Many organizations are behind on developing effective IT controls, held back by the lack of specialized knowledge, time, and resources, and other barriers to overcoming the inherent complexity of the task. IT and risk leaders must take a step-by-step approach to these challenges, in order to counter risks, avoid breaches, and maintain compliance, while safeguarding their operations and reputation.
1. Know and counter the IT risks that matter most.
Taking a structured risk-first approach to developing and managing IT controls will deliver the most effective risk mitigation results at the lowest cost to the organization, optimizing the deployment of risk specialists and resources.
2. Don’t ignore your end users.
Your organization’s end users will be ultimately responsible for the IT risk controls framework you build. You must ensure their involvement in the development of those controls, rather than designing them in isolation.
3. Make monitoring and reporting integral to your system.
Effective IT controls management is not a matter of building a system and then leaving it to operate on its own. Monitoring and reporting must be integral parts of your IT controls. Neglecting that aspect of your framework leaves you vulnerable to undetected breaches, compliance gaps, and inefficiencies, which could result in severe damage to your organization’s operations and reputation.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
10.0/10
Overall Impact
$13,700
Average $ Saved
5
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
City Of Charlotte
Guided Implementation
10/10
$13,700
5

IT Controls and Assurance
All of our Info-Tech Academy courses have closed captioning available. To turn this function on, click on the C.C. in the bottom right corner of the video screen and click "English" on the options that pop-up.
- Course Modules: 5
- Estimated Completion Time: 1.5 hours
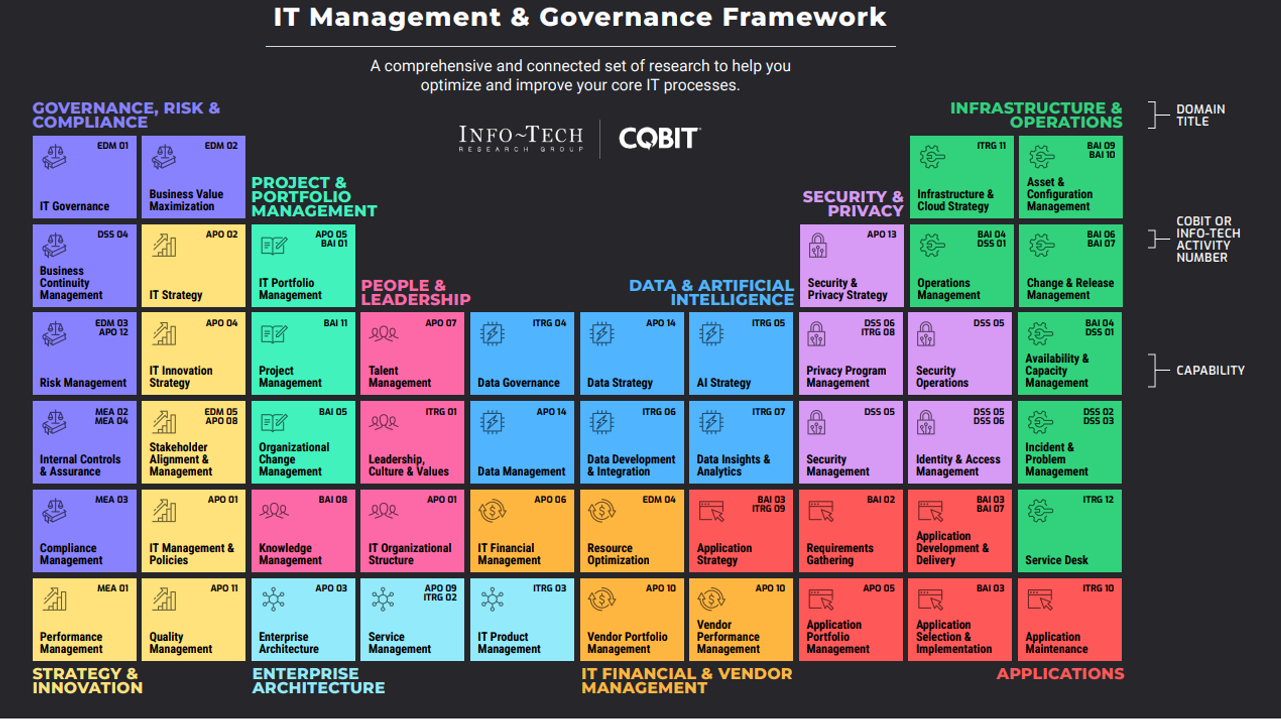
Build an Effective IT Controls Register
Confidently counter IT risks that matter.
