- CIOs of durable goods manufacturing organizations are under pressure to innovate and comply with growing privacy obligations in different jurisdictions.
- The use of new technologies can allow companies to scale and grow, but it also complicates the landscape of data privacy protection.
- Privacy and data protection are particularly pressing concerns for manufacturers, as the expansion of the internet of things and the collection of massive amounts of data complicates the compliance landscape.
Our Advice
Critical Insight
As manufacturing technologies and processes evolve, data privacy is a significant risk and must be addressed with a high priority. An integrated privacy program that incorporates privacy principles into business processes will be a cost-effective way to safeguard the journey of business enablement.
Impact and Result
- Durable goods manufacturing organizations must establish a unified privacy program that incorporates privacy principles into high-risk business processes.
- You need to provide concrete tools to enable business. Work with business departments by speaking the language they can comprehend and providing tools they can readily implement, such as data privacy policies, procedures, and workflows.
- It is imperative to gain visibility into personal data processing activities such as the types of data collected, business purposes for collecting it, and where it resides, etc.
Operationalize Data Privacy for Durable Goods Manufacturing
Embed privacy by design into your business processes and protect high-risk personal data.
Analyst Perspective
Durable goods manufacturing firms need to embrace digital transformation while also managing the associated data privacy risks.
The durable goods manufacturing industry is undergoing significant changes due to factors such as the adoption of Industry 4.0 technologies, the emergence of a growing consumer class, changes in demographics, and increasing regulations. To remain competitive, manufacturing companies are digitally transforming their business operations.
The adoption of these technologies also brings new risks at the same time. Organizations must take steps to manage these risks. Privacy and data protection are particularly pressing concerns for manufacturers, as the expansion of the Internet of Things and the collection of massive amounts of data complicates the compliance landscape and imposes risks of potential penalties for violations. Moreover, emerging technologies like machine learning and artificial intelligence require vast amounts of data, which raises the risk of data privacy compliance missteps. It is worth noting that many manufacturers lack the expertise to manage data privacy risks effectively.
Durable goods manufacturing firms need to adapt to the changing landscape of their industry and embrace digital transformation while also managing the associated risks, particularly those related to data privacy. By doing so, they can remain competitive and provide value to their clients and stakeholders.

Alan Tang
Principal Research Director, Security & Privacy
Info-Tech Research Group
Executive Summary
Your ChallengeCIOs of durable goods manufacturing organizations are under pressure to innovate and comply with growing privacy obligations in different jurisdictions. The use of new technologies can allow companies to scale and grow but complicates the landscape of data privacy protection. Privacy and data protection are particularly pressing concerns for manufacturers, as the expansion of the Internet of Things and the collection of massive amounts of data complicates the compliance landscape. |
Common ObstaclesManufacturing IT feels less confident in its risk management effectiveness. IT has historically been excluded from risk conversations in this sector. IT needs to gain a seat at the risk management table. Operational technology (OT) and IT organizations often focus their attention within silos and miss the big picture need for a synergistic approach regarding privacy and data protection practices. Budgets are strained and high-level skills are difficult to find and keep. Many manufacturers lack the expertise to manage data privacy risks effectively. |
Info-Tech’s ApproachFor a durable goods manufacturing organization, it is imperative to establish a unified privacy program that incorporates privacy principles into high-risk business processes. You need to provide concrete tools to enable business. It is important to work with business departments by speaking the language they can comprehend and providing tools they can readily implement, such as data privacy policies, procedures, and workflows. It is imperative to gain visibility into personal data processing activities such as the types of data collected, business purposes, and where the data resides. |
Info-Tech Insight
As manufacturing technologies and processes evolve, data privacy is a significant risk and must be addressed with a high priority. An integrated privacy program that incorporates privacy principles into business processes will be a cost-effective way to safeguard the journey of business enablement.
Typical business processes of a durable goods manufacturing organization
The US EPA[1] defines durable goods as products with a lifetime of three years or more, such as large and small appliances, furniture and furnishings, consumer electronics, etc.

