bid for your business, driving the business to bypass your assessment process.
Info-Tech's Approach
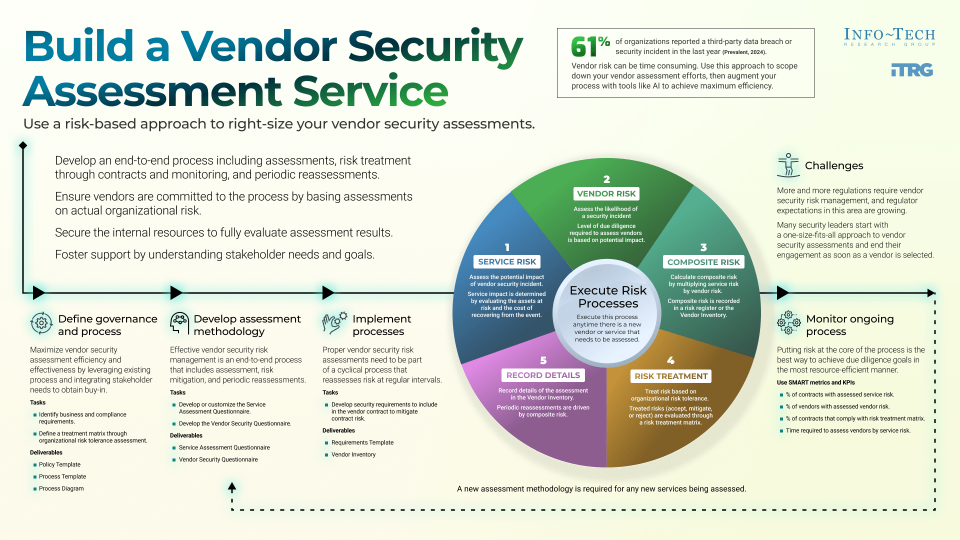
- Develop an end-to-end security risk management process that includes assessments, risk treatment through contracts and monitoring, and periodic reassessments.
- Base your vendor assessments on the actual risks to your organization to ensure that your vendors are committed to the process and you have the internal resources to fully evaluate assessment results.
- Understand your stakeholder needs and goals to foster support for vendor security risk management efforts.
Info-Tech Insight
Assessing vendor risk can be very time-consuming. Use risk to scope down your efforts, and augment your process with tools and AI to achieve maximum efficiency.
Common obstacles
Organizations are not ready to efficiently mitigate third-party risks.
The increasing incidence of third-party attacks has resulted in organizations placing emphasis on the management of their vendors, which includes security assessments to identify and mitigate the security risk to the business.
However, too many security leaders start with a one-size-fits-all approach to vendor security assessments and end their engagement as soon as a vendor is selected, which lacks the strategic approach of assessing vendors through a risk-based lens and continuously monitoring the process until the vendor is offboarded.
Security assessments that are too onerous will lead to vendors refusing to bid for your business, driving the business to bypass your assessment process.
A vendor security assessment methodology that lacks relevant questionnaires, service and vendor risk assessments, and applicable risk treatment plans will result in an inefficient vendor security risk management program that will be time-consuming and bring additional risk to the organization.
| 61% |
of organizations reported a third-party data breach or security incident in the last year. |
|---|---|
| 75% |
of third-party breaches involved a technology or software. |
| 33% |
of vendor relationships are managed by organizations. |
Info-Tech's methodology for building a vendor security assessment service
|
1. Define Governance |
2. Develop Assessment |
3. Implement Process |
|
|---|---|---|---|
|
Phase Steps |
|
|
|
|
Phase Outcomes |
|
|
|
Insight summary
Invest your efforts in your riskiest vendors
Assessing vendor risk can be very time-consuming. Scope down your efforts by prioritizing the riskiest services, and augment your process with tools and AI to achieve maximum efficiency.
Engage all stakeholders to ensure efficiency and effectiveness
Maximize the efficiency and effectiveness of your vendor security assessment by leveraging existing processes and obtaining buy-in from stakeholders by integrating their needs into the process.
Right-size the process with a risk-based approach
Putting risk at the core of the process is the best way to achieve your vendor due diligence goals in the most resource-efficient manner possible.
Design an end-to-end process
A one-and-done process for vendor security can introduce risks that grow in the shadows without proper visibility, especially when business units contract a vendor for a low-risk service and then begin granting them riskier and riskier business arrangements without updating the original contract.
Not all vendors are the same
Taking a one-size-fits-all approach to vendor security risk management and treating all vendors the same way is the fastest way to fail.
Periodic reassessments are key
Proper vendor security risk assessments need to be part of a cyclical process that reassesses risk at regular intervals.
Blueprint deliverables
Each step of this blueprint is accompanied by supporting deliverables to help you accomplish your goals:
|
Vendor Security Policy Template |
A policy template mapped to various regulations and standards that outlines vendor security. |