Analyst perspective
Confidently counter IT risks that matter.
"If you think compliance is expensive, try non-compliance"
– former US Deputy Attorney General Paul McNulty, as quoted in Insurance Business, 2025
In today's volatile environment, with rapid technological, geopolitical, and regulatory changes defining the landscape, you would think that most IT organizations would have a highly mature IT risk and controls management to counter new technological risks as well as other high severity risks. Surprisingly it is not so, and most organizations can best be defined as weak in terms of their IT controls management!
Several barriers, such as the inherent complexity of developing controls, lack of specialized knowledge, lack of time/resources, and an inability to keep pace with environmental changes, have led to this state. Several technology and risk leaders lament, "if only we had a step-by-step logical framework to set up our IT controls management; this is too difficult; and I do not have the time!"
Well, we heard you there and produced this blueprint! This blueprint will help you develop a comprehensive IT controls register through a structured, risk-first, and data-driven approach to controls management, which is essential for enhancing risk and productivity outcomes. It outlines a phased methodology, starting with assessing risk management maturity, defining control goals, evaluating current controls, identifying gaps, developing new controls, and establishing a monitoring and reporting plan. This approach also highlights the importance of involving end users in control design and ensuring controls are not overly stringent or duplicative. By following this blueprint, organizations can confidently counter IT risks, avoid significant breaches, and maintain compliance, ultimately safeguarding their operations and reputation.

Anubhav (Anu) Sharma
Research Director, CIO Advisory Practice
Info-Tech Research Group
Build an Effective IT Controls Register
Confidently counter IT risks that matter.
EXECUTIVE BRIEF
Executive summary
Your Challenge
IT/risk leaders need a controls capability that helps them to identify their greatest risks and enhance the effectiveness of their internal IT controls while keeping them in line with rapidly evolving regulations as well as the technological environment.
Deficiencies in controls could result in serious breaches for an organization or, worse, cost IT/risk leaders their jobs.
Despite these drastic consequences, the system of internal controls at most organizations can, at best, be defined as weak.
Common Obstacles
Numerous barriers exist to building strong IT controls:
- Inherent complexity: IT environments can be complex, with a wide range of IT controls that are to be developed and tested cross-functionally across the organization. This can make controls management time-consuming and challenging.
- Resource and time constraints: Assessing and developing controls can require significant resources, including personnel, time, and specialized knowledge and tools.
- Inconsistent approaches: Inconsistent approaches to controls management can add to the complexity and reduce productivity.
- Evolving regulations: Regulations keep changing and it is hard to keep your IT controls in sync with them.
- Environmental changes: Nature of technology risk is evolving. Risks from AI tend to be more difficult to predict and develop controls for.
Info-Tech's Approach
Our approach helps provide a structured and actionable framework to assess, develop, and manage IT controls that will address your greatest IT risks in a comprehensive, risk-first, and data-driven manner.
- Phase 1: Define your goals and map current controls
- Phase 2: Evaluate current controls and build new controls
- Phase 3: Develop controls monitoring and reporting plan
This approach will lead to enhanced risk and productivity outcomes which are critical in a complex and rapidly evolving regulatory and technological environment.
It sets the base for you to comply with needed regulations as well as implement governance, risk, and compliance (GRC) tools and start optimally leveraging AI and other embedded technologies.
In addition, by reducing massive failure risk, our approach helps you keep your job!
Info-Tech Insight
Organizations are increasingly transitioning to a risk-based approach to controls management as just a compliance-based approach can prove to be too myopic in the era of exponential risk. It makes sense that with limited time and resources at your disposal, you first tackle your greatest risks in a structured and organized manner.
What is an IT control?
An internal control is an organization's mechanism to ensure the objective of a process is achieved.