Usually, there are three types of business processes supporting the operations of a higher education institution: defining processes, shared processes, and enabling processes.
The diagram above provides a high-level view of business processes. For more detailed information, please see Info-Tech’s Durable Goods Industry Business Reference Architecture Template.
The ones highlighted in amber are the processes that usually collect and process personal information from either customers or employees.
[1] EPA, 2022.
Manufacturing IT: Focus on importance first

#1
Manufacturing industry ranks #1 for attacks. Manufacturing replaced financial services as the top attacked industry in 2021, representing 23.2% of the attacks X-Force remediated last year. Ransomware was the top attack type, accounting for 23% of attacks on manufacturing companies.[2]
61%
Sixty-one percent of incidents at OT-connected organizations last year were in the manufacturing industry. In addition, 36% of attacks on OT-connected organizations were ransomware.[2]
[2] “X-Force Threat Intelligence Index,” IBM Security, 2022.
Top challenges organizations face in building an effective privacy program
The struggle to get a comprehensive data protection and privacy program in place across an entire organization is one of the main challenges for data protection and privacy officers.

Case Study
The Background:
The FTC’s action against toy manufacturer VTech was the first time the FTC became involved in a children’s privacy and security matter. The allegations were that Vtech violated a US children’s privacy law by collecting personal information from children without providing direct notice and obtaining their parent’s consent and failing to take reasonable steps to secure the data it collected.
The Enforcement:
In January 2018, the company entered into a settlement with FTC to pay $650,000, as part of the agreement, to resolve allegations that it collected personal information from children without obtaining parental consent, in violation of the Children’s Online Privacy Protection Act (COPPA). VTech was also required to implement a data security program that is subject to audits for the next 20 years.
Lessons Learned:
Manufacturing companies need to strengthen their privacy and security programs by integrating privacy and security by design into their product management lifecycle in order to compete in the new era.
Source: FTC, 2018.
Info-Tech Insight
Creating a comprehensive, organization-wide data protection and privacy strategy continues to be a major challenge for privacy officers and privacy specialists.
True cost of a data breach
Even with a robust privacy program in place, organizations are still susceptible to a data breach. The benefit comes from reducing your risk of regulatory compliance issues and resulting fines and minimizing overall exposure.[1]

The industrial industry, comprised of chemical, engineering and manufacturing organizations, saw an increase in the cost of a data breach, from US$4.24 million to US$4.47 million in 2022 (an increase of US$0.23 million or 5.4%).
$300K: Cost of one hour of shop floor downtime [2]
[1] “Cost of a Data Breach Report,” IBM Security, 2022.
[2] IBM Institute for Business Value, 2021.
Why is privacy important for durable goods manufacturing organizations?
Legal Obligations
Failure to comply with privacy laws and regulations can result in serious legal penalties, liability, fines, and other unpleasant consequences.
Customer Trust
Durable goods manufacturing organizations may collect personal information from customers, such as names, addresses, and payment details. It is important to ensure that this information is collected and stored in a way that protects the customer's privacy.
Finances
Data breaches and privacy violations can lead to costly lawsuits, large damages payments, and costly and onerous legal requirements.
Reputation
If a durable goods manufacturing organization experiences a privacy breach, it can lead to negative publicity, loss of customer trust, and reputational damage. This can ultimately lead to a loss of revenue and market share.
Securing Supply Chains
Durable goods manufacturing organizations may need to protect the privacy of their suppliers or partners to prevent supply chain disruptions or breaches.
Embed privacy by design into data lifecycle
Two of the main tasks of personal protection in the higher education section are to identify high-risk personal information categories and embed privacy by design principles into the data lifecycle.

Info-Tech’s privacy program methodology
The image below is a visual overview of Info-Tech’s Privacy Framework. This includes high-level governance items as well as more tactically defined areas.