|
|---|---|---|
|
Vendor Security Process Template |
A process template with a RACI matrix and process diagrams to depict the process for different contract phases. |

|
|
Vendor Security Process Diagram |
A process flowchart depicting the vendor security assessment process for different contract phases. |

|
|
Vendor Security Requirements Template |
A template containing security requirements that organizations can include within vendor contracts to mitigate identified security risks. |

|
Key deliverables:
|
Service Risk Assessment Questionnaire |

|
|---|---|
|
Vendor Security Questionnaire |

|
|
Vendor Security Assessment Inventory |
Blueprint benefits
|
IT Benefits |
Business Benefits |
|---|---|
|
|
This research aligns with Info-Tech's overall vendor management framework

Info-Tech offers various levels of support to best suit your needs
DIY Toolkit
"Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful."
Guided Implementation
"Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track."
Workshop
"We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place."
Consulting
"Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project."
Diagnostics and consistent frameworks are used throughout all four options.
Guided Implementation
What does a typical GI on this topic look like?

A Guided Implementation (GI) is a series of calls with an Info-Tech analyst to help implement our best practices in your organization.
A typical GI is 6 to 12 calls over the course of 4 to 6 months.
Workshop overview
Contact your account representative for more information.
workshops@infotech.com 1-888-670-8889
|
Day 1 |
Day 2 |
Day 3 |
Day 4 |
Day 5 |
|
|---|---|---|---|---|---|
|
Define Governance |
Develop Assessment Methodology |
Continued Development of Assessment Methodology |
Deploy Process |
Next Steps and |
|
|
Activities |
1.1 Review current processes and pain points. |
2.1 Identify organizational |
3.1 Customize Vendor |
4.1 Customize Vendor Security Requirements Template. |
5.1 Finalize deliverables. |
|
Deliverables |
|
|
|
|
|
Measure the value of this blueprint
An effective vendor security assessment service will have a measurable impact to your security program
|
Phase |
Measured Value |
|---|---|
|
Phase 1: Define Governance |
Cost to define governance, policy, and process:
|
|
Phase 2: Develop |
Cost to define service risk and vendor risk methodologies:
|
|
Phase 3: Deploy and |
Cost to define deployment strategic and metrics:
|
|
Potential Savings |
Total estimated effort = $12,800 By using our Guided Implementation rather than a self-directed implementation, you can expect to save ~75% of the overall cost, which represents ~$9,600. |
|
59% |
of organizations have had a data breach caused by third parties that resulted in misuse of sensitive information. |
|---|
Case study
Reducing risk, improving productivity, and achieving compliance in the vendor security assessment process
INDUSTRY: Higher Education
SOURCE: "Case Study," SecurityScorecard, 2024
Challenge
A US-based Tier 1 research institution was dealing with an increased cybersecurity attack surface due to the expanded collaborations of interdisciplinary research and peer review among universities. Being a small cybersecurity shop of dedicated staff, it lacked resources to assist in the development of an effective third-party risk management program.
Solution
SecurityScorecard collaborated with the university's cybersecurity operations team to streamline vendor security verification, saving time and increasing confidence in assessments. An automated vendor questionnaire allowed seamless cross-referencing of security posture claims with actual maturity, reducing manual checks and enabling the team to focus on critical tasks. This collaboration helped build a resilient vendor security management practice.
Results
The team reduced third-party data breach risks by adopting security reviews during procurement and working with stakeholders to meet business needs while strengthening security. It also ensured compliance with the Cybersecurity Maturity Model Certification (CMMC) 2.0, necessary for obtaining research funding. The solution addressed key CMMC 2.0 components, including subcontractor monitoring.
Phase 1
Define Governance and Process
| Phase 1 |
Phase 2 |
Phase 3 |
|---|---|---|
|
1.1 Identify requirements 1.2 Develop policy 1.3 Identify roles 1.4 Define process 1.5 Define treatment matrix |
2.1 Assess service risk 2.2 Develop questionnaire 2.3 Technical assessments 2.4 Other vendor assessments 2.5 Assess vendor risk |
3.1 Treat risks 3.2 Deploy process 3.3 Monitor the process |
This phase will walk you through the following activities:
1.1 Identify requirements.
1.2 Develop a vendor security policy.
1.3 Identify roles.
1.4 Define process.
1.5 Define treatment matrix.
Outcome:
- Defined governance structure for your vendor security assessment program
This phase involves the following participants:
- Information Security