IT controls are a subset of an organization's internal controls and are defined as activities performed by persons or systems to ensure that computer systems operate in a way that minimizes risk.
IT control objectives typically relate to assuring the confidentiality, integrity, and availability of data and the overall management of the IT function.
IT controls are often described in two categories: IT general controls (ITGC) and IT application controls.
ITGC includes controls over the hardware, system software, operational processes, access to programs and data, program development, and program changes.
IT application controls refer to controls to ensure the integrity of the information processed by the IT environment. Both tend to have broader implications across the organization and are cross-functional in their operating nature.
Examples of controls in daily life
- Seatbelts
- Door locks
- ATM Pins (keep separate)
- Bank account review and reconciliation
Your challenge
IT/risk leaders need a controls capability that helps them to identify their greatest risks and enhance the effectiveness of their internal IT controls while keeping them in line with rapidly evolving regulations as well as the technological environment.
- Deficiencies in controls could result in serious breaches for an organization or, worse, cost IT/risk leaders their jobs.
- Despite these drastic consequences, the system of internal controls at most organizations can, at best, be defined as weak.
- Lower controls maturity has been seen to result in lower five-year share price for organizations; hence, it has an impact on organizational objectives.
- Noncompliance costs are significantly higher than costs of strong compliance, thus there is no excuse not to invest in a good controls program.
Low average controls maturity
9% |
Only 9% have a strong risk and controls culture within the organization. |
39% |
Only 39% of respondents have an advanced or matured controls framework. |
Source: Deloitte, 2024
Why it matters
50% |
50% average five-year share price improvement for companies with high/very high controls maturity vs. 5% for those with low/medium maturity. |
Source: Deloitte Future of Controls, 2024
2.71x: |
Noncompliance costs 2.71x the cost of compliance. |
Source: Ponemon Institute, 2011
There are several obstacles for an organization looking to evolve their IT controls management
1 |
Inherent complexity: IT environments can be complex, with a wide range of IT controls that are to be developed and tested cross-functionally across the organization. This can make controls management time-consuming and challenging. |
2 |
Resource and time constraints: Assessing and developing controls can require significant resources, including personnel, time, and specialized knowledge and tools. |
3 |
Inconsistent approaches: Inconsistent approaches to controls management can add to the complexity and reduce productivity. |
4 |
Evolving regulations: Regulations keep changing and it is hard to keep your IT controls in sync with them. |
5 |
Environmental changes: Nature of technology risk is evolving. Risks from AI tend to be more difficult to predict and develop controls for. |
6 |
Only compliance viewpoint: Myopic view of risk and controls from a compliance standpoint and not a risk-based standpoint can leave the organization vulnerable to emerging technology risks. |
Info-Tech's approach to building your IT controls register
Pre-Phase |
Phase 1 |
Phase 2 |
Phase 3 |
|
Activities |
Assess Risk Management Maturity and Need for Controls |
Define Your Goals and Map Current Controls |
Evaluate Current Controls and Build New Controls |
Develop Monitoring and Reporting Plan |
|
|
|
|
|
Inputs |
|
|
|
|
Outputs |
|
|
|
|
Info-Tech Insight
All outputs can be captured in the IT Controls Register template provided with this blueprint or can be updated in your original risk and controls repository (e.g. in your organization's GRC tool).
Insight summary
An IT controls register helps confidently counter the IT risks that matter.
Having a structured risk-first and data-driven approach to identifying and managing IT controls will lead to the best risk mitigation results at the lowest cost to the organization, optimizing the usage of limited risk personnel and resources.
A robust controls taxonomy enables better controls management through:
- Consolidation and shared controls language.
- Reporting on controls at different aggregate levels.
- Benchmarking and comparison.
- Identifying gaps in your controls management.
Controls effectiveness evaluation should be based on multiple factors.
It is not just enough to evaluate controls only from a design point of view. Make sure to also factor in implementation quality, feasibility, user feedback, as well as audit/self-assessment findings.
IT controls monitoring and reporting plans will help in proactive management of risks.
Without monitoring and reporting, organizations remain vulnerable to undetected breaches, compliance gaps, and inefficiencies which could potentially result in severe damage.