Insight summary
Overarching insight
As manufacturing technologies and processes evolve, data privacy is a significant risk and must be addressed with a high priority. An integrated privacy program that incorporates privacy principles into business processes will be a cost-effective way to safeguard the journey of business enablement.
Fit privacy to the business
Contextualize privacy for your organization by involving the business units from day one; collect requirements that promote cross-collaboration.
Privacy is dynamic
Structure drives success: take a process-based vs. system-based approach to assess personal data as it flows throughout the organization.
Prioritize and plan together
Review, revise, and reprioritize; come back to the initial risk map created. Draw on areas of alignment between high-value/high-risk processes and their supporting initiatives to properly prioritize.
Make it operational
Be selective with your metrics: choose to implement only metrics that are relevant to your environment. Base your selection on the highlighted areas of focus from the maturity assessment.
Privacy doesn’t live in isolation
By assigning ownership and flexibility to your business units in how they weave privacy into their day-to-day, privacy becomes part of operational design and structure.
A good privacy program takes time
Leverage the iterative process embedded in each phase to prioritize privacy initiatives based on value and risk, and support the rollout through customized metrics.
Info-Tech’s methodology for building a privacy program
1. Collect Privacy Requirements
Phase Action Items
- Define and document drivers
- Establish privacy governance structure
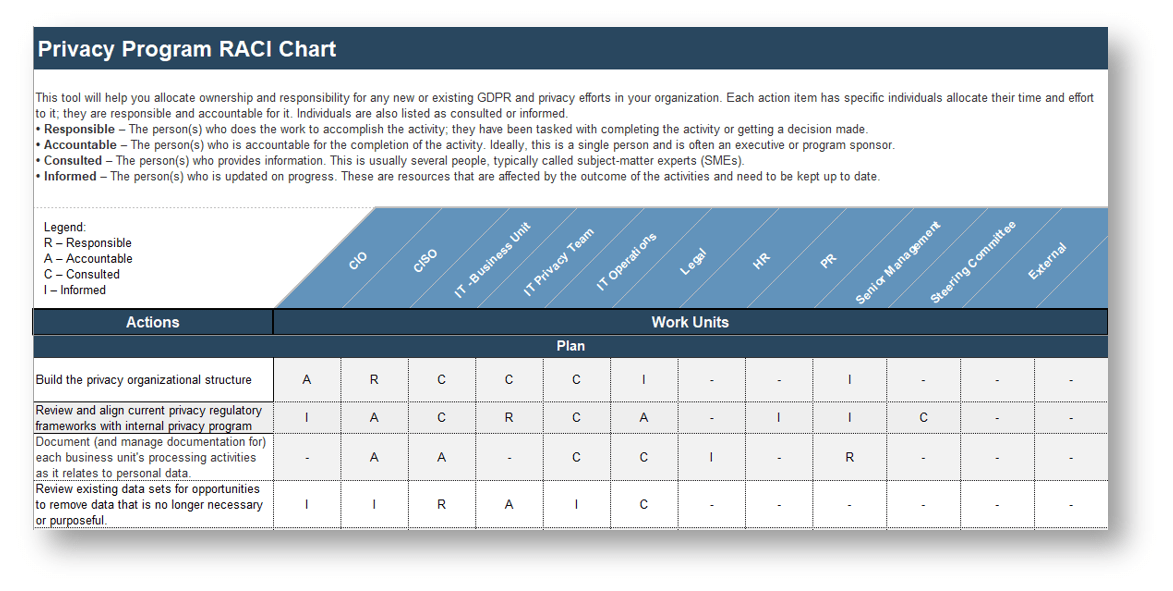
- Build a privacy RACI chart
- Define personal data scope
- Build a risk map
Phase Outcomes
- Documented business and IT drivers for the privacy program
- High-level understanding of how privacy is perceived in the organization
- Completed Data Privacy Program RACI Chart
2. Conduct a Privacy Gap Analysis
Phase Action Items
- Complete the Data Process Mapping Tool
- Compare compliance and regulatory requirements for gap analysis
- Assess and categorize privacy gap initiatives
Phase Outcomes
- Data Process Mapping Tool detailing all business processes that involve personal data
- Privacy maturity ranking (Privacy Framework Tool)
- Identification of compliance or regulatory privacy gaps
3. Build the Privacy Roadmap
Phase Action Items
- Finalize privacy gap initiatives
- Prioritize initiatives based on cost, effort, risk, and business value
- Set firm dates for launch and execution of privacy initiatives
- Assign ownership for initiatives
Phase Outcomes
- Completed Privacy Framework Tool
- Completed privacy roadmap, including timeline for initiative implementation, and cost/benefit vs. value/risk assessment
4. Implement and Operationalize
Phase Action Items
- Establish a set of metrics for the data privacy program
- Operationalize metrics
- Set checkpoints to drive continuous improvement
Phase Outcomes
- Customized set of privacy metrics
- Tasks to operationalize privacy metrics
- Data Privacy Report document
- Performance monitoring scheduled checkpoints
Blueprint deliverables
Each step of this blueprint is accompanied by supporting deliverables to help you accomplish your goals:
|
|
Key deliverable: Privacy Framework/ Business Unit Framework ToolsLeverage best-practice privacy tactics to assess your current organizational privacy maturity while comparing against current privacy frameworks, including GDPR, CCPA, HIPAA, and NIST. Build your gap-closing initiative roadmap and work through cost/effort analysis. |
|
|
Data Privacy Program RACI ChartA high-level list of privacy program initiatives, with assigned ownership to privacy champions from both the business and IT. |
|
|
Data Process Mapping ToolFull documentation of all business processes that leverage personal data within the organization. |
|
|
Data Protection Impact AssessmentWhen highly sensitive data is involved, leverage this tool to assess whether appropriate mitigating measures are in place. |
|
|
Privacy Policy TemplatesInternal and external policies around:
|
|
|
Data Privacy Program ReportA template that highlights the key privacy metrics identified in Phase 4 for the senior leadership team. |
Info-Tech offers various levels of support to best suit your needs
DIY Toolkit
"Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful."
Guided Implementation
"Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track."
Workshop
"We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place."
Consulting
"Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project."
Diagnostics and consistent frameworks are used throughout all four options.
Guided Implementation
A Guided Implementation (GI) is a series of calls with an Info-Tech analyst to help implement our best practices in your organization.
A typical GI is 8 to 12 calls over the course of 4 to 6 months.
What does a typical GI on this topic look like?

