IT Security Diagnostic Program
Collect the Data You Need to Effectively Manage IT Security
Thinking your organization is sufficiently protected against security threats isn’t good enough. You need to know.
The IT Security Diagnostic Program is a low effort, high impact program designed to help IT Security Leaders assess and improve their security practices. Gather and report on IT Security governance, business satisfaction, and effectiveness to understand where you stand and how you can improve.

Improving IT Security starts here:
Step 1: Assess Current Operations Based on Best Practices

Governance & Management Scorecard
Understand your current strengths and weaknesses, then follow Info-Tech’s customized roadmap of practical and prioritized action items to improve and optimize your security governance and management.

Audience: IT Security Leader
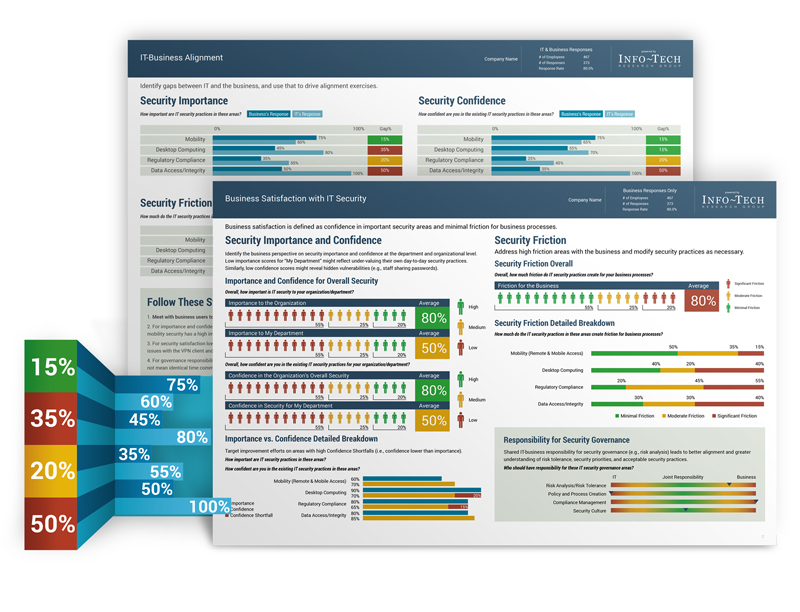
STEP 2: Measure Business Satisfaction and Identify Security Needs
IT Security Business Satisfaction & Alignment
Measure business satisfaction in terms of security confidence and the amount of friction for business processes, and analyse gaps between IT and business perceptions.

Audience: IT Management + Business Leaders
STEP 3: Improve Targeted IT Security Areas
Security Process & Technology Effectiveness
Optimize IT security policies and processes, and drive improvement in technology usage and decisions.