Having a risk framework/risk register is a prerequisite.
Before we deep dive into internal IT controls, it is important that you have first defined your risk framework/register as controls management is a subsequent step.
Involve end/business users in controls design.
It is important that controls are not designed in isolation and that their development has the involvement of the end/business users since they are responsible for them.
Blueprint deliverables
Each step of this blueprint is accompanied by supporting deliverables to help you accomplish your goals.
- Risk Management Checklist
- Goals & Outcomes Template
- Likelihood and Impact Scales
- Risk Register
- Controls Register
- Controls Effectiveness Checklist
- Risk Taxonomy
- Controls Taxonomy
- Monitoring Plan Template
- Reporting Plan Template
Key deliverable:
IT Controls Register
Excel document which maps controls to the greatest risks, evaluates their effectiveness, defines new controls, and has a defined monitoring and reporting plan.
Blueprint benefits
IT Benefits |
Business Benefits |
|
|
Track the outcome measures developed in Phase 1, Step 1.1 to track the organizational benefits you receive from actioning this blueprint.
Measure the value of this blueprint
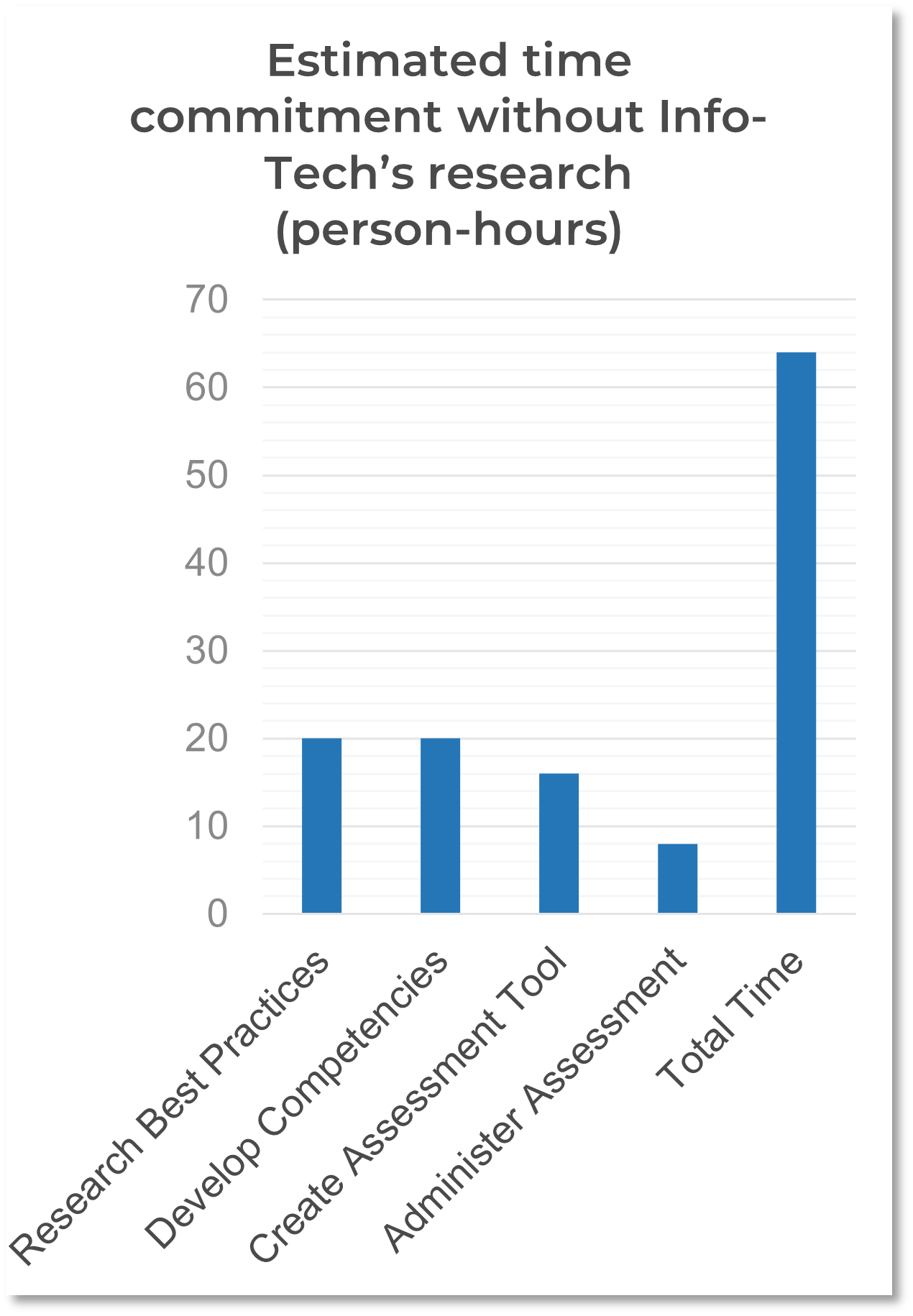
Most organizations will need to spend a lot of money and resources in creating an IT controls register if they do not use Info-Tech's resources.