Workshop overview
Day 1: Collect Privacy Requirements
Activities
1.1 Define and document program drivers
1.2 Establish privacy governance structure and define scope
1.3 Build the data privacy RACI chart
1.4 Build the risk map
Deliverables
- Business context and drivers behind privacy program
- Data privacy RACI chart
Day 2: Conduct a Privacy Gap Analysis
Activities
2.1 Conduct interviews and complete the Data Process Mapping Tool
2.2 Compare compliance and regulatory requirements with current privacy practices of the organization
2.3 Identify gap areas
2.4 Review data protection impact assessment (DPIA) process and identify whether threshold assessment or full DPIA is required
Deliverables
- Data Process Mapping Tool draft
- Mapped privacy control gap areas to relevant privacy laws, frameworks, or industry standards
- Optional: Walk-through of DPIA tool
Day 3: Build the Privacy Roadmap
Activities
3.1 Complete business unit gap analysis; consolidate inputs from Day 2 interviews
3.2 Apply variables to privacy initiatives
3.3 Create a visual privacy roadmap
3.4 Define and refine the effort map; validate costing and resourcing
Deliverables
- Privacy Framework Tool
- Data privacy roadmap and prioritized set of initiatives
Day 4: Implement and Operationalize
Activities
4.1 Review Info-Tech’s privacy metrics and select relevant metrics for the privacy program
4.2 Operationalize metrics
4.3 Input all outputs from Days 1 to 3 into the Data Privacy Report
4.4 Summarize and build an executive presentation
4.5 Set checkpoints and drive continuous improvement
Deliverables
- Completed data privacy roadmap
- Completed Data Process Mapping Tool
- Review of any outstanding privacy collateral (privacy notice, data protection policy, etc.)
- Data Privacy Program Report document
Day 5: Next Steps and Wrap Up (offsite)
Activities
5.1 Consolidate and schedule any outstanding business unit interviews
5.2 Complete in-progress deliverables from previous four days
5.3 Set up review time for workshop deliverables to discuss next steps
Contact your account representative for more information.
workshops@infotech.com
1-888-670-8889
Phase 1
Collect Privacy Requirements

