Sample Report
Info-Tech’s Security Governance and Management Maturity Scorecard is designed to apply to all organizations, regardless of size or industry. Download a preview of the report to see the value it can bring to your organization.
Governance and management are a major part of getting security right. How do you measure up?
Without the right policies and processes in place and enforced, no organization is truly secure. Info-Tech’s Security Governance and Management scorecard lets you measure your performance against industry standard best practices. Use this report to understand your current strengths and weaknesses, then follow Info-Tech’s customized roadmap of practical and prioritized action items to improve and optimize your security governance and management.

Chart your course to security success. These reports consolidate the customized action items arising from your security governance and management scores, and present this information in a unified and prioritized format to guide your next steps.
Share end user satisfaction and importance ratings of core IT services, IT communications and business enablement to focus on the right end user groups or lines of business, and ramp up satisfaction and productivity.
Understand your scores on an in-depth level for each security governance and management area:
Understand your scores for each policy and process governance area:
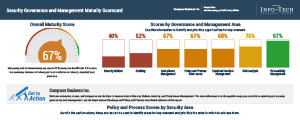
Info-Tech’s Security Governance and Management Maturity Scorecard is designed to apply to all organizations, regardless of size or industry. Download a preview of the report to see the value it can bring to your organization.

Preview a sample of Info-Tech’s Security Governance and Management Maturity Scorecard survey. This 60 question survey should be completed by your organization’s Chief Security Officer or equivalent, and is designed to be quick and user friendly.