Based on similar efforts, we estimate that most organizations would take months to prepare an IT controls register without our resources. That's nearly 65 hours per person multiplied by the number of people involved in researching and gathering data to support due diligence, for a total cost of thousands of dollars. Improve your success rate and reduce your effort by using Info-Tech's methodology developed through the combined insights of seasoned Info-Tech experts.
Value of this blueprint = Reduced effort and cost to develop an IT controls register by following this blueprint methodology versus developing a similar document without Info-Tech's methodology and resources.
Case Example
INDUSTRY: Technology
TYPE: Semiconductor Manufacturer
Acme Inc. develops their IT controls register to counter their greatest risks.
Acme Inc. is a global semiconductor manufacturer specializing in advanced sensor technologies. The company has grown to become a key supplier to major automotive original equipment manufacturers (OEMs) worldwide.
Annual Revenue: $500 million
Employees: 1500
Manufacturing Facilities: US, Canada, UK, China
The company has a complex global supply chain, highly automated production lines, and a just-in-time manufacturing model.
It is connected by a global ERP system, cloud-based lifecycle management, and real-time order tracking portal for customers.
It has a high-pressure delivery schedule and has to undergo strict quality control requirements and technology audits from customers as well as its auditors. In addition, it has complex intellectual property which it needs to protect.
Currently, it is looking to digitally transform its technology in the midst of rising technology regulatory requirements, the need to protect intellectual property amongst growing cyberthreats in the semiconductor industry, and uncertainty in the global supply chain.
The CIO along with the CRO want to ensure that they are countering the greatest IT risks and want to do a comprehensive risk assessment and IT controls register development to be confident in their organizational resilience. CIO does have a risk register but needs more structure to do this well and has limited resources and time, but she also understands that with AI and other exponential technologies used by threat actors, having effective IT controls is essential.
Let us follow their journey throughout this blueprint through each phase.
Follow Acme Inc.'s IT controls register journey throughout this blueprint:
- Pre-Phase: Identification of greatest IT risks
- Phase 1: Developing goals, outcomes, and mapping controls
- Phase 2: Evaluating controls and developing new controls
- Phase 3: Developing a monitoring and reporting plan
Info-Tech offers various levels of support to best suit your needs
DIY Toolkit
“Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful.”
Guided Implementation
“Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track.”
Workshop
“We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place.”
Consulting
“Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project.”
Diagnostics and consistent frameworks used throughout all four options
Guided Implementation
What does a typical GI on this topic look like?
A Guided Implementation (GI) is a series of calls with an Info-Tech analyst to help implement our best practices in your organization.
A typical GI is 8 to 12 calls over the course of 3 to 4 months.
