- Higher education institutions have increased pressure in ensuring personal data protection for students and faculties in the new digital era, especially protecting sensitive information such as health data, biometrics data, etc.
- Privacy teams are having a difficult time conveying the legal obligations and privacy protection principles and providing actionable guidance to business partners.
- One institution may have more than one IT department. Decentralized and fractional systems lead to inconsistent policies and procedures.
Our Advice
Critical Insight
- Students are wary of privacy risks and value privacy protections. So should the leaders at the education institutions. Embed privacy-by-design principles into your business processes and data lifecycle to protect valuable personal data for students and faculty.
Impact and Result
- Establish a holistic and integrated privacy program that embeds privacy by design principles into the business processes.
- Partner with business departments by speaking a language it can understand and providing tools it can implement.
- Gain the visibility of personal data processing activities and prioritize personal data protection initiatives.
- Create privacy policies, standards and procedures that are established with respect to how information is collected, processed, shared, and protected within the data lifecycle.
Build Business-Aligned Privacy Programs for Higher Education Institutions
Embed privacy by design into your business processes and protect high-risk personal data.
EXECUTIVE BRIEF
Analyst Perspective
Students are wary of privacy risks and value privacy protections. So should the leaders at education institutions.
|
College students are living in environments that increasingly require regular interaction with information technology and data. Students are aware of data protection risks and take privacy seriously. Some personal identifiers, such as email addresses, can be easily replaced. But biometric information such as fingerprints and facial geometry scans are unique. Students' strong belief in the protection of sensitive personal information stems from a desire to protect themselves from privacy risks and harm that may last for the rest of their lives. With a veritable explosion of data breaches highlighted almost daily across the globe, and the introduction of heavy-handed privacy laws and regulatory frameworks, privacy has taken center stage. Students care about their data privacy, and this concern is increasing. This leaves leaders in the education section questioning what exactly privacy involves and how to make it scalable for their respective institutes. As the general public begins to take back control over data privacy, so too should education institutions by taking a tactical, measurable approach to privacy and the business. Alan Tang |
Executive Summary
Your Challenge |
Common Obstacles |
Info-Tech’s Approach |
|---|---|---|
|
|
|
Info-Tech Insight
Students are wary of privacy risks and value privacy protections. So should the leaders at education institutions. Privacy-by-design principles should be embedded into the business processes and data lifecycle to protect the valuable personal data of students and faculty.
Relevant Legal Obligations and Guidelines
More than 130 countries had put in place legislation to secure the protection of data and privacy
Info-Tech Insight
Higher education institutions increasingly depend on online platforms related to student learning, advising, and management in order to optimize processes and deliver student services at scale. The importance of privacy and data protection is increasingly recognized. Equally concerned is the collection, use and disclosure of personal information to third parties without prior notice or consent from students and faculties.
Typical Business Processes of a Higher Education Institution
Usually, there are three types of business processes supporting the operations of a higher education institution: defining processes, shared processes and enabling processes.
Defining Capabilities
- Recruitment (Undergrad, Graduate Studies)
- Admission (Undergrad, Graduate)
- Student Enrollment (Enrollment, Financial Aid)
- Instruction & Research (Teaching & Learning, Research)
- Graduation (Graduation, Transcripts)
- Advancement (Alumni Relations, Fundraising)
Shared Capabilities
- Student Administration (Student progression, Record maintenance)
- Student Support Services (Athletics, Career Development)
- Academic Admin (Academic Year Scheduling, Policy Admin)
Enabling Capabilities
- Facilities & Property Mgmt.
- Finance Mgmt.
- Human Resources
- IT
- Legal Services
- Government, Public, and Stakeholders
- Governance, Risk, and Compliance
Privacy is all about personal data
When building a privacy program, focus on all personal data, whether it’s publicly available or private. This includes defining how the data is processed, creating notices and capturing consent, and protecting the data itself. Conversely, an effective privacy program allows access to information based on regulatory guidance and appropriate measures.
Examples of personal data include:
Traditional PII: Personally identifiable information |
Personal Data: Any information relating to an identified or identifiable person |
Sensitive Personal Data: Special categories of personal data (some regulations, like GDPR, expand their scope to include these) |
Full name (if not common) |
Enrollment status |
Biometrics data: Retinal scans, voice signatures, or facial geometry |
Home address |
Grade level |
Health information: Patient identification number or health records |
Date of birth |
Dates of attendance |
Political opinions |
Social security number |
Degrees, honors, and awards received |
Trade union membership |
Banking information |
Location data |
Sexual orientation and/or gender identity |
Passport number |
Photograph |
Religious and/or philosophical beliefs |
Etc. |
Etc. |
Ethnic origin and/or race |
Privacy and Security Are Among the Top Concerns
Privacy and cybersecurity together are the #2 issue education institutions will be facing in 2023 based on EDUCAUSE’s recent report “Top 10 IT Issues, 2023: Foundation Models.”