Audience: IT Security Team
-

Governance & Management
-

End User Device Security
-

Server Security
-

Application Security
-

Physical Security
-

IAM
-

Network Security
-

Data Security

Measured Value

Guided Implementation:
IT Security Diagnostic Program
Average Days Saved 28
Average Dollars Saved $11.0k
Client
Experience
$ Saved
Days Saved
GreatAmerica Financial Services
N/A
N/A
I can't put a dollar figure on it right now. And the survey is unforgiving when asking for a dollar amount. Regarding the feedback – it was very good. I received good feedback.
University of West Florida Virtual Campus
N/A
N/A
Verified that our plan is going in the right direction.
Canpotex Limited
$1,000
N/A
Congressional Federal Credit Union
$31,266
6
Maxion Wheels
$6,562
N/A
One of my first engagements with Info-Tech. It gave me a lot of insight into an area where I am a newbie. I also got directions, references, and resources to look into. Thumbs up.
ANSA McAL
$13,124
90
The ability to perform a self evaluation of our security governance was an invaluable starting point for development of our security roadmap. The process was well structured and the analyst was extremely helpful. The greatest challenge is using the information gathered to begin the process now.
Canadian Grain Commission
N/A
N/A
The overall methodology of the survey and the result and recommended actions are all valuable information.
Pittsburgh Corning Corporation
$6,253
8
Consultant needs higher quality voice communication tools... microphone, headset, etc.
Wixon Inc.
$2,501
10
Wesley's input on prioritizing areas for improvement was valuable.
Genworth Financial
N/A
N/A
Best: It confirmed some gaps we thought we had. Worst: Doesn't give a benchmark against other survey participants to show if we are good, better, or worse than others.
Pita Pit Limited
$3,752
10
Completing the survey for the diagnostic was easy. The completed diagnostic report we were given provides a good insight. The adviser was needed to put it in perspective and give clarity on the action steps. The report could be overwhelming otherwise.
Five Points Bank
$6,562
15
Positive and informative interaction. Really appreciate what your team has to offer.
Comprehensive Health Services Inc.
$196K
N/A
Great opportunity to baseline the security program.
University of West Florida
$3,127
3
Good experience; no downside really.
Nuna Logistics Limited
$6,000
5
The diagnostic report is easy to read, follow, and understand and, importantly, it includes recommendations for action with the description of the issues. Going through the report with the security expert from Info-Tech helped us to understand more thoroughly and, through discussion, helped to identify which areas should be our priorities. This will help us move forward quickly and get the most benefits faster.
National Cooperative Bank NA
$1,312
15
No worst aspects, except many of the solutions seem to be designed for mid to large organizations and require many internal resources to complete. Best aspects include confirmation of my analysis and provides insight into areas, processes, or concepts I may not have thought of.
Osage Casino - Tulsa
$6,562
15
Got a ton of information from a very basic set of questions.
Colonial Savings, F.A.
$19,687
30
I find incredible value in the insight provided. The reports are very easy to understand and use in supporting a change or move in a certain direction.
Real Estate One
$6,562
N/A
Best - Validation. Worst - More details on how to execute on direction/vision would save even more time.
Southwest Arkansas Electric Cooperative
$1,313
90
Tons of information.
Paysafe
$3,000
15
Coordination, question assessment, and people.
PPFA Affiliates
N/A
5
All excellent stuff; no down side.
PPFA Affiliates
$3,281
15
I think Info-Tech's guidance is always well-presented and useful, and we're incorporating much of that guidance into our work plans. I'm also most comfortable starting most initiatives at the most basic level of engagement (e.g. downloading blueprints and roadmaps), but sometimes I feel like there's more of a focus on more involved levels of engagement (often outside of the scope of the subscription).
Administrative Office of the Courts, Commonwealth of Kentucky
$1,312
N/A
GreatAmerica Financial Services
N/A
N/A
I can't put a dollar figure on it right now. And the survey is unforgiving when asking for a dollar amount. Regarding the feedback – it was very good. I received good feedback.
Canpotex Limited
$1,000
N/A
Larimer County, Colorado
$13,124
30
A very good experience. It gave me a baseline so that our BRM group can start having meaningful conversations with our customer regarding security.
GreatAmerica Financial Services
N/A
N/A
I can't put a dollar figure on it right now. And the survey is unforgiving when asking for a dollar amount. Regarding the feedback – it was very good. I received good feedback.
Perry Technical Institute
N/A
N/A
Cameron is very helpful.
Sunnybrook Health Sciences Centre
$50,000
N/A
Best - Very structured process and review. Worst - Generalized, rather than specialized knowledge.
Sunnybrook Health Sciences Centre
$50,000
N/A
Best: Structured process. Worst: General expertise.
Everman Independent School District
N/A
N/A
The analyst was very thorough and asked relevant questions to determine how to best use the data to our benefit. The analyst sometimes spoke too rapidly, which made it hard for me to understand him.
St. Jude the Apostle School
$1,000
N/A
Presentation was helpful and informative. Gained some great insights and direction on where to focus.
Toronto District School Board
N/A
N/A
Best - Sharing his experience about how others compare and putting the results in perspective. Worst - Some of the survey questions were ambiguous.
Patented Medicine Prices Review Board
$5,000
N/A
This was a valuable process to walk through. A good experience. Not all aspects are relevant to a very small shop like mine. We have a low budget, and maybe 1/2 or 1/4 resources dedicated to security. We do not have the luxury to put in place some items that are mentioned in the questionnaire.
Edinburgh Airport
$3,404
N/A
FortisAlberta Inc.
N/A
N/A
Elementis Specialties
$65,622
N/A
Very good insight of ELE Security Governance.
Surgi-Care Inc.
$1,000
N/A
I valued the freeform comments in the survey as well as the Info-Tech feedback on the scores.
University of West Florida Virtual Campus
N/A
N/A
Verified that our plan is going in the right direction.
BWX Technologies
$6,562
N/A
Wesley provided great guidance and did a nice job of explaining the report. There were some technical issues that caused a little static in the connection on the second call.
The Chronicle Herald
N/A
N/A
William Osler Health System
$10,000
N/A
Well-presented overall security posture, with attention paid to outstanding issues or questions.
Choctaw Nation of Oklahoma
$19,687
30
Waterloo Regional Police Services
$2,501
4
Overall, it's a good report but it lacks some detail.
Calgary Public Library
$10,000
30
FTI Consulting
$1,500
N/A
The amount of time it took to arrange the meeting.
New Mexico Human Services Department
N/A
5
Sometimes hard to interrupt for questions.
AmSurg
$10,005
10
Delta Dental Plan of Colorado
$18,759
20
Gives us a good baseline to begin from and direction to go.