Workshop Overview
Contact your account representative for more information.
workshops@infotech.com 1-888-670-8889
Pre-Work | Day 1 | Day 2 | Day 3 | Day 4 | Day 5 | |
Activities | Assess risk management maturity and need for controls | Define control objectives and map current controls | Map current controls (cont'd.) and evaluate control effectiveness | Develop/design controls cont'd. | Develop monitoring and reporting plan | Next steps and |
0.1 Use a risk management assessment checklist to validate whether we have the prerequisites for working on the IT controls blueprint. 0.2 Identify your greatest or potentially most impactful risks based on risk scores (likelihood, impact). 0.3 Identify focus areas and people for possible workshop (e.g. IT, audit, and business folks) on controls. | 1.1 Introduce the workshop agenda and objectives. 1.2 Define your goals and outcome measures for implementing controls management. 1.3 Build your control taxonomy and map to your risk taxonomy (can either follow example from Info-Tech or use whatever you already have). 1.4 Baseline current controls vs. greatest identified risks via the classification of preventative, detective, and corrective controls. | 2.1 Baseline current controls vs. greatest identified risks via the classification of preventative, detective, and corrective controls. 2.2 Use the factors that Info-Tech has provided and finalize the factors that you will use for your controls evaluation. 2.3 Execute controls evaluation utilizing the Info-Tech template. | 3.1 Execute controls evaluation utilizing the Info-Tech template (cont'd.). 3.2 Develop/design new/modified controls for a pre-identified focus area with the understanding that similar processes will be adopted for other focus areas outside the workshop. | 4.1 Develop monitoring plan. 4.2 Develop reporting plan. 4.3 Transfer new information to your original risk and controls repository. | 5.1 Complete in-progress deliverables from previous four days. 5.2 Set up review time for workshop deliverables and to discuss next steps. | |
Deliverables |
|
|
|
|
|
|
Pre-Phase
Assess Risk Management Maturity and Need for Controls
Pre-Phase |
Phase 1 |
Phase 2 |
Phase 3 |
|---|---|---|---|
0.1 Check completeness of prerequisites 0.2 Identify your greatest risks |
1.1 Define your goals and outcome measures 1.2 Build your control taxonomy 1.3 Map your existing controls |
2.1 Finalize your controls evaluation framework and gather relevant data 2.2 Execute the controls evaluation 2.3 Design new/modified controls |
3.1 Establish monitoring plan 3.2 Establish reporting plan 3.3 Finalize IT controls register and transfer to original repository |
This phase will get you the following outcomes:
- Completed assessment checklist
- List of your greatest or potentially most impactful risks identified
- (Optional) List of focus areas and workshop participants
This phase involves the following participants:
- IT/risk leader, focus area business stakeholder
Risk management and controls are two sides of the same coin
Good risk management involves identifying the greatest risks facing the organization and then designing and implementing effective controls to mitigate the impact of those risks.
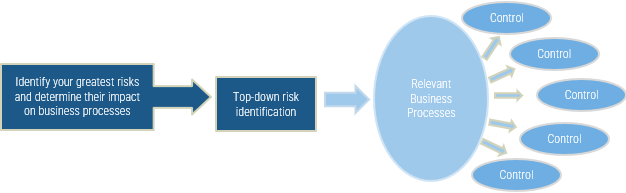
A prerequisite to working on controls is to first be able to identify your greatest risks and document these in a repository such as a risk register. Then focus on mapping, evaluating, and designing controls which help to mitigate these risks.
This approach will help focus your efforts on getting maximum value from minimum resource utilization.

 Optimize IT Governance for Dynamic Decision-Making
Optimize IT Governance for Dynamic Decision-Making
 Maximize Business Value From IT Through Benefits Realization
Maximize Business Value From IT Through Benefits Realization
 Build an IT Risk Management Program
Build an IT Risk Management Program
 Review and Improve Your IT Policy Library
Review and Improve Your IT Policy Library
 Establish a Sustainable ESG Reporting Program
Establish a Sustainable ESG Reporting Program
 Take Control of Compliance Improvement to Conquer Every Audit
Take Control of Compliance Improvement to Conquer Every Audit
 Build an Effective IT Controls Register
Build an Effective IT Controls Register
 Integrate IT Risk Into Enterprise Risk
Integrate IT Risk Into Enterprise Risk
 The ESG Imperative and Its Impact on Organizations
The ESG Imperative and Its Impact on Organizations
 Make Your IT Governance Adaptable
Make Your IT Governance Adaptable
 Build an IT Risk Taxonomy
Build an IT Risk Taxonomy
 Prepare for AI Regulation
Prepare for AI Regulation
 Building the Road to Governing Digital Intelligence
Building the Road to Governing Digital Intelligence