Source: EDUCAUSE, 2022.
Privacy Policies Are Not Fully Understood
ECAR's 2019 survey of US students found that less than half of them believed they benefited from their institution's privacy and security policies, and even fewer students reported understanding how their institution used their personal data. *
 |
*ECAR, 2019.
Transparency and Communication Are Key
Case Study:
In March 2020, in response to a proposal to adopt facial recognition for security surveillance at UCLA, students from 36 campuses protested, in person and via online petitions, against the use of facial recognition systems. The pushback from students and the community led UCLA and about 50 other colleges and universities to promise not to use facial recognition technology on their campuses.*
*Kari Paul, "'Ban This Technology': Students Protest US Universities' Use of Facial Recognition," The Guardian, March 2, 2020.
Info-Tech Insight
To foster trust and cooperation, higher education institutions should communicate how and why they collect and use students' personal information.
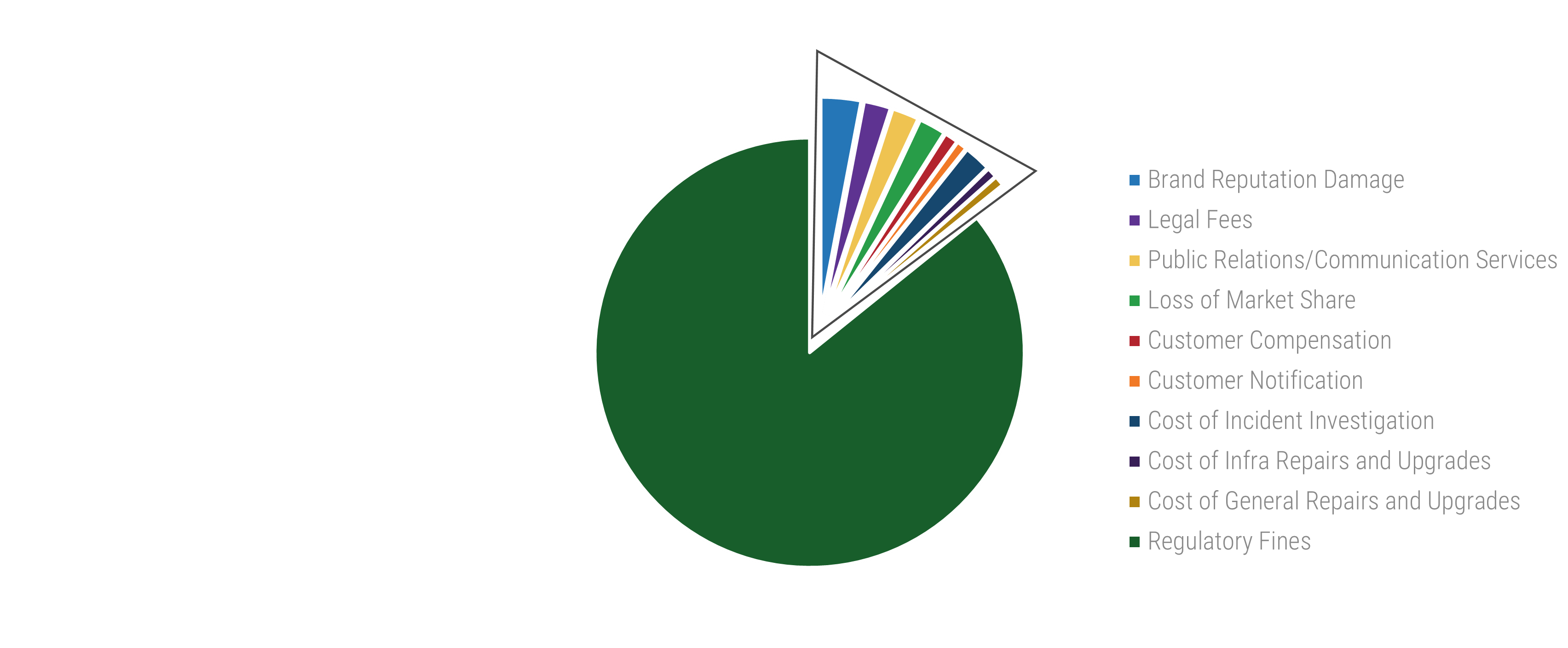
True Cost of a Data Breach
An industry outlook
Even with a robust privacy program in place, organizations are still susceptible to a data breach. The benefit comes from reducing your risk of regulatory compliance issues and resulting fines and minimizing overall exposure.
86% of data breach costs are associated with REGULATORY fines
Healthcare* |
Government |
Financial Services |
Education |
Estimated Cost of Exposure: $841.41 |
Estimated Cost of Exposure: $114.75 |
Estimated Cost of Exposure: $188.05 |
Estimated Cost of Exposure: $207.75 |