This phase will walk you through the following:
- Identify the driving forces behind the privacy program
- Understand privacy governance
- Assign ownership of privacy
This phase involves the following participants:
- Privacy officer/privacy team
- Senior management representation (optional)
- Relevant business unit privacy champions
- InfoSec representative
- IT representative
1.1 Define and document the data privacy program drivers
Input: Optional: Ask core team members to brainstorm a list of key privacy program drivers and objectives
Output: Documented list of privacy program drivers, Documented list of privacy objectives, Level-setting on understanding of privacy from core team
Materials: Whiteboard/flip charts, Sticky notes, Pen/marker
Participants: Privacy officer, Senior management team, Core privacy team, InfoSec representative (optional), IT representative (optional)
1 hour
- Bring together relevant stakeholders from the organization. This can include Legal, HR, and Privacy teams, as well as others who handle personal data regularly (Marketing, IT, Sales, etc.).
- Using sticky notes, have each stakeholder write one driver for the privacy program.
- These may vary from concerns about customers to the push of regulatory obligations.
- Collect these and group together similar themes as they arise. Discuss with the group what is being put on the list and clarify any unusual or unclear drivers.
- Determine the priority of the drivers. While they are all undoubtedly important, it will be crucial to understand which are critical to the organization and need to be dealt with right away.
- For most, any obligation relating to an external regulation will become top priority. Noncompliance can result in serious fines and reputational damage as well.
- Review the final priority of the drivers and confirm current status.
Privacy by design is no longer a “nice to have”
Integrate the key principles behind privacy by design to embed privacy in the operations of the organization and minimize business disruption.
- Proactive, not reactive. Preventative, not remedial.
- Privacy as the default setting.
- Privacy embedded into design.
- Full functionality; positive-sum not zero-sum.
- End-to-end security; full lifecycle protection.
- Visibility and transparency; keep it open.
- Respect for user privacy; keep it user-centric.
Get a head start on integrating data protection into the foundations of your projects and processes with Info-Tech's Demonstrate Data Protection by Design for IT research.
Determine the primary owners of the privacy program
The privacy program must include multiple stakeholders for it to be successful. It’s integral to assign clear lines of ownership to build and effectively manage the program. Without defined ownership, privacy initiatives can easily fall between the cracks, and issues may not be handled effectively.
Privacy Department:
- In the most privacy-mature organizations, a dedicated privacy function exists that heads up all privacy initiatives.
- This does involve coordinating with all other relevant departments, but privacy is centrally managed by one group.
Legal, Compliance, Audit:
- In many organizations without a dedicated privacy team, it often falls to Legal, Compliance, and/or Audit to take the privacy mantle.
- Since many privacy programs are being driven by the increase of privacy regulations, these groups often become huge proponents of implementing privacy within the organization.
Human Resources:
- Occasionally the HR department will take on the privacy program.
- This is the case for organizations that do not have a dedicated legal counsel and where most personal data held by the organization is that of the employees.
InfoSec or IT:
- Privacy can also be owned by the security team. Many still think of security and privacy as being the same thing, and it is not uncommon to conflate these two functions into one team.
- However, it is worth noting again that these two are different and many privacy initiatives go beyond security controls.
Info-Tech Insight
If not already mandated by governing privacy laws, consider appointing a privacy officer to formalize privacy ownership in the organization.