- IT Risk
- Vendor Management
- Privacy & Compliance
- Business
Build a Vendor Security Assessment Service
1.1 Define requirements for vendor security assessments
60 minutes
Gather the required participants and use a whiteboard to brainstorm and capture requirements within the following categories.
- Identify business requirements: Failure to identify business goals can result in a vendor assessment service that does not deliver required outcomes.
- Identify customer experience: Most customers expect organizations to safeguard their data, including when it is being processed by fourth parties.
- Identify compliance obligations: Regulators and legislators are becoming more interested in how regulated organizations manage risk, including vendor risk.
The following slides provide more information on this step.
Download the Information Security Requirements Gathering Tool
|
Input |
Output |
|---|---|
|
|
|
Materials |
Participants |
|
|
1.1.1 Identify business requirements
To determine business requirements, ask stakeholders leading questions. Some examples may include:
|
Question |
Business requirement if "Yes" |
|---|---|
|
Do you rely on critical suppliers where a disruption in service delivery would have a significant impact on organizational functions? |
Ensure that vendor security practices minimize risks to availability. |
|
Do you often share sensitive data with vendors such that a data breach at a critical supplier would have significant reputational and other impacts? |
Ensure that vendor security practices minimize risks to confidentiality. |
|
Is time to market an important goal? |
Reduce time required for vendor selection and onboarding. |
|
Do you expect your reliance on vendors to increase in the future? |
Maximize efficiencies in vendor risk management. |
Info-Tech Insight
Security activities must support business objectives. An effective and efficient vendor security program will enable the business to leverage the supply chain in new and creative ways rather than acting as an obstacle to the achievement of goals.
1.1.2 Identify customer expectations
Today, most customers or clients expect some level of security to protect their data.
For many organizations, customer data privacy is arguably the largest driving factor for developing a mature IT security program.
- Repeat the same process you use to identify business requirements to elicit customer expectations as they relate to vendor security risk management.
- For organizations that deal primarily with consumers, these expectations are likely along the lines of "Protect customer data while it is being transmitted to and processed by vendors."
- Organizations whose customers are primarily institutional should review major contracts to identify customer security requirements.
Info-Tech Insight
When reviewing contracts with your business customers, look for requirements related to subcontractors or fourth parties. These will be relevant to how you manage the security of your vendors.
1.1.3 Identify compliance obligations
Regulators are increasingly focusing on how regulated organizations manage vendor risk. Identify compliance obligations by consulting with your Legal, Privacy, and Compliance teams and extracting relevant security requirements.
Examples include:
|
PCI |
Maintain and implement policies and procedures to manage service providers with whom cardholder data is shared or that could affect the security of cardholder data. |
|---|---|
|
GDPR |
Where processing is to be carried out on behalf of a controller, the controller shall use only processors providing sufficient guarantees to implement appropriate technical and organizational measures in such a manner that processing will meet the requirements of this regulation and ensure the protection of the rights of the data subject. |
|
NIST 800-53 |
The organization conducts a supplier review prior to entering into a contractual agreement to acquire the information system, system component, or information system service. |
You may also ask stakeholders if they are aware of increasing regulator interest in this area or if you have been subject to external audits that are testing controls related to vendor security.

 Develop and Implement a Security Incident Management Program
Develop and Implement a Security Incident Management Program
 Build Resilience Against Ransomware Attacks
Build Resilience Against Ransomware Attacks
 Build a Vendor Security Assessment Service
Build a Vendor Security Assessment Service
 Implement Risk-Based Vulnerability Management
Implement Risk-Based Vulnerability Management
 Improve Organizational Resilience With a Tabletop Program
Improve Organizational Resilience With a Tabletop Program
 Master Your Security Incident Response Communications Program
Master Your Security Incident Response Communications Program
 Design a Coordinated Vulnerability Disclosure Program
Design a Coordinated Vulnerability Disclosure Program